
Security researchers have uncovered a sophisticated cyberespionage technique used by the ToddyCat APT group to execute malicious payloads undetected — by hijacking a vulnerability in a command-line scanner component of ESET's own antivirus suite.
The incident was investigated by Kaspersky in early 2024, which discovered a malicious file named version.dll on multiple compromised systems. Analysis revealed it to be part of a new ToddyCat toolkit named TCESB, a custom malware designed to stealthily execute in protected environments. What makes this campaign notable is that the attackers used a signed ESET executable to sidestep system defenses, effectively turning a security tool into an unwitting malware host.
Leveraging ESET for evasion
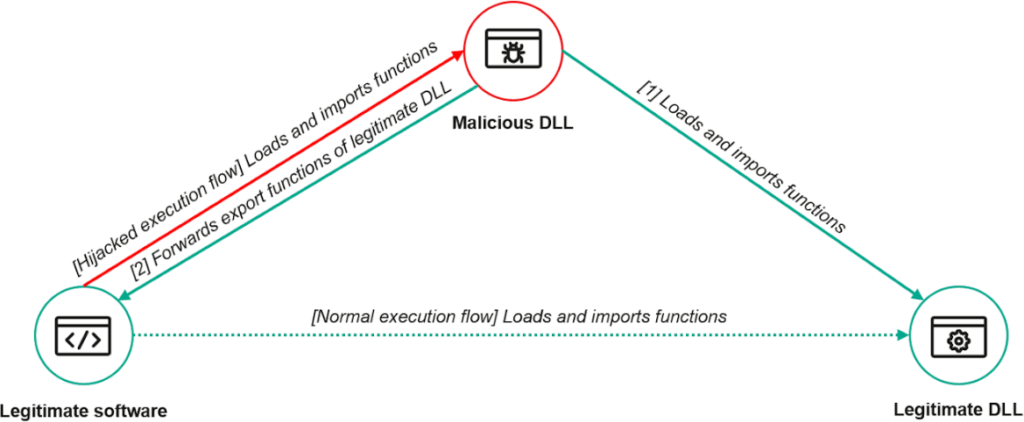
ToddyCat is a long-running, espionage-oriented APT group known for targeting high-profile organizations across Asia and Europe. In this case, they exploited CVE-2024-11859, a vulnerability in ESET's Command Line Scanner (ecls.exe) — a legitimate component of the ESET Endpoint Protection suite. This tool, when executed, loads the version.dll library insecurely, first searching in its current directory before looking in system folders. Attackers capitalized on this behavior by dropping a malicious DLL with the same name into the local directory, triggering its execution within the trusted context of ESET's scanner.
The malicious DLL was a proxy, mimicking the export functions of the legitimate version.dll but quietly redirecting calls to the system's real version while running ToddyCat's code in parallel. This “DLL proxying” approach enabled malware execution under the guise of a trusted security process — an especially insidious method, as EDR tools are typically configured to trust EPP components by default.
Kaspersky
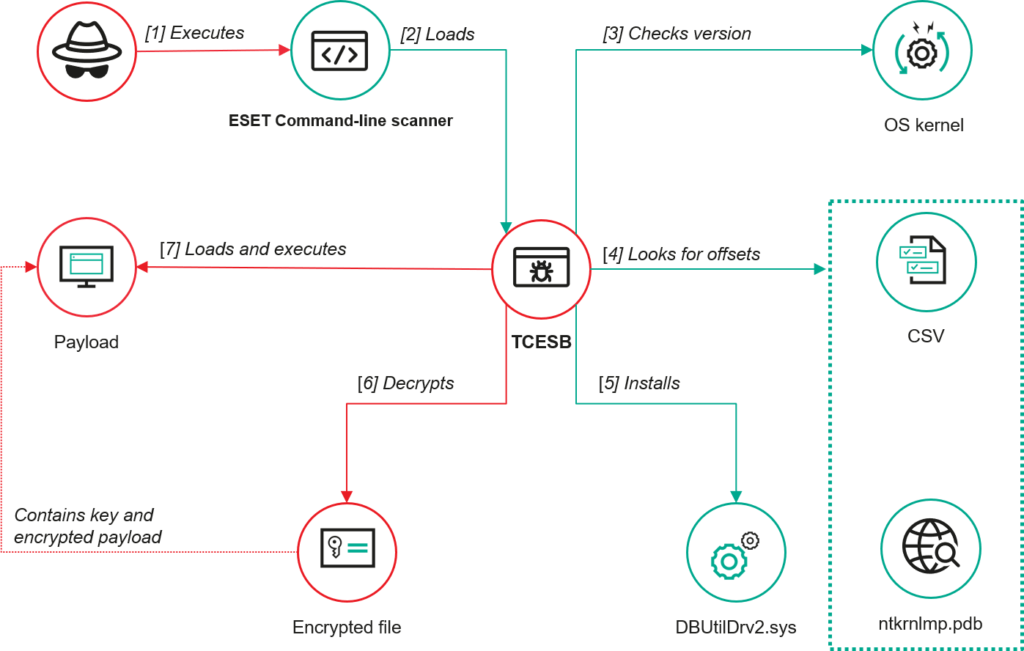
TCESB is based on a modified version of the open-source malware framework EDRSandBlast, with enhancements for deeper stealth. Once loaded, it disables kernel notification routines (such as process creation alerts) by modifying Windows kernel structures. To do this safely and without triggering alerts, it uses a Bring Your Own Vulnerable Driver (BYOVD) technique, deploying Dell's DBUtilDrv2.sys — a known vulnerable driver (CVE-2021-36276) — to execute privileged operations in kernel space.
A core part of TCESB's evasion strategy involves dynamic identification of Windows kernel version information. The malware reads a bundled CSV file containing kernel structure offsets for various OS versions and, if necessary, fetches Microsoft's official debugging symbols to locate needed memory structures — an unusual move typically not observed in malware operating at this level.
TCESB then waits in a loop, scanning the local directory every two seconds for a specific payload file. When found, the payload is decrypted using an AES-128 key embedded at the start of the file and loaded directly into memory for execution. This delay-before-load approach allows attackers to confirm a successful, stealthy deployment before risking exposure by dropping the final stage of the attack.
Kaspersky
Despite the sophisticated obfuscation, the TCESB tool was eventually caught by Kaspersky's telemetry. The ESET vulnerability was disclosed responsibly under a Coordinated Vulnerability Disclosure process, and a patch was issued on January 21, 2025. The flaw was further detailed in ESET's advisory, which was released late last week.
Blocking the attacks
ESET is a Slovakia-based cybersecurity vendor best known for its antivirus and endpoint protection solutions, widely used by both enterprise and consumer customers worldwide. While its software is generally regarded as robust, this incident underscores how even security tools can become liabilities when implementation flaws are present — especially in components operating with elevated privileges.
To defend against similar attacks, it is recommended to:
- Block known vulnerable drivers using Microsoft's Windows Defender Application Control (WDAC) or third-party driver blocklists such as those from the LOLBAS/LODLRIVERS project.
- Monitor for unexpected symbol downloads from Microsoft's symbol server, especially on systems where kernel debugging is not performed.
- Audit all DLL load paths to ensure only digitally signed, trusted binaries are loaded from secure directories.
- Update endpoint protection software promptly upon the release of security patches.







Leave a Reply