
A team of Austrian and German researchers has uncovered critical vulnerabilities in WhatsApp's implementation of the Signal protocol that could allow adversaries to degrade forward secrecy, track device usage, fingerprint users, and even block new conversations altogether.
Their paper, titled Prekey Pogo, reveals a new class of stealthy and impactful attacks targeting the app's prekey mechanism, a core component of secure session initialization.
WhatsApp, a Meta-owned service boasting over 3 billion users globally, uses its own fork of the Signal protocol. Despite Signal's strong reputation for security, the researchers argue that real-world implementations remain vulnerable without active auditing. To test their theory, the researchers developed a custom client based on reverse-engineered community projects like WhatsMeow, Baileys, and Cobalt. These tools enabled them to simulate realistic attacks across various WhatsApp clients — Android, iOS, desktop apps, and web interfaces.
WhatsApp's flawed prekeys implementation
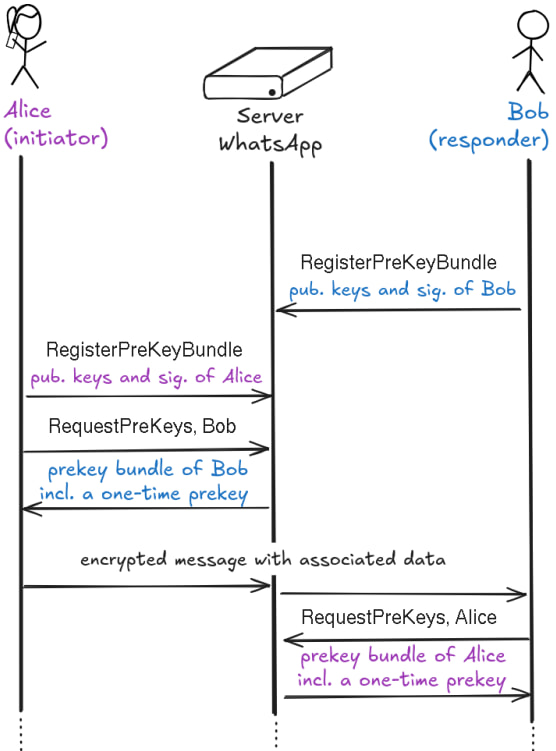
The study centers on a targeted abuse of WhatsApp's handling of ephemeral prekeys. These one-time-use cryptographic keys are essential for ensuring that even if long-term encryption keys are later compromised, past messages remain secure — a property known as Perfect Forward Secrecy (PFS). While this mechanism has long been part of Signal's X3DH protocol, the authors are the first to demonstrate a viable attack against it within WhatsApp's infrastructure.
Arxiv
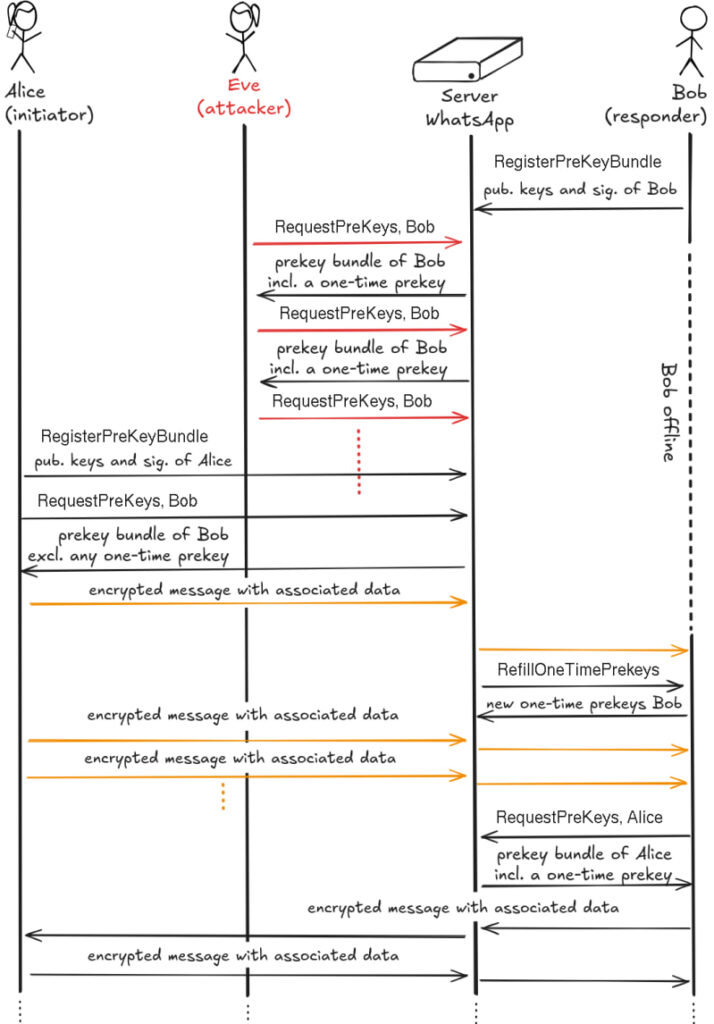
The attack exploits a missing safeguard: WhatsApp does not rate-limit the number of prekey bundle requests made for a user. As a result, a malicious actor can continuously fetch prekey bundles for a specific target, silently draining all their available one-time prekeys. When another user then initiates a new chat with the victim, the resulting session lacks PFS for initial messages, as no one-time prekey is available. These early messages can later be decrypted if the attacker gains access to the victim's long-term keys.
Arxiv
In addition to weakening forward secrecy, the researchers identified serious privacy concerns. By monitoring how and when devices replenish their depleted prekeys, an attacker can infer whether a device is online, track its activity patterns, or determine the operating system it runs. This type of side-channel analysis enables device fingerprinting and online status tracking without alerting the user or requiring message transmission. For example, if a device fails to refill its prekeys after depletion, it likely indicates the device is ofline — potentially revealing user habits, locations, or sleep schedules.
