
Italian cybersecurity firm Cleafy reports a surge of SpyNote infections in Europe, especially during June and July 2023, coinciding with a new campaign targeting multiple European banks.
SpyNote is a dangerous Android malware with a rich feature set, able to track infected devices in real-time, collect SMS and messages, access contact lists, perform keylogging, bypass 2FA protection, and commit on-device bank fraud with automated transactions.
Cleafy says SpyNote is distributed via email or SMS phishing messages sent to targets supposedly from their bank agents, asking them to install what is supposedly a new version of their bank app or a security app that will protect their accounts from malware and fraud. Once nested in the device, the malware will abuse Android’s Accessibility services to automatically grant itself additional permissions required for performing account takeover attacks and on-device fraud.
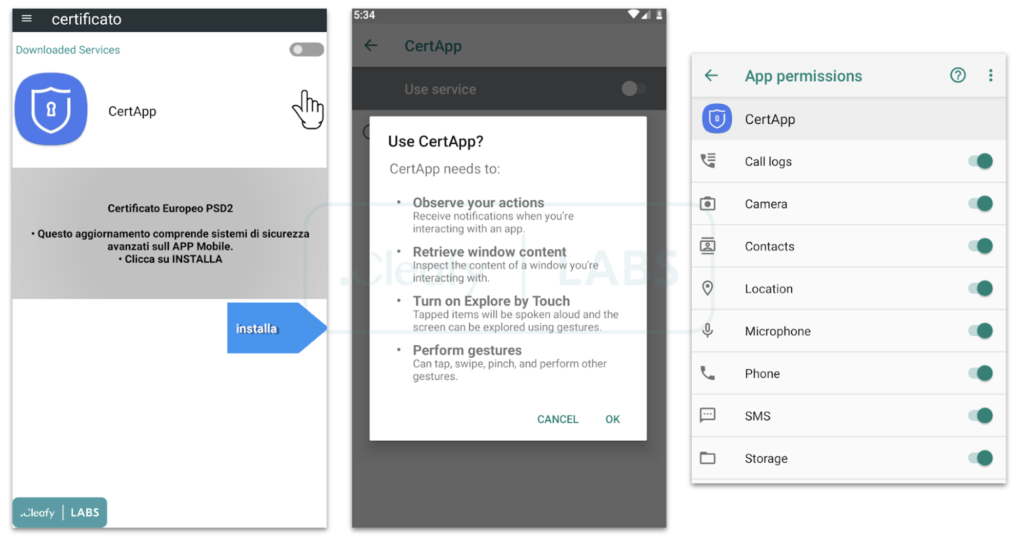
Cleafy
The spyware records user activity, including applications installed on the device, specific app properties, and any text the user writes. It can steal bank credentials, credit card information, and other sensitive data. Furthermore, SpyNote can gather SMS messages, including those containing 2FA codes. It can also access temporary codes generated by the Google Authenticator app, thus bypassing two-factor authentication.
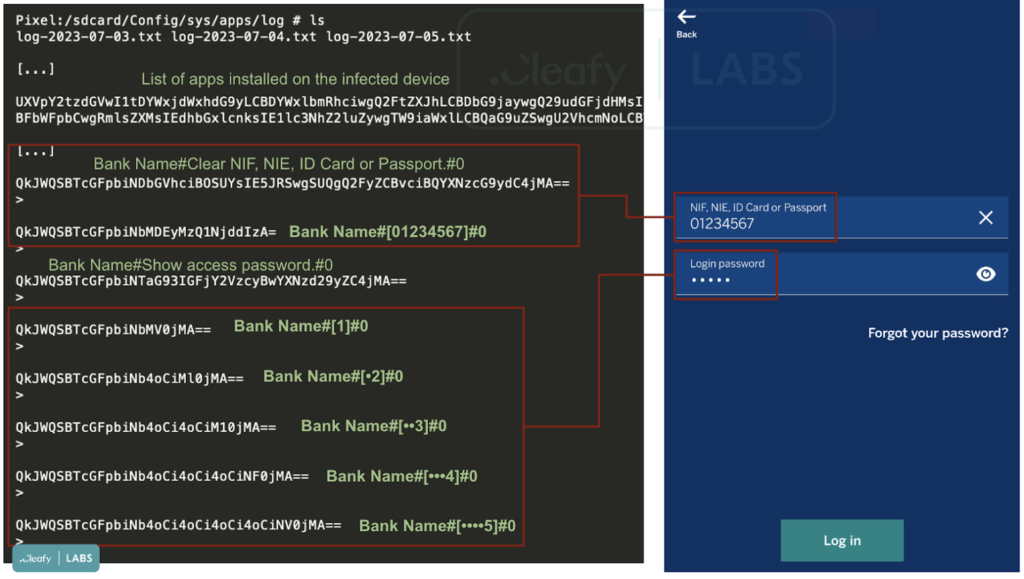
Cleafy
The image below illustrates Spynote intercepting text messages.
