
The second day of the Pwn2Own Automotive 2025 hacking competition saw security researchers uncover 23 unique zero-day vulnerabilities, earning a total of $335,500 in bounties. The event, organized by Trend Micro’s Zero Day Initiative (ZDI), continues to expose critical security flaws in electric vehicle (EV) chargers, in-car infotainment systems, and other automotive technologies.
One of the standout discoveries came from Sina Kheirkhah (@SinSinology) of Summoning Team, who exploited multiple vulnerabilities across different devices, cementing his position as a leader in the Master of Pwn standings. His most notable success came from chaining six different bugs, including improper access control and stack-based buffer overflows, to exploit the Autel MaxiCharger—though one of the flaws was already known.
Other significant findings include:
Tesla Wall Connector
- PHP Hooligans exploited a numeric range comparison bug (CWE-839) to take control of the device, earning $50,000.
- Synacktiv leveraged a logic bug via the Charging Connector, netting $45,000.
WOLFBOX Level 2 EV Charger
- Rafal Goryl of PixiePoint Security successfully exploited the device using a two-bug chain, though one of the flaws was already known, earning $18,750.
ChargePoint HomeFlex EV Charger
- Viettel Cyber Security used command injection combined with a known vulnerability, winning $18,750.
Infotainment systems
- Juurin Oy, Elias Ikkelä-Koski, and Aapo Oksman uncovered a command injection flaw in the Kenwood DMX958XR infotainment system, securing $10,000.
- PCAutomotive chained a heap overflow, authentication bypass, and improper isolation flaw to hack the Sony XAV-AX8500 infotainment system, winning $10,000.
Despite many successes, some teams faced bug collisions, meaning they independently discovered and exploited vulnerabilities that had been previously identified. These efforts still earned them partial rewards.
The vulnerabilities exposed at Pwn2Own Automotive 2025 highlight the growing attack surface in modern vehicles, where EV chargers, infotainment systems, and connected services become potential entry points for cyber threats. Companies like Tesla, ChargePoint, and Alpine—whose products were successfully exploited—must now work swiftly to patch these flaws before they can be exploited in the wild.
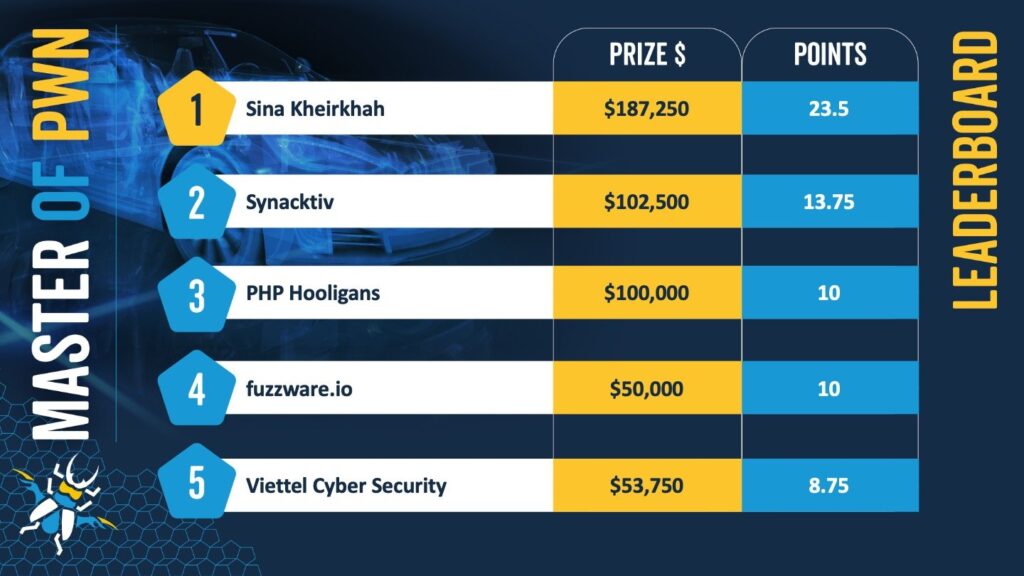
By the end of Day Two, Sina Kheirkhah is leading with 23.5 points and $187,250 in prize money, followed by Synactiv with 13.75 points and $102,500 in monetary awards.
With one day left in the competition, researchers are expected to give all they have tomorrow and reveal more critical weaknesses in modern automotive systems.







Leave a Reply