
A new variant of the Vo1d botnet has infected over 1.6 million Android TV devices globally, significantly expanding its scale and capabilities.
The botnet was previously seen in a campaign that infected 1.3 million Android TV boxes, reported by Doctor Web in September 2024.
Researchers at XLab identified the malware's latest evolution, which enhances stealth, resilience, and monetization tactics—including ad fraud, proxy services, and potential large-scale cyberattacks.
Vo1d botnet back in action
The Vo1d botnet was initially detected on November 28, 2024, when XLab's Cyber Threat Insight and Analysis System (CTIA) flagged an ELF file named jddx with zero detections on VirusTotal. The file was identified as a downloader using encryption patterns reminiscent of the Bigpanzi botnet but with distinct code structures. Further analysis confirmed that jddx belonged to a new Vo1d campaign, marking the botnet's latest resurgence.
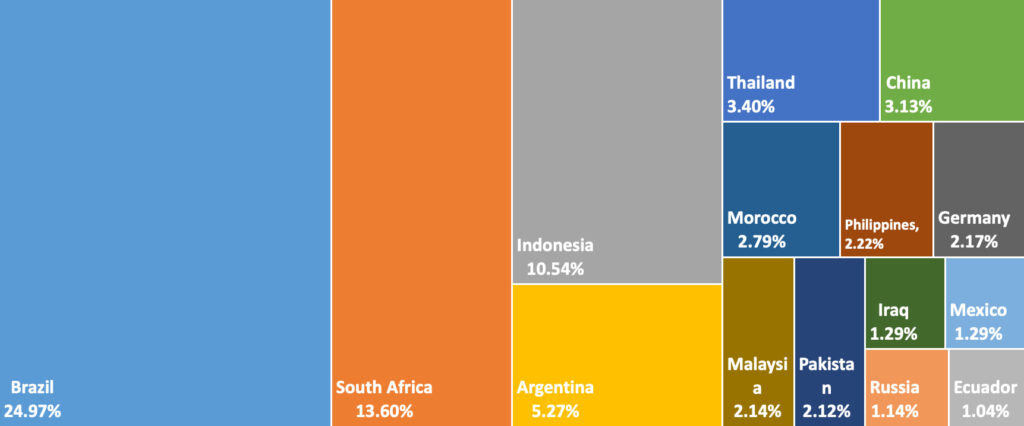
The scale of the infection is unprecedented. Vo1d has compromised Android TVs across 226 countries, with Brazil, South Africa, and Indonesia leading in infection rates. At its peak on January 14, 2025, daily active bots reached 1.59 million. The botnet's infrastructure includes 21 command-and-control (C2) domains, over 100,000 dynamically generated (DGA) domains, and an advanced encryption mechanism that protects its operations from security researchers.
XLab
Capabilities and potential threats
The Vo1d botnet is primarily designed for profit but retains the capability to launch high-impact cyberattacks. The most important scenarios are:
- DDoS Attacks – With a network of 1.6 million infected devices, Vo1d could easily surpass historical botnets like Mirai (2016) and Cloudflare's 2024 attack, both of which operated with fewer devices.
- Unauthorized Broadcasts – Recent incidents, such as AI-generated videos playing on compromised TVs at the U.S. Department of Housing and Urban Development (HUD), highlight how attackers could manipulate media streams for propaganda, disinformation, or explicit content.
- Monetization via Proxy Services & Ad Fraud – Vo1d operates an extensive proxy network, similar to the illicit 911S5 service, which generated $99 million in criminal profits. Infected devices are used for anonymized traffic, fraudulent advertising, and potential cybercriminal leasing agreements.
Technical breakdown
The malware consists of multiple components, including a downloader module that retrieves the main payload (ts01) from remote servers, encrypting all traffic using a modified XXTEA algorithm. The ts01 payload is a compressed package containing executable components (cv, vo1d, x.apk) that manage device persistence, launch additional malware, and report infection status. Vo1d's command-and-control network is highly resilient, utilizing a mix of hardcoded and DGA-generated domains. It employs RSA encryption to prevent hijacking, even if researchers register its DGA domains.
Xlabs also spotted a modular Android malware linked to Vo1d, consisting of entry, SDK, and plugin components, used for proxy services, ad fraud, and other cybercriminal activities.
Protecting devices from Vo1d
Given the scale and evolving nature of the Vo1d botnet, organizations and individuals must take proactive steps to secure their devices. The most important actions are to regularly update firmware, avoid unofficial app stores, and disable unnecessary remote access settings on Android TVs.
Common signs of infection include inexplicable device overheating, degraded performance, and suspicious network traffic. Performing a factory reset and changing the default admin credentials on impacted devices should be enough for a quick clean-up, followed by a firmware update.







Leave a Reply