
Researchers from the University of Vienna uncovered a massive privacy issue in WhatsApp's contact discovery mechanism, allowing them to enumerate over 3.5 billion active accounts, including phone numbers, profile pictures, and encryption keys, without triggering any rate limits or bans.
The team warns that this flaw, which persisted until Meta quietly addressed it in October 2025, represents one of the largest exposures of personal data ever documented.
The discovery was made by researchers Gabriel Gegenhuber, Philipp É. Frenzel, Maximilian Günther, Johanna Ullrich, and Aljosha Judmayer, who presented their findings in a study to be published at NDSS 2026. Their experiment ran from December 2024 to April 2025, using WhatsApp's own infrastructure to probe over 100 million phone numbers per hour via a reverse-engineered API. Remarkably, WhatsApp imposed no restrictions on the query rate even when requests originated from a single university server using just five authenticated accounts.
By leveraging the absence of effective rate-limiting, the researchers built a dataset of over 3.5 billion user accounts. For each one, they were able to retrieve associated phone numbers, profile pictures (when public), “about” text, and even the encryption keys used for WhatsApp's end-to-end encrypted messaging. The study also highlighted that users in countries where WhatsApp is banned, such as China, Iran, Myanmar, and North Korea, were easily identifiable, exposing them to state surveillance or persecution risks.
WhatsApp, owned by Meta, operates as the world's most widely used messaging platform with over 3.5 billion active accounts, according to the researchers. The platform's global reach is facilitated by its convenience, allowing users to find contacts simply by syncing their phone numbers with WhatsApp's servers. The feature, shown to be vulnerable to enumeration attacks in 2012 and again in 2021, remained exposed to novel methods despite the vendor's efforts to plug previously exposed holes.
What sets this new research apart is its unprecedented scale and speed. The team developed a tool called libphonegen, which generated a realistic set of 63 billion potential mobile phone numbers across 245 countries. These were then checked for WhatsApp registration using the XMPP protocol via a modified open-source client named whatsmeow. At peak speed, the researchers were confirming 7,000 numbers per second without ever being blocked.
The exposed data provides unsettling insights:
- Profile photos: 56.7% of accounts globally had public profile pictures, with regional variances reaching 80% in some West African countries.
- About texts: 29.3% had visible status texts, some disclosing political views, religious affiliations, sexual orientation, or even links to external social media accounts.
- Business tags: Roughly 9% were labeled as business accounts, often due to users employing WhatsApp Business without understanding the implications for public data exposure.
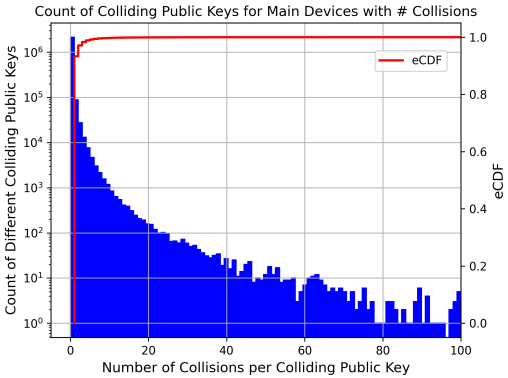
Particularly alarming was the discovery of 2.9 million instances of public key reuse, including identity keys, signed prekeys, and one-time prekeys, undermining the integrity of WhatsApp's end-to-end encryption. In one egregious case, 20 US phone numbers used a key consisting entirely of zeroes, suggesting a broken or malicious cryptographic implementation, possibly from third-party clients.
Meta, after being informed via its bug bounty program in April 2025, implemented stricter rate limits starting in October. However, the company claimed the exposed data was already public and emphasized that message content remained protected by encryption. Nonetheless, the researchers argue that the ability to generate a global user database, including cryptographic keys, poses substantial risks to user safety, especially in repressive regimes.
On a minor but related note, WhatsApp also disclosed a separate, unrelated security vulnerability earlier today (CVE-2025-55179), which affected WhatsApp for iOS and Mac. The bug allowed media to be fetched from arbitrary URLs, but Meta reports no evidence of exploitation in the wild. WhatsApp users should update their clients to benefit from the fixes.
Update: WhatsApp sent CyberInsider a comment on the researchers' findings, posted below.
“We are grateful to the University of Vienna researchers for their responsible partnership and diligence under our Bug Bounty program. This collaboration successfully identified a novel enumeration technique that surpassed our intended limits, allowing the researchers to scrape basic publicly available information. We had already been working on industry-leading anti-scraping systems, and this study was instrumental in stress-testing and confirming the immediate efficacy of these new defenses. Importantly, the researchers have securely deleted the data collected as part of the study, and we have found no evidence of malicious actors abusing this vector. As a reminder, user messages remained private and secure thanks to WhatsApp’s default end-to-end encryption, and no non-public data was accessible to the researchers.” – Nitin Gupta, VP of Engineering at WhatsApp






Leave a Reply