
ReasonLabs has uncovered a widespread Trojan malware campaign that force-installs malicious web browser extensions on users' devices, affecting over 300,000 users across Google Chrome and Microsoft Edge.
The campaign, active since 2021, not only hijacks users' search queries but also executes a series of malicious commands to compromise user data and control browser behavior.
Campaign overview
The campaign employs from fake download websites mimicking popular services like Roblox, YouTube, and VLC Media Player. Instead of providing the promised software, these sites deliver a Trojan that silently installs extensions on the user's browser.
The extensions, ranging from basic adware to advanced scripts, are designed to steal sensitive information and modify browser settings. This includes disabling browser updates, tampering with browser shortcuts, and even overriding search engine settings to redirect queries through the attacker’s servers.
Technical details
Once a user downloads the malicious software, the program creates a scheduled task on the infected system, often under misleading names like NvOptimizerTaskUpdater_V2. This task triggers a PowerShell script stored in the system's System32 folder, which downloads and executes additional payloads from a remote command-and-control (C2) server. The script then installs malicious extensions by modifying registry keys in Chrome and Edge, making it impossible for users to remove the extensions via normal means.
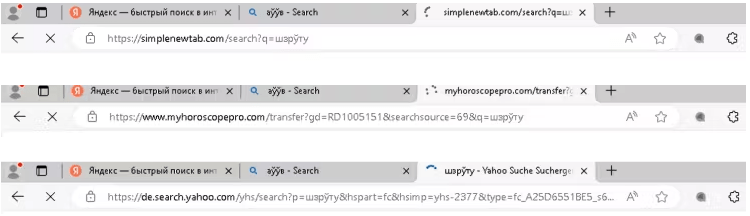
The extensions perform various malicious activities, including redirecting searches through attacker-controlled domains before finally delivering results from legitimate search engines like Yahoo or Bing.
ReasonLabs
The extensions cannot be disabled by users, even with browser developer mode enabled. The malware goes to great lengths to hide its presence, including altering browser shortcuts and disguising itself as legitimate processes. ReasonLabs reports that the Trojan's most recent iterations are particularly insidious, as they modify core browser DLL files to further embed the malicious extensions, making detection and removal even more challenging.
Impact and response
The malware campaign has primarily targeted users of Google Chrome and Microsoft Edge, with over 200,000 Chrome users and 100,000 Edge users affected by extensions like “Micro Search,” “Simple New Tab,” and “yglSearch.”
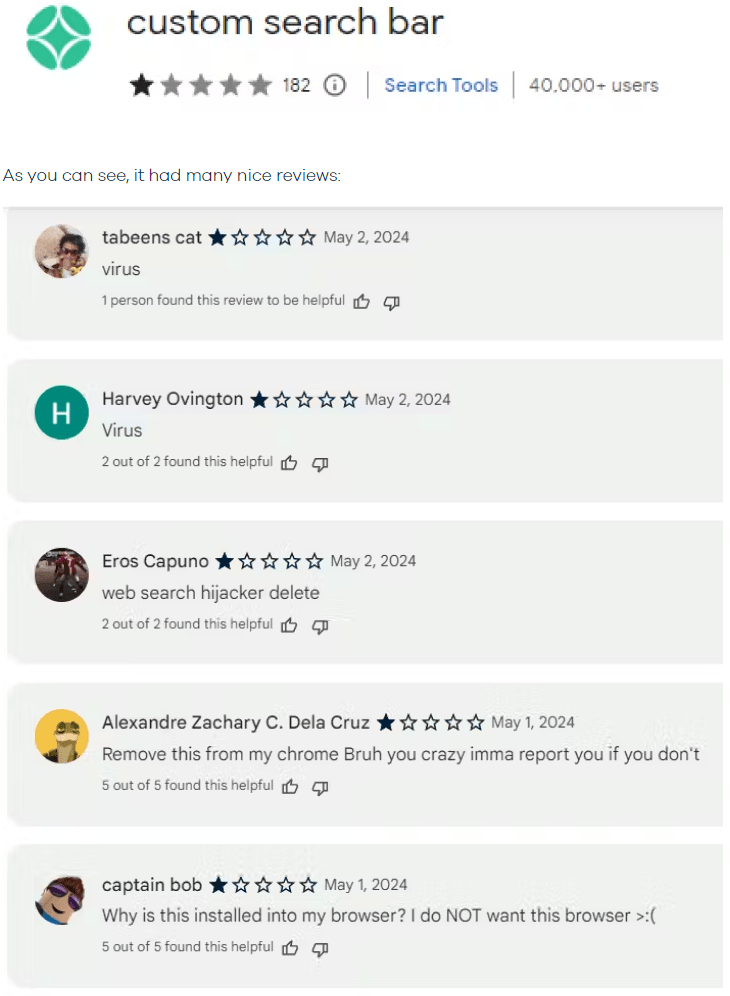
These extensions have garnered thousands of downloads before being removed from official stores, but new versions continue to emerge, complicating efforts to mitigate the threat.
ReasonLabs
ReasonLabs alerted both Google and Microsoft to the issue, and the companies are taking measures to remove the malicious extensions and block further installations. However, many users remain unaware that their browsers are compromised, as the malware evades most antivirus detections.
Defense and mitigation
To defend against this malware, users are advised to take the following steps:
- Identify and delete any suspicious scheduled tasks in the Task Scheduler that reference PowerShell scripts located in the System32 folder.
- Remove the malicious registry keys that force the installation of extensions by navigating to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Google\Chrome\ExtensionInstallForcelist for Chrome and the corresponding path for Edge.
- Manually search for and delete files associated with the malware, particularly in the System32 folder and other locations identified by ReasonLabs.
- Employ reputable antivirus tools to scan and remove any residual malware.
The complete list of the malicious extensions to search for and remove is given below.
Google Chrome Extensions:
- Custom Search Bar – 40,000+ users
- yglSearch – 40,000+ users
- Qcom Search Bar – 40+ users
- Qtr Search – 6,000+ users
- Micro Search Chrome Extension – 180,000+ users (removed from Chrome store)
- Active Search Bar – 20,000+ users (removed from Chrome store)
- Your Search Bar – 40,000+ users (removed from Chrome store)
- Safe Search Eng – 35,000+ users (removed from Chrome store)
- Lax Search – 600+ users (removed from Chrome store)
Microsoft Edge Extensions:
- Simple New Tab – 100,000+ users (removed from Edge store)
- Cleaner New Tab – 2,000+ users (removed from Edge store)
- NewTab Wonders – 7,000+ users (removed from Edge store)
- SearchNukes – 1,000+ users (removed from Edge store)
- EXYZ Search – 1,000+ users (removed from Edge store)
- Wonders Tab – 6,000+ users (removed from Edge store)







Google is extremely complacent these days and really doesn’t give much attention to the security of its extensions.
More and more of its extensions are becoming compromised in Github. There are fake (not just cloned) versions of uBlock Origin in the official Chrome Web Store. Additionally, many shills, likely bots, have recently “attacked” the negative reviews of uBlock Origin by downvoting criticism of the extension which will be deprecated in 2025 due to the developers failing to upgrade to MV3. While typically a few reviews of the extension occur on a monthly or weekly basis, now the uBlock extension is saturated with glowing artificial positive reviews. One has to wonder who’s behind all this.
Meanwhile, Google just sits idly and reporting apps and reviews are effectively inconsequential or meaningless. That’s Google!