
Signal is adding a new cryptographic layer designed to defend against future quantum computing threats on the protocol's security.
The enhancement, dubbed the Triple Ratchet, integrates a Sparse Post-Quantum Ratchet (SPQR) into the existing Signal Protocol, ensuring forward secrecy and post-compromise security (PCS) even in a post-quantum world.
The research and implementation behind this upgrade were led by Signal engineers with contributions from external researchers at PQShield, NYU, and AIST. Signal first took a step towards quantum resistance in 2023 with PQXDH, an upgraded key exchange protocol. That initiative targeted session initiation, protecting messages against “harvest-now-decrypt-later” attacks. With the introduction of SPQR, Signal now extends quantum resistance to the ongoing lifecycle of conversations, securing not just session establishment but also message ratcheting.
The Signal Protocol, introduced in 2013, underpins the encryption used by billions of users worldwide. It’s not only the foundation of the Signal app, but has also been integrated into WhatsApp, Facebook Messenger, and other platforms. Designed for secure asynchronous communication, the protocol guarantees forward secrecy (past messages remain safe even if keys are later compromised) and post-compromise security (sessions recover from compromise). However, the cryptographic backbone, based largely on Elliptic Curve Diffie-Hellman (ECDH), is vulnerable to future quantum attacks.
ECDH relies on mathematical problems solvable by sufficiently powerful quantum computers, leaving encrypted communications susceptible to retrospective decryption. To mitigate this, SPQR introduces post-quantum Key Encapsulation Mechanisms (KEMs), specifically ML-KEM 768, a NIST-selected standard for quantum-safe key exchange.
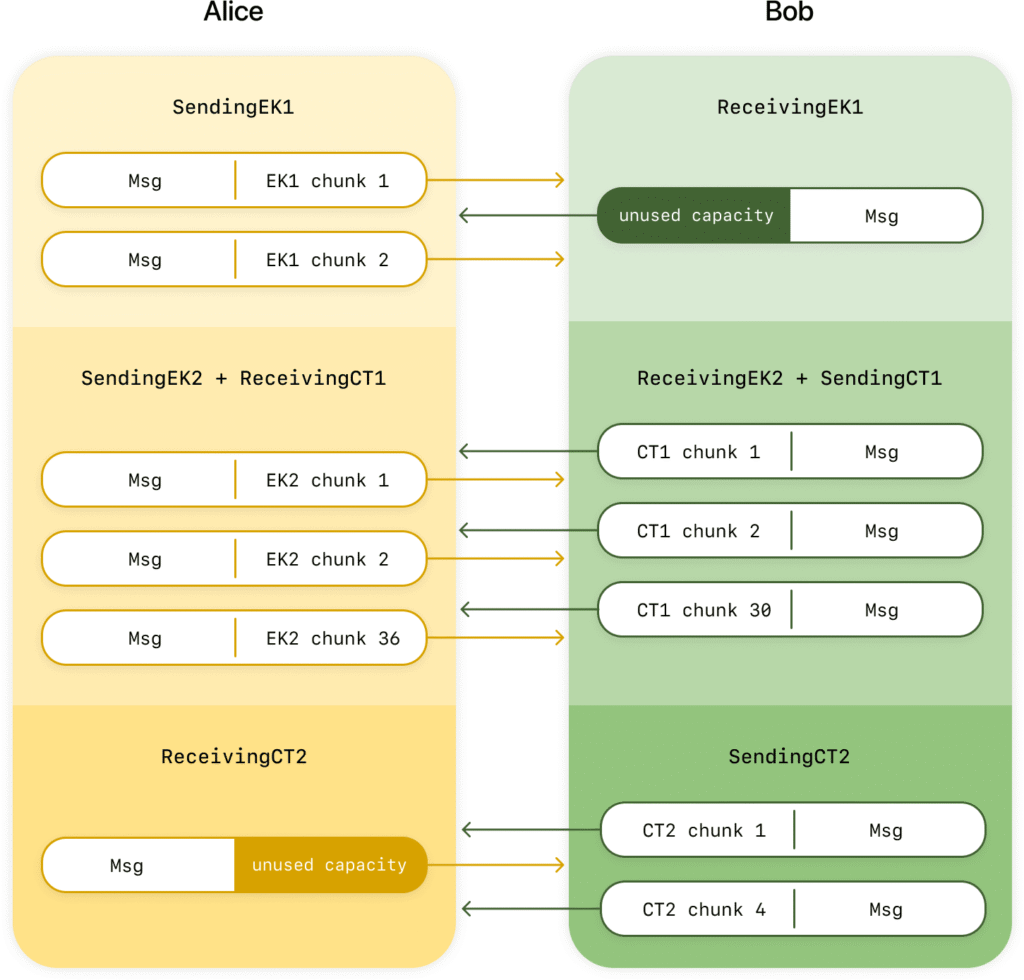
Unlike ECDH, which is compact and synchronous, ML-KEM-based exchanges involve large key and ciphertext payloads (over 1,000 bytes each) and require a careful choreography between participants. To manage this complexity, Signal engineers designed a state machine system where each device tracks its key exchange status and decides how to encode messages accordingly. These exchanges are chunked and protected using erasure coding, allowing for loss-tolerant transmission even on unreliable networks or in the face of active message suppression by attackers.
Signal
SPQR runs alongside the classic Double Ratchet in what Signal now calls the Triple Ratchet. When sending a message, keys from both ratchets are combined using a Key Derivation Function (KDF) to create a hybrid encryption key. This means that an attacker must break both the elliptic-curve and post-quantum layers to compromise a message, an exponentially harder task.
Gradual rollout
The rollout strategy has been designed to avoid disruptions as devices gradually adopt the new protocol. Signal allows graceful downgrades in mixed-version environments, where older clients that do not yet support SPQR can still communicate securely using the existing Double Ratchet. Crucially, these downgrades are cryptographically authenticated, preventing attackers from forcibly downgrading a session.
To eventually ensure that all Signal conversations benefit from post-quantum protection, Signal plans a future update that will archive any non-SPQR sessions once all clients support the new protocol.
The SPQR and Triple Ratchet work builds on academic research presented at Eurocrypt 2025 and USENIX 2025, where Signal researchers introduced the concept of erasure-coded ratchets and evaluated multiple post-quantum protocols, including one based on a custom KEM named Katana. While Katana showed promise, Signal chose ML-KEM for this initial rollout to stick with NIST-standardized algorithms.
From a user perspective, no action is required besides keeping the Signal app up to date. The transition is silent, seamless, and backward-compatible. Over time, as all clients receive updates, every Signal message will benefit from post-quantum security, mitigating the risk of future decryption via quantum computing.







Leave a Reply