
ONEKEY Research Lab has uncovered a severe vulnerability in TP-Link's Archer C5400X Tri-Band Gaming Router, potentially allowing remote unauthenticated attackers to execute arbitrary commands with elevated privileges.
This flaw, tracked under CVE-2024-5035, affects firmware versions up to 1.1.6, with TP-Link having released a patch in version 1.1.7.
Discovery and details
While testing and validating their new binary zero-day identification feature, ONEKEY's automated analysis revealed several vulnerabilities in various devices, including the TP-Link Archer C5400X. Specifically, the issue lies in the rftest binary, which is utilized for radio frequency testing. This binary exposes a network listener on TCP ports 8888, 8889, and 8890, vulnerable to command injection and buffer overflows.
The rftest binary is launched during the router's initialization sequence and listens on TCP port 8888. This network service is susceptible to command injection due to the insecure handling of input via the read() function. Commands received can be manipulated using shell meta-characters (;, &, |) to bypass restrictions and inject malicious commands. For instance, an attacker can connect to port 8888 and send a crafted payload to gain unauthorized access and execute commands on the device.
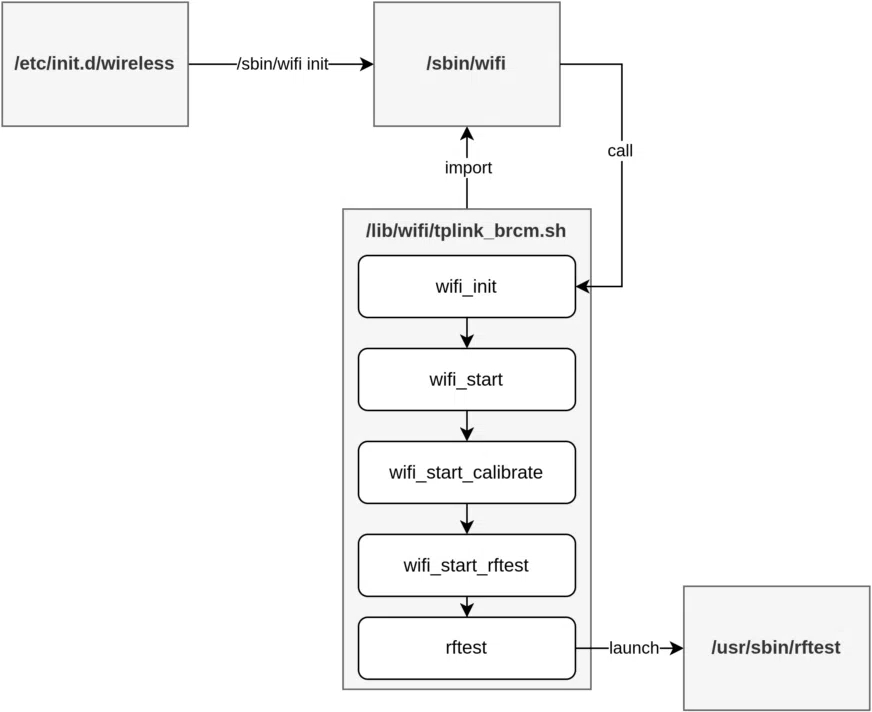
A remote, unauthenticated attacker could exploit the identified vulnerability to gain root access to the affected devices. This flaw's critical nature is highlighted by its CVSS score of 10.0, which indicates maximum severity. Successful exploitation would give the attacker full control over the router, potentially compromising the network and connected devices.
Timeline and TP-Link's response
- February 16, 2024: Vulnerability reported to TP-Link PSIRT.
- February 19, 2024: The vendor acknowledges the report and opens a case.
- April 10, 2024: TP-Link shares a beta version of the patched firmware (1.1.7p1) for validation.
- April 17, 2024: ONEKEY confirms the patch's effectiveness.
- May 27, 2024: ONEKEY releases the security advisory in coordination with TP-Link.
TP-Link has issued firmware version 1.1.7, which mitigates the vulnerability by discarding any commands containing shell meta-characters, thereby preventing command injection attempts.
Users of Archer C5400X routers are urged to update their firmware to version 1_1.1.7 immediately. This can be done through the router's firmware upgrade feature, which is available on the vendor's support site. Users should always ensure they download firmware from the official TP-Link website corresponding to their device's purchase location to avoid warranty issues and potential device damage.







Leave a Reply