
Check Point Research (CPR) has uncovered a network of GitHub accounts, named the Stargazers Ghost Network, that distributes malware through malicious links embedded in phishing repositories.
This operation, tracked by CPR as Stargazer Goblin, uses multiple GitHub accounts to distribute various malware families and employs tactics to make these repositories appear legitimate.
The network operates as a Distribution as a Service (DaaS), allowing cybercriminals to share and distribute malicious content. CPR researchers, led by Antonis Terefos, identified over 3,000 active “Ghost” accounts within the network. These accounts use actions like starring, forking, and subscribing to repositories to create an illusion of legitimacy, making the repositories seem credible and enticing victims to download malicious content.
Check Point Research
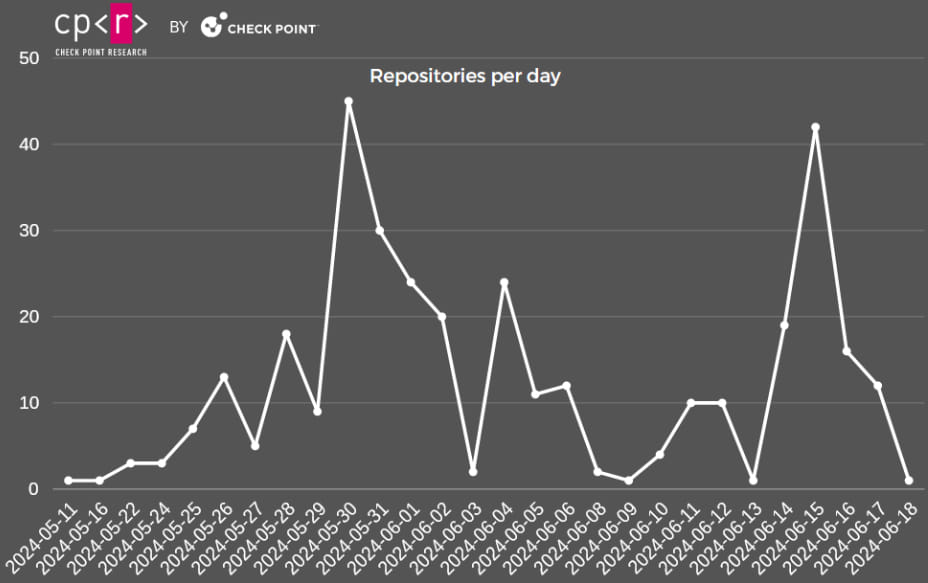
Since August 2022, Stargazer Goblin has been developing this network. An advertisement for this malicious GitHub operation was first published on a dark web forum on July 8, 2023. CPR estimates that Stargazer Goblin earned around $8,000 from mid-May to mid-June 2024, with total earnings potentially reaching $100,000 over the network’s operational lifespan.
Stargazers Ghost Network’s operation
The network uses GitHub to distribute various types of malware, including Atlantida Stealer, Rhadamanthys, RisePro, Lumma Stealer, and RedLine. The malicious activities were discovered in over 2,200 repositories, targeting victims through phishing templates promising increased social media followers or cracked software.
Check Point Research
For example, during a campaign in January 2024, the network distributed Atlantida Stealer via Discord channels, infecting over 1,300 victims in just four days. The repositories targeted individuals seeking to boost their social media presence on platforms like YouTube, Twitch, and Instagram.
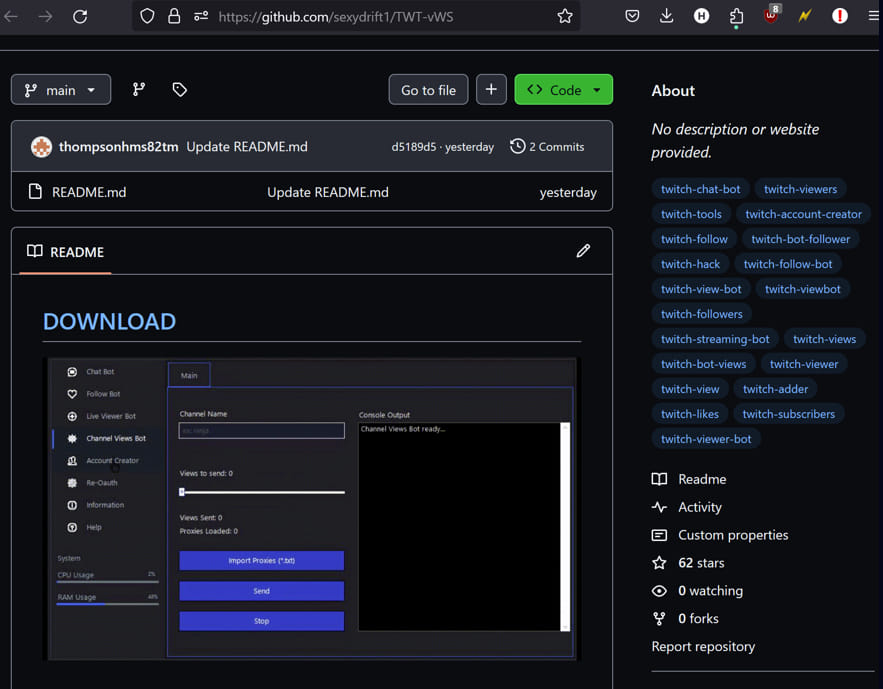
The malicious repositories typically contain README.md files with phishing links redirecting to external websites or GitHub releases with password-protected archives. This tactic hides the malicious content from GitHub’s scanning solutions. The network also uses multiple accounts for different roles, such as creating phishing templates, hosting images, and serving malware, allowing quick recovery from account bans and minimizing operational disruption.
Check Point Research
Infection chain
One notable campaign involved the distribution of the Atlantida Stealer. Victims were lured into clicking on malicious links in GitHub repositories, which redirected them to compromised WordPress sites hosting malicious scripts. These scripts downloaded and executed further malware, including Atlantida Stealer, which exfiltrated user credentials and cryptocurrency wallets.
Another campaign involved Rhadamanthys malware. This campaign used a phishing template titled “RisePro Stealer + HVNC Crack: The Ultimate Cybersecurity Threat,” targeting both threat actors and security researchers. The phishing link redirected victims to download a GO downloader, which then dropped Rhadamanthys malware.







This seems quite inevitable, thanks largely to Google and how they deal with reports.
Several months ago users in the Google Webstore (for extensions) flagged many extensions that are on Github for malware. It wasn’t until recently (within the last few days) Google took action.
Interestingly, if anyone recently tried to flag an extension in the Chrome store, you’ll notice there is no direct option to flag malware. The options are:
1. Content was disturbing
2. Not trustworthy
3. Felt hostile
4. Did not like the content
5. Felt suspicious
6. Not what I was looking for