Worse still, the team demonstrated that overwhelming WhatsApp's servers with prekey queries could prevent new conversations from being established altogether, effectively enabling a denial-of-service (DoS) attack. In some cases, new chat sessions failed to initiate or phone calls were dropped. With sufficient request volume — exceeding 2,000 per second — the server began returning error codes that persisted across different clients, blocking legitimate users from obtaining prekey bundles entirely.
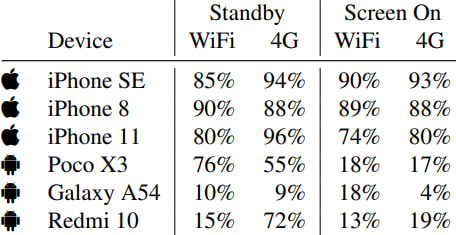
Device fingerprinting was also shown to be feasible through the analysis of key ID values and prekey batch sizes. For instance, Android and iOS devices use different schemes for assigning key IDs and initializing batches, allowing an attacker to determine the OS and even approximate the device's age or usage level. This information could be used for targeted phishing, surveillance, or tailored malware deployment.
Arxiv
While the researchers describe the real-world confidentiality impact of the PFS downgrade as “modest” due to Signal's self-healing ratchet and defense-in-depth architecture, they stress that WhatsApp's user interface offers no indication when initial messages are sent without forward secrecy. Users are left unaware that their messages could be compromised in the future.
To mitigate these risks, the authors recommend several defenses:
- Implement strict rate limits on prekey bundle requests.
- Shorten the lifetime of signed prekeys to reduce long-term exposure.
- Notify users when messages are sent without PFS.
- Randomize or hash key identifiers to prevent device fingerprinting.
- Introduce on-demand updates of signed prekeys during prekey refills to reduce the attack surface.
All the reported vulnerabilities can be exploited covertly by anyone with a WhatsApp account, without needing access to the victim's device or consent. Given WhatsApp's global reach and the simplicity of executing these attacks, the authors argue for urgent action from Meta to address these design oversights and harden the platform against abuse.
The findings were responsibly disclosed to Meta prior to publication of the paper, but as of publication, the vulnerabilities remain unpatched.
CyberInsider has reached out to WhatsApp for a comment on the security status of the communication platform and whether they plan to fix the discovered flaws soon, and we'll update the article with their response once received.







Leave a Reply