
A disturbing spearphishing campaign leveraging a fake Steam game has resulted in the theft of over $32,000 in cryptocurrency from a terminally ill cancer patient.
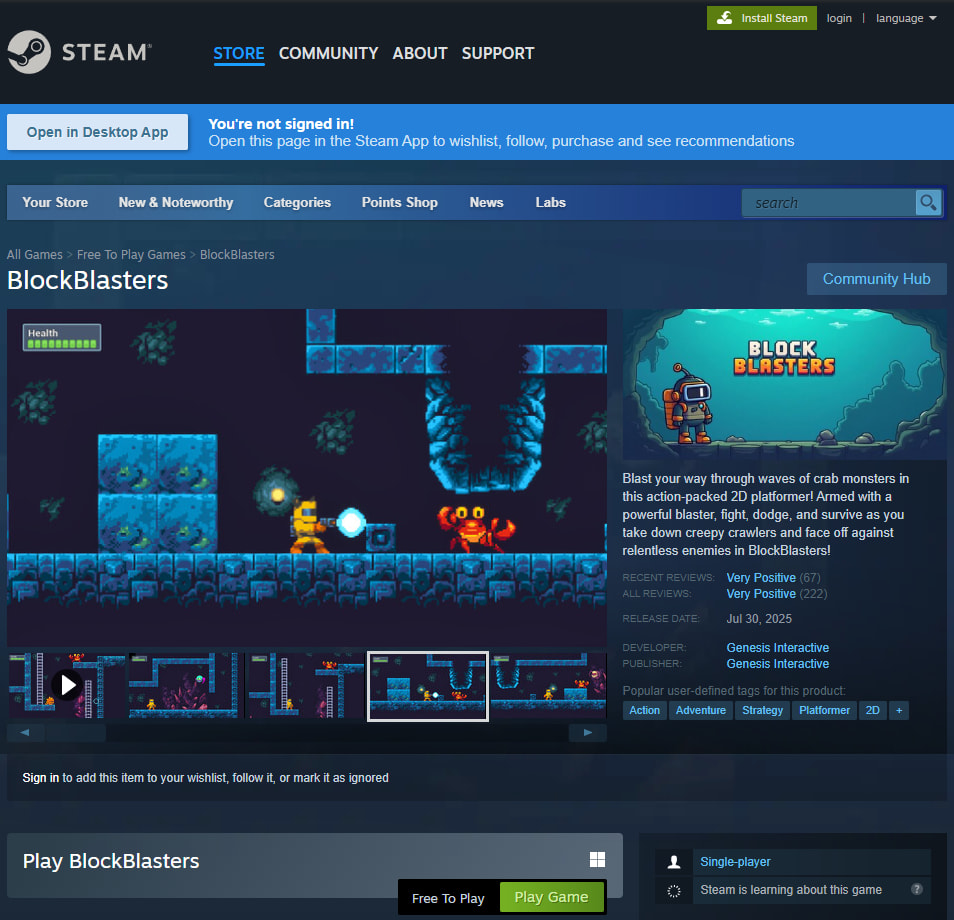
The campaign, which made a total of $150,000, traced to a title named Block Blasters. The game was available on Steam for nearly a month and operated as a fully-fledged cryptodrainer, exploiting Valve's inadequate vetting of indie game uploads.
On September 21, 2025, Twitch and Steam content creator RastaLandTV, who is battling Stage IV Sarcoma, inadvertently broadcast their own victimization live. They were contacted by an individual who offered payment in exchange for streaming a demo of their game, Block Blasters, available directly on Steam. The streamer downloaded and launched the game on air, unknowingly executing a series of payloads that drained their crypto wallet, including funds earmarked for cancer treatment.
Security researcher Karsten Hahn of GDATA and independent analysts from the VX-Underground and crypto-investigation communities quickly mobilized, dissecting the malware and tracing its infrastructure.
The malicious Steam title (ID 3872350) hosted multiple obfuscated payloads, with key components including:
- A batch-based stealer named game.bat (at least 16 variants were found)
- A PyInstaller backdoor
- A StealC binary
- Multiple VBScripts and ZIP archives encrypted with the password “121”
- A Telegram bot for data exfiltration
The malware was designed to evade detection by checking for antivirus processes before deploying its payloads. If only Windows Defender was detected, it proceeded to unpack and execute secondary payloads such as Block1.exe or MegaActionPlatformer.exe, embedded in the v1.zip and v2.zip archives.
Stolen credentials, Steam account data, and crypto wallet details were uploaded to an unprotected server at http://203.188.171.156:30815/upload. The upload server lacked authentication and file size restrictions, allowing researchers to eventually crash the infrastructure by flooding it with large dummy files.
The forensic report compiled by the research collective behind the takedown of Block Blasters reveals that they accessed the command-and-control server used in the attack. Exploiting the absence of security controls, the team extracted victim logs for 478 users, a curated list of crypto-focused Steam users, and malware files and scripts used for reconnaissance, exfiltration, and execution.
They also discovered that the attackers mocked their victims in internal conversations and later deleted the server infrastructure when confronted.
Steam risks
Investigators traced the malware's injection date through SteamDB logs and confirmed that the malicious binaries were live and downloadable for nearly a month. The game had passed Valve's internal checks despite housing multiple archives containing info-stealing malware.
CyberInsider
Worse yet, this isn't an isolated incident. In March 2025, Valve pulled Sniper: Phantom's Resolution, another indie title whose “demo” led users to a malware-laced external executable. Prior to that, PirateFi was removed in February for shipping with embedded malware directly inside its Steam release.
It is generally recommended to avoid running indie game demos without verified developer reputation, and use hardware (cold) wallets to store cryptocurrency.







Leave a Reply