
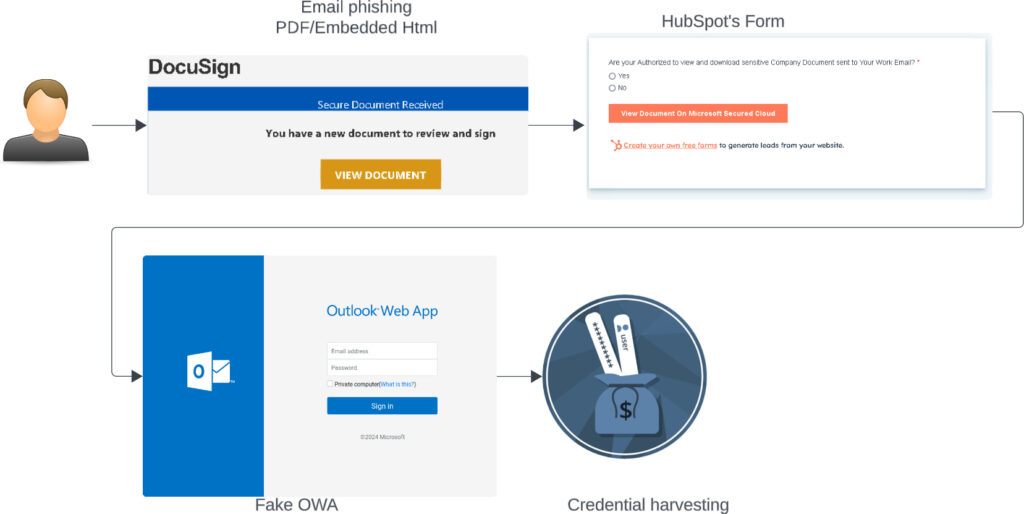
Unit 42 researchers have uncovered an ongoing phishing campaign targeting European companies, particularly in Germany and the UK. The attacks began in June 2024 and persisted as late as September 2024. The campaign used fraudulent forms hosted on HubSpot's Free Form Builder service to harvest credentials, enabling attackers to compromise Microsoft Azure cloud environments. Approximately 20,000 users from industries including automotive, chemical, and industrial compound manufacturing were affected.
HubSpot abuse
The phishing campaign was identified when Unit 42 researchers analyzed malicious emails embedding either DocuSign-themed PDFs or HTML links. Victims were directed to phishing pages masquerading as legitimate Microsoft Outlook Web Apps or other brand-specific portals. Despite using HubSpot's form builder to host malicious links, investigators confirmed that HubSpot's infrastructure itself was not compromised.
Unit 42
Notably, phishing emails manipulated urgency and exploited authentication failures to evade detection. Email headers frequently showed failed Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) checks, common red flags for phishing attempts.
The phishing infrastructure relied heavily on Bulletproof VPS hosts, known for their resistance to takedowns. Threat actors reused domains and infrastructure across multiple campaigns, primarily using .buzz top-level domains to host phishing sites. Their tactics also included using Base64-encoded phishing links to obfuscate URLs and employing unusual user-agent strings like Client=OWA;Action=ViaProxy for stealthy connections.
Unit42
Targeted entities and impact
The campaign focused on high-value industries with critical operational infrastructure, such as the automotive sector, chemical manufacturers, and industrial compound manufacturing entities.
Once user credentials were compromised, attackers employed advanced persistence techniques. These included adding new devices to victims' accounts and using VPN proxies to simulate login attempts from victims' home countries. This led to a struggle between attackers and victims to control affected accounts, as seen in ongoing password resets and alerts.
Unit 42 collaborated with HubSpot to mitigate the misuse of their services and developed alerts to detect suspicious forms. They also worked closely with affected companies to recover from breaches. Meanwhile, organizations targeted by the campaign implemented stricter controls, such as monitoring unusual authentication behaviors and deploying enhanced multi-factor authentication (MFA).
To stay safe from similar threats, enforce SPF, DKIM, and DMARC protocols to prevent spoofing and protect accounts with multi-factor authentication to prevent takeovers, even in cases of credential compromise.







Leave a Reply