Cybercriminals have been coercing YouTube creators into distributing malware by threatening them with channel takedowns over fraudulent copyright claims.
According to a Kaspersky report, attackers targeted content creators who posted videos on bypassing internet restrictions, forcing them to share links to malware-infected files disguised as legitimate tools. The campaign, which has primarily impacted Russian users, relies on a mix of social engineering, deception, and outright extortion to spread the SilentCryptoMiner malware.
Unusual malware campaign uncovered
Kaspersky researchers identified the campaign while analyzing the growing abuse of Windows Packet Divert, a legitimate driver used for intercepting and modifying network traffic. Over the past six months, Kaspersky’s telemetry has recorded more than 2.4 million detections of this technology on user devices. While typically used for legal purposes, cybercriminals have exploited it as a delivery method for malware, including stealers, remote access Trojans (RATs), and cryptocurrency miners like SilentCryptoMiner.

Kaspersky
The malware was initially spread via a YouTube channel with 60,000 subscribers, where the creator uploaded tutorial videos about bypassing internet restrictions. The description of these videos contained links to a malicious file hosted on gitrok[.]com, which was downloaded over 40,000 times before the link was removed. The videos themselves accumulated more than 400,000 views.
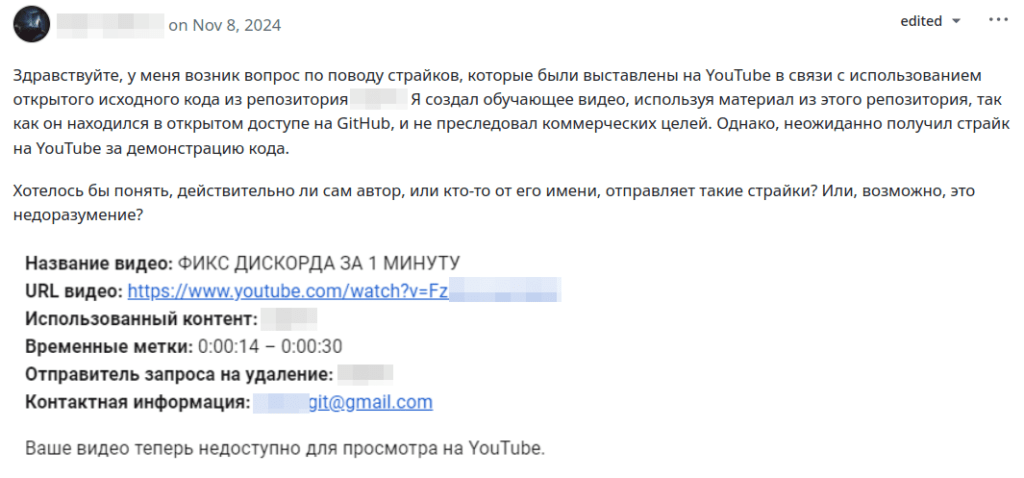
However, beyond deception, attackers resorted to blackmail to further distribute the malware. They filed fraudulent copyright strikes against YouTubers who shared legitimate restriction bypass tools. Posing as developers of the original tool, they then contacted these creators, threatening them with permanent channel bans unless they replaced their video descriptions with links to infected files. This tactic forced YouTubers into unwittingly promoting the malware out of fear of losing their channels.
Kaspersky
Malware infection chain
The infected files were distributed in archives containing a modified general.bat script, which launched a second-stage loader written in Python and packed with PyInstaller. In some cases, PyArmor was used for additional obfuscation.
The malware followed a multi-stage execution process:
- The Python loader retrieved a second-stage payload from hardcoded URLs (canvas[.]pet, swapme[.]fun), but only if accessed from a Russian IP address.
- The next-stage loader scanned the environment to detect virtual machines and sandboxes, attempting to evade security analysis.
- It then disabled security protections by adding the AppData directory to Microsoft Defender exclusions.
- The malware downloaded an executable (di.exe), increased its size to 690 MB by appending random data (to bypass antivirus detection), and gained persistence by registering as a Windows service (DrvSvc), masquerading as a legitimate system process.
The final payload, di.exe, was identified as SilentCryptoMiner, a stealthy malware based on XMRig. This miner is capable of mining multiple cryptocurrencies, including Monero (XMR) and Raptoreum (RTM).
To avoid detection, SilentCryptoMiner injects itself into the legitimate Windows process dwm.exe using process hollowing. Next, it monitors active processes to suspend mining when security-related programs (Taskmgr.exe, ProcessHacker.exe, procexp.exe) run. Finally, it uses encrypted configurations stored on Pastebin and updated every 100 minutes via remote servers.
The attackers also employed anti-analysis techniques, such as bloating the executable’s size to 680–800 MB in size, ensuring it won’t run on security sandbox environments.
YouTube users beware
This campaign highlights a dangerous shift in cybercriminal tactics, where attackers don’t just deceive users into downloading malware but actively blackmail content creators into spreading it. While this attack focused on cryptojacking, similar methods could be used to steal credentials, deploy spyware, or even launch ransomware attacks.
To defend against such threats, users should never trust YouTube channels blindly, especially smaller and mid-tier channels that provide niche tech tips. Creators themselves should verify copyright claims before complying with takedown notices, as scammers exploit this system for blackmail. If a cybercriminal approaches you, it would be better to report it to YouTube’s abuse team rather than complying with any demands.







Leave a Reply