
Significant privacy vulnerabilities in WhatsApp's device identification mechanisms allow attackers to fingerprint the operating systems of users' devices through WhatsApp's End-to-End Encryption (E2EE) protocol. Discovered by security researcher Tal Be'ery, the flaws expose information about users' devices that could aid attackers in their reconnaissance efforts.
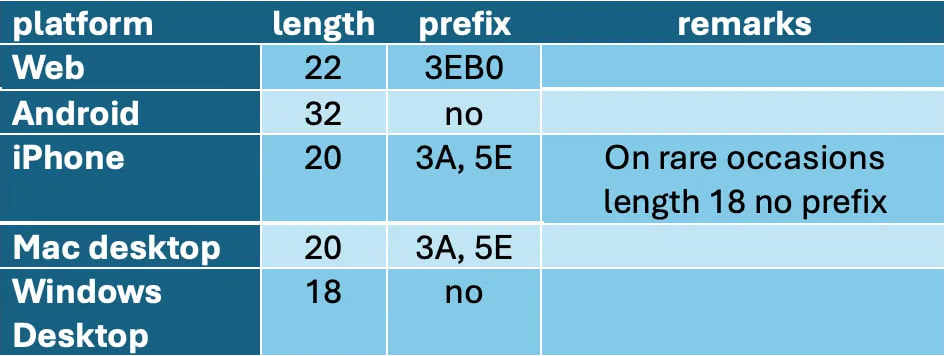
The privacy issues stem from WhatsApp's multi-device E2EE protocol, which is based on Signal's Sesame protocol. In this multi-device setup, a sender must establish a secure session with each of a recipient's devices. However, this design also unintentionally leaks details about the recipient's devices, such as how many devices they are using, whether the device is mobile or desktop, and a long-term identifier for each device. These identifiers allow persistent tracking of the devices, even after a user blocks another on the platform.
While this information leakage is problematic on its own, Be'ery's research has uncovered that attackers can also deduce more specific details, such as the operating system used on each device. This opens the door for more targeted attacks by allowing adversaries to exploit OS-specific vulnerabilities. For example, attackers can identify whether a victim is using an Android, iOS, Mac, or Windows device, and use this information to tailor their attack, targeting the device with the most vulnerabilities.
Tal Be'ery
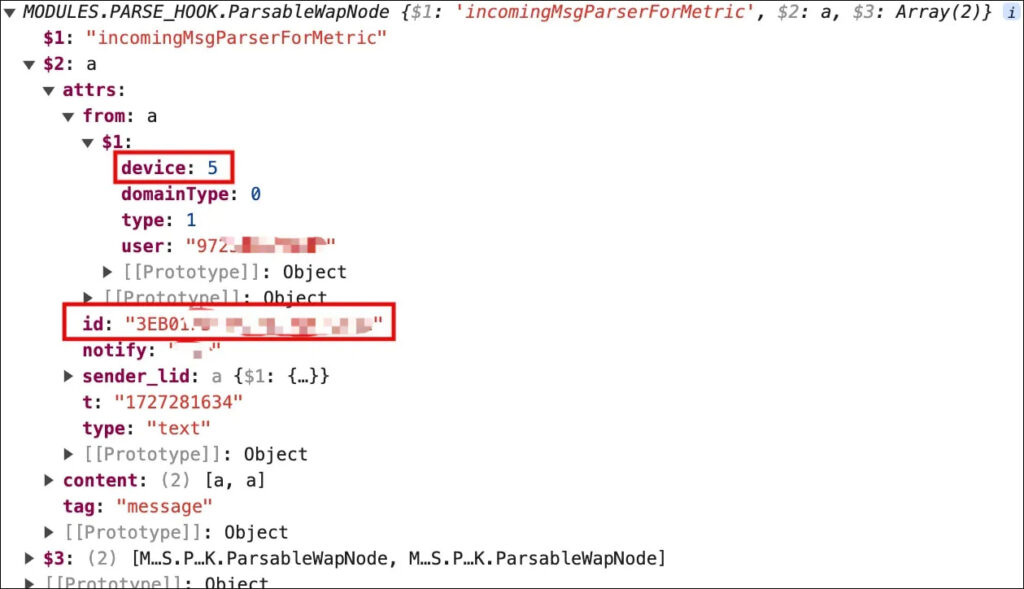
WhatsApp, owned by Meta, boasts over 2.4 billion active users globally, making these privacy issues potentially impactful on a massive scale. Be'ery's initial discovery came earlier this year, and his recent findings indicate the problem is even worse than initially thought. By examining features like the “View Once Media” function and the message ID structure, Be'ery was able to refine his analysis, showing that WhatsApp messages include OS-specific identifiers. This means attackers could determine not only the device type but also the operating system in use, such as distinguishing between a Mac and an iPhone or Android versus a desktop.
Tal Be'ery
The implications of these vulnerabilities are not extremely serious, but attackers can still leverage them as part of sophisticated attack chains to identify and exploit the weakest link in a victim's device ecosystem. Even non-technical attackers, such as individuals engaging in domestic spying, could exploit these data leaks to gain insights into their victim's device setup.
Be'ery disclosed the issue to Meta on September 17, 2024, but has received only a partial response. Meta's security team acknowledged the report, but no comprehensive fix has been released. Given the widespread exploitation of WhatsApp's vulnerabilities through tools like WhatsApp Web extensions, Be'ery decided to publish his findings after a month of silence from Meta. The researcher believes that addressing the issue could be as simple as standardizing the message ID generation across platforms to eliminate the fingerprinting vector.
For users concerned about these vulnerabilities, there are a few steps they can take to protect themselves:
- Be cautious of the number of devices linked to your WhatsApp account, especially desktop clients.
- Consider limiting the use of WhatsApp Web or desktop applications if possible.
- Monitor any unusual activity on your WhatsApp account, such as messages marked as read on devices you are not using.
CyberInsider contacted WhatsApp for a comment on Be'ery's report, and a spokesperson sent us the following comment:
“We appreciate the researcher’s submission. We remain focused on protecting our users against many different vectors of attack while still ensuring we can smoothly run a service that over 2 billion people use around the world.” – WhatsApp spokesperson







Leave a Reply