
A large collection of internal data was dumped over the weekend on a hacking forum and now Uber has confirmed a new data leak to RestorePrivacy that is unrelated to the September breach. Uber is blaming a third-party vendor. We analyzed the data for this report.
Update: Uber has now confirmed to RestorePrivacy that Teqtivity was the third-party vendor that was hacked, more info below.
American mobility service Uber has suffered an indirect data leak which, according to the company, has resulted from a hack on a third-party vendor.
On December 10, a user on the Breached forums posted a dump of data allegedly stolen from Uber, containing 20 million records of internal information.
Source: RestorePrivacy.com
The data wasn't put up on the forum for sale but instead shared freely with all users. The forum\'s admin also joined in the discussion, which is typically an indication of the legitimacy of the listing.
RestorePrivacy examined the data in the shared archive and found various spreadsheets containing asset data and various sensitive details, including personally identifiable and account information of about 77,000 Uber employees.
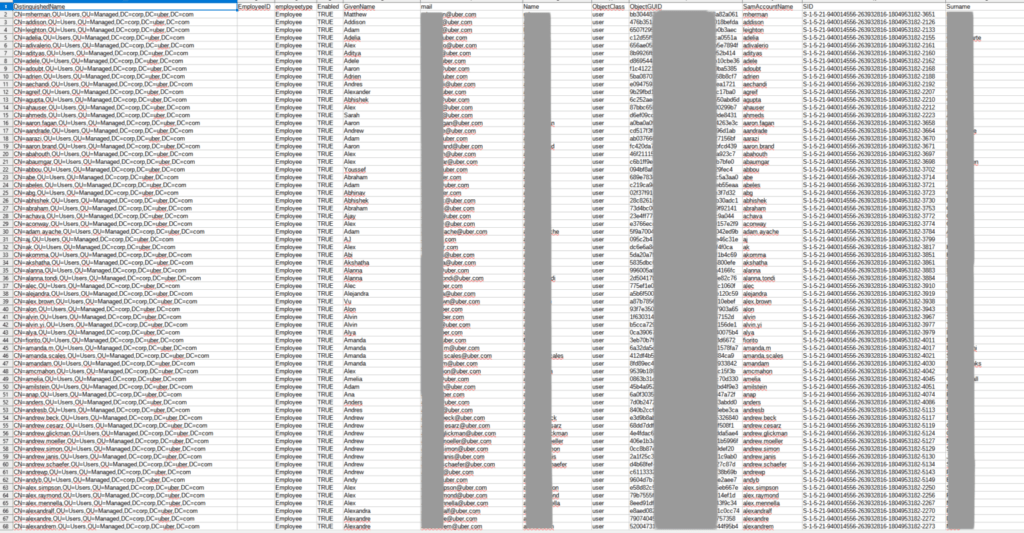
Source: RestorePrivacy.com
A separate thread posted on the same day shares an archive containing what seems to be source code, API details, web app data, and more.
Uber confirms new security breach
RestorePrivacy contacted Uber to verify the authenticity of the data, and the company told us they are still investigating the leaked dataset.
However, from the preliminary results of their review, it was deduced that the leak is unrelated to the September 2022 incident, and the source code belongs to a third-party vendor, not Uber.
“We believe these files are related to an incident at a third-party vendor and are unrelated to our security incident in September. Based on our initial review of the information available, the code is not owned by Uber; however, we are continuing to look into this matter.”
-Uber spokesperson\'s statement to RestorePrivacy
This confirms the novelty of the leaked data is new, but its impact on Uber is still unknown. Until the internal investigation is completed, not much can be said about the actual implications for Uber employees and users.
The forum user also posted data allegedly belonging to TripActions, a travel management services firm, and Teqtivity, an IT asset management software vendor.
These companies aren't linked to Uber, so they might have been impacted by the same security incident on the unnamed third party that affected Uber.
Update: Teqtivity is the third-party vendor that was breached
In an updated statement to RestorePrivacy, Uber has confirmed that the breach happened via its third-party vendor Teqtivity. Uber directed us to this statement from Teqtivity, published today:
We are aware of customer data that was compromised due to unauthorized access to our systems by a malicious third party. The third party was able to gain access to our Teqtivity AWS backup server that housed Teqtivity code and data files related to Teqtivity customers.
– Teqtivity statement
A third-party forensics firm has been retained to investigate all logs and server configuration. A third-party security team has also been hired to begin a penetration test of the infrastructure. We have notified law enforcement officials.
According to Teqtivity's post, the exposed information contains:
- User Information: First Name, Last Name, Work Email Address, Work Location details
- Device information: Serial Number, Make, Models, Technical Specs
This corresponds to the data analyzed by RestorePrivacy earlier today in the screenshot above.
An Uber spokesperson told RestorePrivacy that Taqtivity helps Uber to \”manage and track IT assets, like phones and computers.”
Teqtivity has not quantified the scale or impact of the breach at this time.
Uber's September breach
On September 2022, Uber disclosed it had suffered a security incident after the account of a contractor was compromised by hackers who bought their credentials on the dark web.
Although the contractor had two-factor authentication enabled to protect their account, the hackers employed “MFA fatigue” tactics to approve at least one OTP request, resulting in a breach of Uber\'s internal systems.
The attacker compromised multiple Uber employee accounts and gained extensive access to Uber\'s systems, including the Slack channel, AWS accounts, HackerOne account, and more.
This article will be updated with any new information that develops.







Hi RP, I hadn’t heard of ‘“MFA fatigue” tactics to approve at least one OTP request’.
Thank you for bring this to my attention.
I’m hungry. can you feed me? 🥺
Sven Sir currently a bill is in the parliament of UK under discussion which if passed will be the death knoll to End to End Encryption in UK, specially for messaging apps. The argument in support of this law being given by the government is that it will help the government agencies to scan messages for illegal content using tools mandated by the government therefore catching illegal content and making UK internet space the safest in the world.
Sir What are your views regarding this? Please write an article (you not Heinrich Sir) explaining the possible implications of such laws which are under consideration by UK and EU to abolish End to End Encryption to prevent online abuse.
I’m noticing a trend of big companies getting exposed when trusted third parties get hacked. Perhaps it’s time to start limiting the data that third parties have access to.