
Researchers from HUMAN have uncovered a complex ad fraud operation named “Merry-Go-Round,” involving two independent rings of websites designed to conceal ad impressions from users and brands. This operation uses pop-under tabs to redirect traffic, generating millions of hidden bid requests daily.
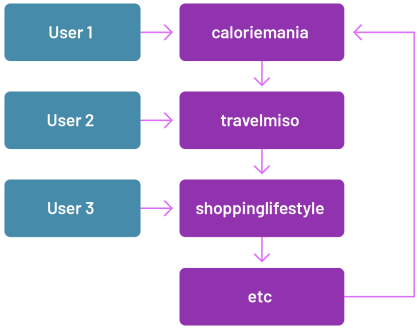
The Merry-Go-Round operation relies on an intricate system where visiting specific websites triggers hidden pop-under tabs that cycle through various domains, accumulating ad impressions unseen by users. This process ensures that directly visiting the involved domains does not trigger the redirection behavior, masking the fraudulent activity from advertisers.
Key points of the scheme include:
- Pop-under tabs redirect traffic automatically, creating a carousel of domains.
- Obscuring referrer information, misleading advertisers about where their ads are displayed.
- Overlay DIV tags and iFrames hijack user clicks to trigger pop-under tabs.
At its peak, Merry-Go-Round generated 782 million bid requests daily. Currently, it accounts for about 200 million bid requests each day, with threat actors continually adding new domains and subdomains to their rings. The sophisticated obfuscation techniques used make this operation notably effective in hiding its activities while maximizing profits by loading up to a hundred ads per domain cycle.
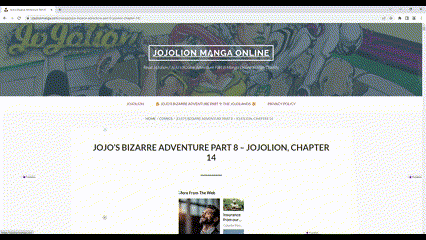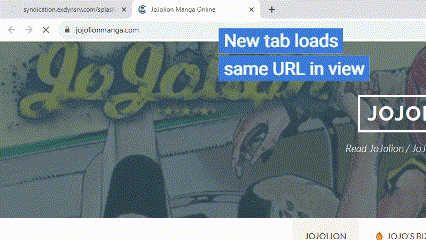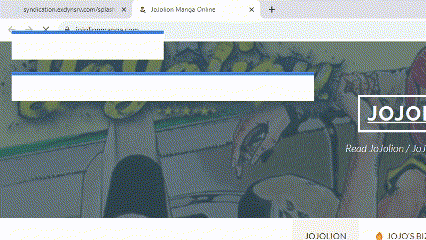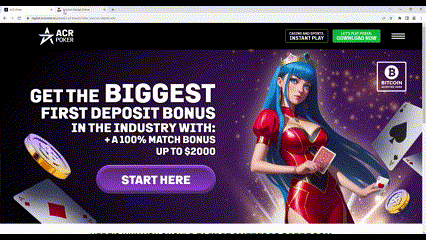
Pop-under and redirection
The fraudulent activity starts when a user visits a website containing content that is generally undesirable for advertisers, such as pornography or pirated material. These sites use overlays to hijack mouse clicks, opening a new tab with the expected content and redirecting the original tab to a Merry-Go-Round domain. This redirection is facilitated by iFrames and overlays with a maximum z-index value of 2147483647, ensuring they sit atop all other page content.
HUMAN
A timer initiates once the Merry-Go-Round domain is loaded, causing the tab to jump to another domain in the ring after about sixty seconds. This cycle continues until the tab is manually closed. In one instance, a single residential IP address generated over 789,000 ad requests in a single day.
HUMAN
Domain cloaking
Merry-Go-Round also employs domain cloaking to deceive advertisers and DSPs (demand-side platforms). When visited directly, the domains appear innocuous, displaying mundane content that doesn't raise brand safety concerns. However, when accessed through forced redirection, these domains show only collections of ads with no actual content. This discrepancy misleads advertisers into believing they are buying ad space on legitimate sites.
To further obscure their activities, the first domain in each ring includes code that instructs search engines not to index the site or follow its links. Additionally, referrer information is removed through specific coding techniques, complicating efforts to trace the fraudulent activity.
The Merry-Go-Round ad fraud operation highlights the increasing sophistication of ad-cloaking schemes. HUMAN's Satori Threat Intelligence Team continues to monitor and capture new domains added to the fraudulent operation's rings.







Leave a Reply