
Researchers have uncovered an expansive malware campaign using a new information stealer dubbed PXA Stealer, actively deployed through malicious ZIP files and managed via Telegram-based infrastructure.
The operation, attributed to Vietnamese-speaking threat actors, has been targeting victims globally, including users in Japan, India, the US, the Philippines, and Germany. The discovery, made by SentinelLABS and Beazley Security, highlights how the attackers weaponize seemingly benign compressed files to initiate a multistage infection chain that ultimately exfiltrates sensitive user data to attacker-controlled Telegram bots.
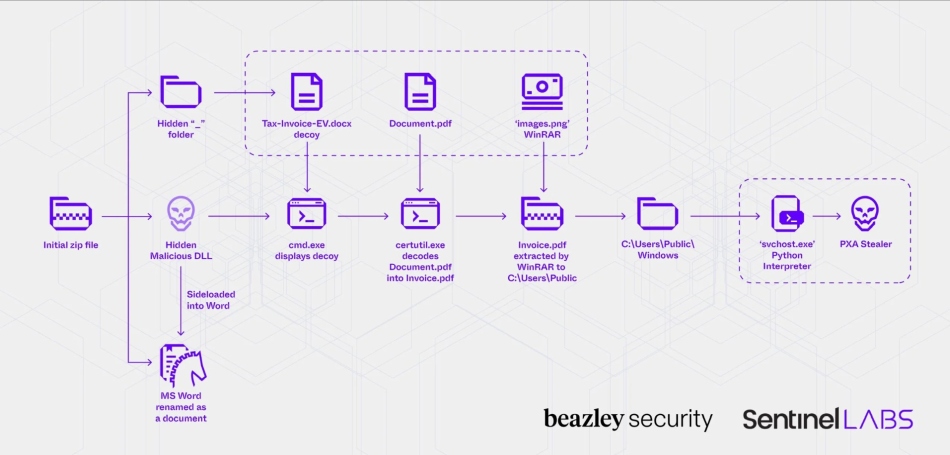
The attack starts with the delivery of ZIP archive files, typically through phishing emails or direct downloads. Once opened, the archive executes malicious code, leading to the deployment of PXA Stealer on the victim’s system. Written in Python and packed with the Nuitka compiler, the stealer is capable of evading detection and unpacking itself at runtime.
SentinelLABS
PXA Stealer is designed to collect a wide range of sensitive information from infected machines. This includes system metadata, browser-stored passwords, session cookies, cryptocurrency wallet data, and even screenshots. The stealer also attempts to exfiltrate data from applications such as Discord, Telegram, Steam, and various web browsers.
Telegram used for exfiltration and campaign control
What sets this campaign apart is the attacker’s heavy reliance on Telegram as both a command-and-control (C2) channel and an exfiltration pipeline. Once PXA Stealer gathers the victim’s data, it is transmitted directly to Telegram bots controlled by the operators. SentinelOne analysts identified multiple Telegram accounts associated with different attacker groups, suggesting a growing ecosystem of actors using the same core tool.
These accounts act as drop points for stolen data, allowing operators to manage their campaigns with minimal infrastructure investment and added anonymity. Researchers believe this use of Telegram also simplifies collaboration between threat actors and lowers the barrier to entry for launching similar campaigns.
Analysis of metadata and associated accounts indicates the threat actors are Vietnamese-speaking and possibly connected to prior malware campaigns involving XClient stealer, XWorm, and other commodity malware. One of the Telegram handles linked to the campaign, “@HackerVietnam1,” was observed promoting various stealer variants and offering malware services.
Notably, some Telegram channels connected to the campaign were observed selling ZIP malware builder kits, making it easier for less sophisticated actors to participate in the distribution of PXA Stealer. This ecosystem-driven approach points to an active and growing underground market in Southeast Asia for malware-as-a-service (MaaS) offerings.
Researchers warn that the malware is under continuous development, with updates introducing obfuscation techniques and new targeting capabilities. Several code variations tailored to specific regions and user environments have already been observed, indicating that the campaign is being fine-tuned for broader impact.
Prevention and mitigation
Users are advised to avoid opening unsolicited ZIP files and to remain cautious when downloading files from unfamiliar sources. Organizations should also consider monitoring for unusual outbound connections to Telegram domains and implement endpoint protections capable of detecting Python-compiled executables.
SentinelLABS continues to track the campaign and warns that its Telegram-based delivery and management model could serve as a blueprint for future low-cost, high-impact malware operations.







Leave a Reply