
A serious firmware security flaw has been discovered affecting around 200,000 Framework laptops and desktops.
Researchers at Eclypsium found that signed UEFI shells, legitimate diagnostic tools, can be used to bypass Secure Boot protections, exposing affected systems to stealthy pre-OS attacks.
Eclypsium’s investigation focused on signed .efi binaries used for diagnostics and firmware updates, which unintentionally grant attackers near-total control over system memory during early boot stages.
Framework, a hardware startup known for its repairable and upgradeable laptops, distributes UEFI shells for Linux users to perform firmware updates. These shells, which are signed using certificates trusted by Secure Boot, were found to contain commands, specifically the mm (memory modify) command, that enable direct memory access. While useful for legitimate debugging, the mm command can be weaponized to disable critical security features like Secure Boot entirely.
UEFI trust broken
Secure Boot relies on a chain of trust, beginning with a root certificate authority, typically Microsoft's UEFI CA, that validates all pre-boot components. When a UEFI application is signed with a trusted key, it is automatically executed by the firmware during boot, without prompting or warning.
This model assumes that signed components are benign. However, Eclypsium’s analysis shows that even these trusted binaries can contain functionality dangerous enough to neutralize security boundaries.
In this case, the UEFI shells distributed by Framework can be used to locate and overwrite the memory address of gSecurity2, a global variable pointing to the security protocol enforcing Secure Boot policies. By overwriting this pointer using mm, attackers can effectively disable signature verification, load unsigned UEFI modules, and establish persistence, all while the system falsely reports that Secure Boot is active.
Real-world risk
To confirm their findings, Eclypsium developed Python and shell scripts that analyzed .efi binaries for the presence of the mm command and tested their behavior in a QEMU virtual environment. These tests confirmed that several versions of Framework's UEFI shells were vulnerable. While no specific malware campaigns were linked to these shells directly, the researchers noted that gaming cheat developers, ransomware operators, and nation-state actors have increasingly turned to UEFI-based attacks to establish undetectable persistence below the OS.
This vulnerability is reminiscent of UEFI threats like BlackLotus and Bootkitty, which similarly exploited pre-boot environments to evade security controls. However, in contrast to those malware strains, the tools found on Framework devices were never designed to be malicious, making this issue more of a supply chain trust failure than a traditional backdoor.
Framework’s response
Framework has acknowledged the vulnerability and is actively working on remediations across its product lines. As of this writing:
- Firmware updates removing the mm command have already been released for several models, including the 12th and 13th-generation Intel, as well as AMD Ryzen-based systems.
- Updates to the DBX (revocation) database are being developed to blacklist older, vulnerable signed shells.
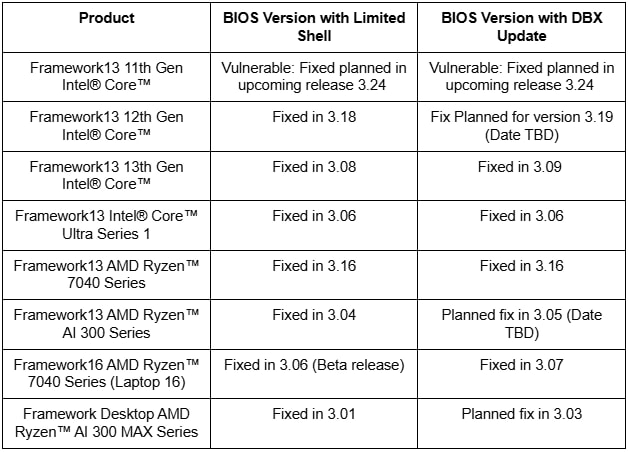
Framework has also pledged to provide documentation to help users delete their existing DB keys via BIOS, allowing them to manually revoke trust for the affected UEFI shells. Customers are encouraged to consult the company’s support resources or reach out directly for rollout timelines.







Leave a Reply