
On June 8, 2024, Kadokawa Corporation, a prominent Tokyo-based media company, suffered a ransomware attack, affecting its servers and disrupting key business operations. The company has since been striving to restore its systems and mitigate the impact on its operations, especially on Niconico, a widely used video-sharing platform, and other critical services.
Kadokawa publicly acknowledged the attack in a series of updates, the latest released earlier today. The corporation expressed its deepest apologies to all stakeholders affected by the disruptions. It said its efforts are now focused on rebuilding a secure network and server environment, prioritizing the restoration of accounting functions, which are crucial to its business activities.
Kadokawa is a major player in the Japanese media industry, renowned for its publishing, web services, and merchandise businesses. Its reach extends across various media formats, including books, magazines, movies, and digital content, making the attack's impact far-reaching.
Disruption and mitigation efforts
Publishing Business: The ransomware attack has significantly affected the production and distribution of physical and digital publications. While new publications are being produced at usual levels, the shipment of existing publications is operating at about one-third of its normal capacity. Kadokawa employs alternative arrangements, such as increased human resources, to minimize disruptions and expedite recovery.
Web Services: The attack suspended all Niconico services, preventing users from logging into external services via Niconico accounts. Kadokawa has introduced provisional services like Niconico Video (Re: tmp) and Niconico Live Streaming (Re: tmp) to maintain some functionality. Full service restoration is being pursued gradually.
Merchandise Business: The wholesale of merchandise has been less affected, with shipping functions restored to normal levels. However, account authentication issues are affecting users' access to online shops, prompting Kadokawa to create temporary pages and consider alternative authentication solutions.
BlackSuit ransomware claims
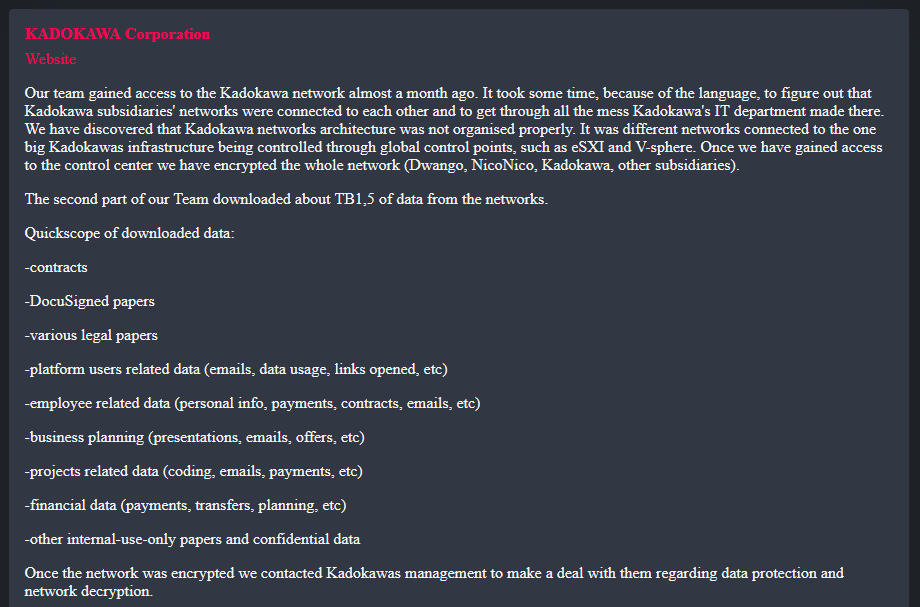
The BlackSuit ransomware gang has claimed responsibility for the attack, alleging they infiltrated Kadokawa's network a month before the encryption event. According to their statements on their extortion portal, they discovered flaws in Kadokawa's network architecture, which allowed them to access and control various subsidiaries' networks through centralized control points like eSXI and V-Sphere.
The group claims to have downloaded approximately 1.5 terabytes of data, including:
- Contracts and legal documents
- DocuSigned papers
- User data (emails, data usage, etc.)
- Employee information (personal details, contracts, emails, etc.)
- Business planning documents
- Financial data (payments, transfers, etc.)
- Project-related data
They further allege that Kadokawa's IT department detected their presence three days before the network encryption but failed to prevent the data exfiltration. The group has issued a ransom demand, threatening to release the stolen data, which includes sensitive personal information about Japanese citizens, if their financial demands are not met by July 1.
Kadokawa is collaborating with external cybersecurity professionals to investigate the extent of the data breach. The company has assured that no credit card information was compromised, as it does not store such data in its systems.
More detailed results from the investigation are expected in July, but by that time, BlackSuit may have realized its data leak threats. That said, Kadokawa's management is under immense pressure to resolve the situation, with the potential release of sensitive data looming.







Leave a Reply