
A new global IoT botnet campaign dubbed “Ballista” targets TP-Link Archer routers via a known remote code execution (RCE) vulnerability.
The botnet is actively targeting thousands of devices worldwide, spreading automatically and evolving its tactics to evade detection.
Cato Networks researchers identified the Ballista botnet on January 10, 2025, during an ongoing analysis of IoT device exploitation attempts. Over the following weeks, multiple initial access attempts were observed, with the latest attack recorded on February 17. The botnet leverages CVE-2023-1389, a vulnerability in the web management interface of TP-Link Archer routers, allowing unauthenticated attackers to execute arbitrary commands with root privileges.
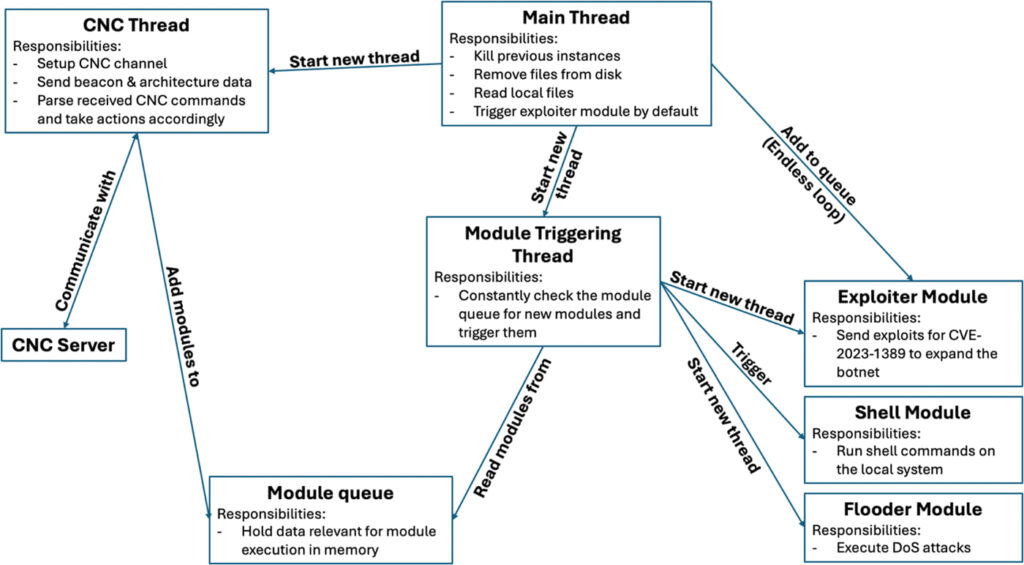
The infection chain begins with a malware dropper—delivered as a bash script—which downloads and executes malicious binaries on the compromised device. The malware then establishes an encrypted command-and-control (C2) channel on port 82, enabling remote attackers to issue shell commands, conduct further RCE attacks, and launch denial-of-service (DoS) campaigns. Additionally, the malware attempts to access sensitive system files, such as password and SSL configuration files, potentially enabling credential theft and lateral movement.
As Cato continued investigating the campaign, the botnet operators adapted their methods by switching to Tor domains for C2 communication, indicating an effort to increase stealth and persistence.
Ballista capabilities
Ballista operates with a modular architecture, allowing attackers to execute various functions through C2 commands. The malware's key capabilities include:
- Self-preservation: Kills previous instances of itself and deletes traces from disk to evade detection.
- Automated propagation: Actively exploits CVE-2023-1389 to infect additional devices.
- Command execution: Executes arbitrary shell commands on compromised routers.
- DoS attacks: Launches TCP-based flooding attacks.
- Credential theft: Reads system configuration files, including /etc/passwd and /etc/shadow.
- Stealth mechanisms: Uses TLS encryption for C2 communication and recently shifted to Tor domains for added anonymity.
Cato Networks
Impact and attribution
The Ballista botnet has been observed targeting organizations across multiple industries, including manufacturing, healthcare, technology, and services, with confirmed victims in the U.S., Australia, China, and Mexico. Using Censys, researchers identified over 6,000 vulnerable TP-Link Archer routers exposed to the Internet, highlighting the widespread risk posed by the botnet.
Cato CTRL attributes Ballista with moderate confidence to an Italian-based threat actor. This assessment is based on the location of a key C2 server (IP: 2.237.57[.]70) and the presence of Italian-language strings within the malware binaries. The use of an ancient Roman siege weapon as the botnet's namesake further aligns with this regional connection.
TP-Link, a major manufacturer of networking equipment, has faced scrutiny in recent months due to security concerns. In August 2024, we reported that U.S. government agencies were considering banning TP-Link devices over potential security risks linked to China. This context underscores the broader implications of router security vulnerabilities in enterprise and government environments.
To protect against Ballista and similar IoT botnet threats, users need to ensure they have updated to the latest firmware version, especially one that mitigates CVE-2023-1389. Moreover, it is recommended to change default admin account credentials and isolate IoT devices from critical systems to reduce the impact of a potential compromise.







Leave a Reply