B
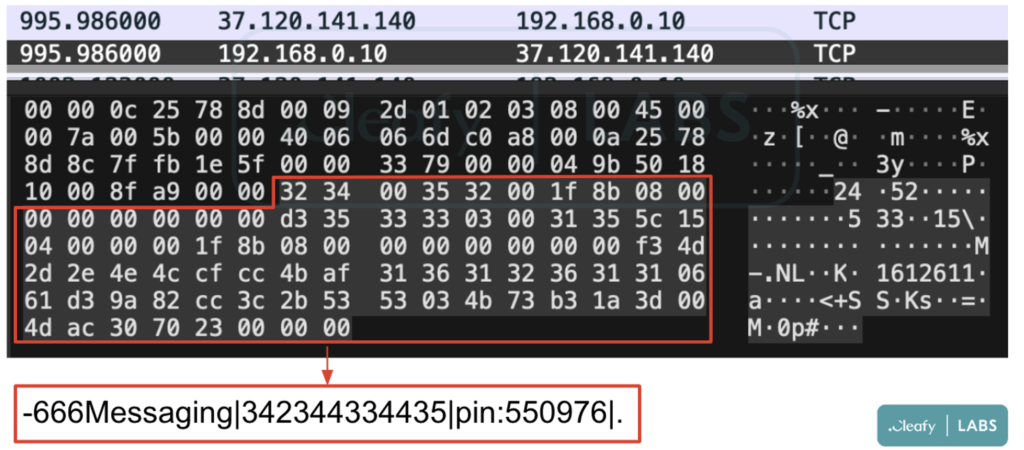
Cleafy
To evade detection, SpyNote utilizes a sophisticated array of strategies and techniques. These include obfuscating its code to confuse and misdirect analysts, embedding redundant or junk code within its strings to slow down static analysis, masking its application icons to thwart manual uninstallation attempts, and conducting checks for emulation or sandboxed environments, thus ensuring its operation is limited to genuine victim devices, and not on security analysts’ boxes.
SpyNote Operations Outlook
Cleafy calls the current SpyNote campaign one of the most aggressive in recent times, and it is unlikely that it will fizzle out any time soon. On the contrary, SpyNote campaigns are expected to expand to more regions, with the inclusion of North American bank customers appearing to be an inevitable progression.
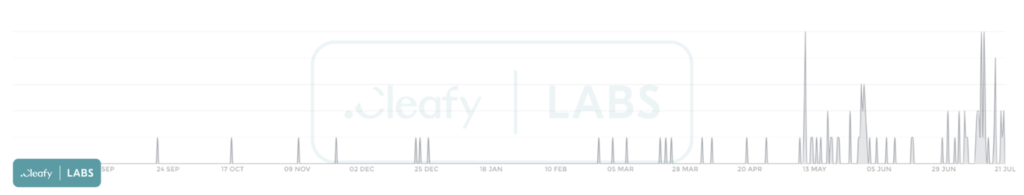
Cleafy
One key thing to note regarding the operators and targeting scope of SpyNote is that the malware’s source code was leaked by its authors in October 2022, just after it had added bank targeting features, as reported in January 2023 by ThreatFabric. This gave access to the malware to many cybercriminals, each setting up their own campaigns backed by the sophisticated trojan tool.
Unfortunately, the fears generated by SpyNote’s code leak regarding the adoption and large-scale use of the sophisticated and highly-capable spyware have been vindicated now, as threat actors appear to adapt and further develop the malware to meet their operational needs.
Related Articles:
- Europe Reacts to Meta’s Chaotic User Data Management
- ‘BidenCash’ Leaks Free Pack of 1 Million US Credit Cards
- New ‘HotRAT’ Malware Disables Antivirus of Software Pirates
- CBDCs (Central Bank Digital Currencies): Profound Privacy Implications
- Malvertizing Network with 12 Billion Daily Bid Requests Taken Down







Leave a Reply