
The Tor Project has announced the release of a new bridge called ‘WebTunnel,’ designed to help users bypass censorship in highly problematic regions where accessing the Tor network is particularly challenging.
WebTunnel comes in addition to Tor browser‘s multiple censorship circumvention technologies, and its release coincides with the World Day Against Cyber Censorship.
Tor bridges are a kind of “unlisted” relay that gives users a secret entry point to connect to the Tor network by routing their traffic through a series of bounce points. Because these relays are unknown to the censoring entities (governments, ISPs, etc.), they aren’t included in common blocklists, so people can use them to bypass censorship.
However, this approach isn’t ideal in all possible scenarios, especially in regions with aggressive censorship. For example, the ‘obfs4’ system in Tor, which acts as a bridge for users, can be identified and blocked by internet service providers due to its traffic appearing suspiciously unrecognizable, a side effect of encryption. Eventually, blocking parties catch up with conventional circumvention methods, and the relays must be refreshed.
Tor addresses this problem by introducing a new kind of bridge designed to be unrecognizable from normal traffic. WebTunnel functions as a pluggable transport that mimics encrypted web traffic (HTTPS) and is specifically designed to resemble WebSocket-like HTTPS connections. This enables user traffic to blend with regular web traffic, making it difficult for observers to detect that the user employs a censorship circumvention tool.
“WebTunnel is so similar to ordinary web traffic that it can coexist with a website on the same network endpoint, meaning the same domain, IP address, and port,” reads Tor’s announcement.
“This coexistence allows a standard traffic reverse proxy to forward both ordinary web traffic and WebTunnel to their respective application servers […so] when someone attempts to visit the website at the shared network address, they will simply perceive the content of that website address and won’t notice the existence of a secret bridge.”
To enable WebTunnel on your Tor browser, follow these simple steps:
- Visit https://bridges.torproject.org/options
- Choose “webtunnel” in “Advanced Options” and click “Get Bridges”
- Solve the captcha and copy the bridge line
- Download the latest Tor Browser version (older than 12.5.x won’t work) from the Tor Project’s website
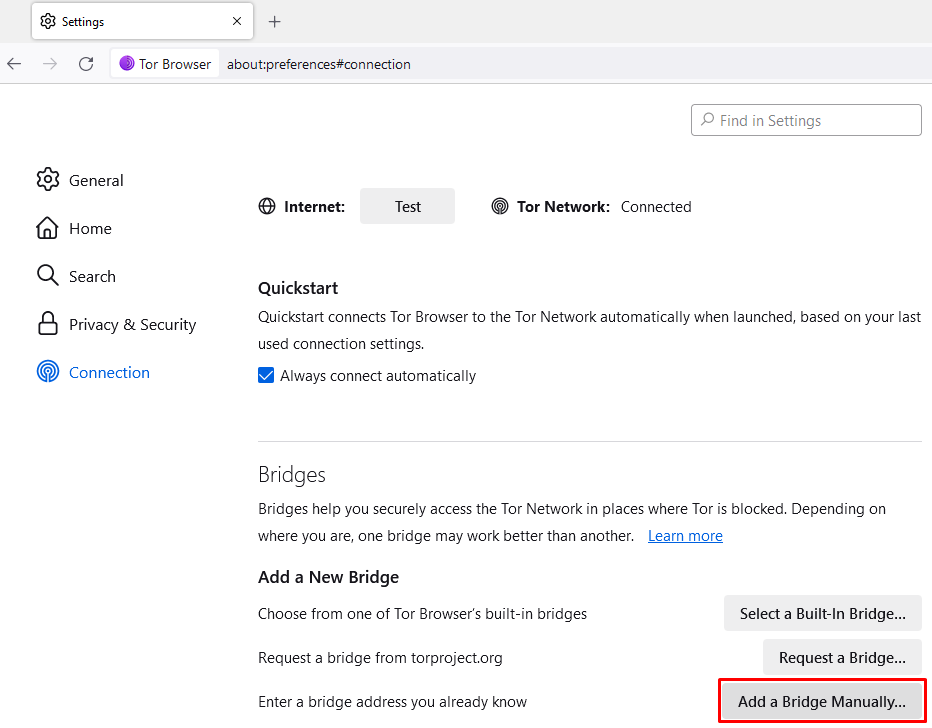
- Open Tor Browser, go to Settings > Connection and click “Add a Bridge Manually” and paste the copied bridge line
- Click “Connect”
On Android, install the latest Tor Browser version from Google Play, launch it, choose “configure a bridge,” select the “Provide a Bridge I know” option, and enter the copied address. Finally, Tap “OK” to connect.

 Tuta Mail Adds Quantum Resistant Encryption via TutaCrypt
Tuta Mail Adds Quantum Resistant Encryption via TutaCrypt
Sit thank you for the article. Tor can be a bit unsafe as has been well described by Sven Sir in his article which is still relevant, nevertheless it is good to have an option other than VPN to bypass censorship, specially for whistleblowers, human right activists and dissidents in dictatorial regime.