
A misconfigured Elasticsearch database belonging to APIsec.ai, a security firm claiming to serve 80% of the Fortune 100, was discovered leaking over three terabytes of highly sensitive customer data — including API scan results, configuration secrets, and personally identifiable information (PII).
The discovery was made by UpGuard’s Greg Pollock during routine scanning for exposed cloud infrastructure. Upon identifying the open instance, UpGuard analysts reviewed the data and found it to contain detailed records of APIsec’s internal scanning infrastructure and results of API security testing for a wide range of customers. APIsec was promptly notified, and the database was secured on the same day.
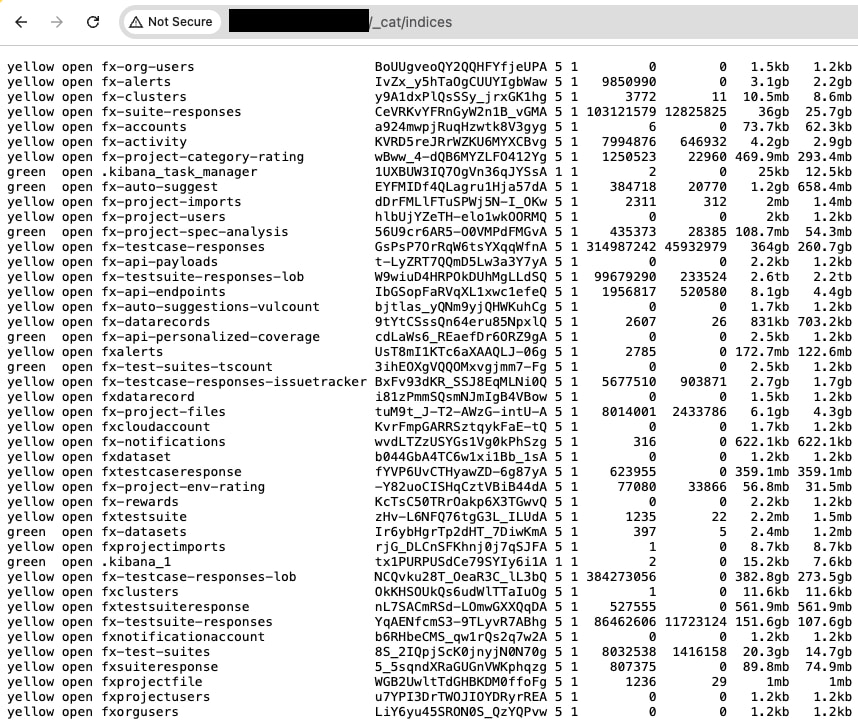
The breach centers around APIsec’s Elasticsearch database, which held indices detailing both the execution and results of automated API test suites. The largest index, labeled fx-testsuite-responses-lob, accounted for more than 99 million records, consuming roughly two terabytes alone. These logs spanned a timeframe from 2018 to 2025 and included verbose request and response data from customer endpoints — effectively creating a high-fidelity map of enterprise APIs, often considered prime reconnaissance material for threat actors.
UpGuard
Headquartered in the United States, APIsec positions itself as a provider of automated API security solutions. Its platform scans customer APIs against known vulnerabilities, particularly those listed in the OWASP API Security Top 10. The company offers both SaaS and self-hosted scanning deployments, the latter of which appeared extensively in the leaked dataset.
Among the exposed data were system credentials, including AWS access keys, GitHub and Slack login information, and configuration data for over 3,700 scanning clusters. A total of 218 of these clusters shared the same AWS key, suggesting a widespread deployment model hinging on a single cloud account. The dataset also included over 1,900 unique scanner authentication keys (FX_KEY) and internal identifiers (FX_IAM), which could enable unauthorized access if still valid.
On the customer side, exposed data included:
- Billing names
- Email addresses
- Company names
- Security configuration metadata such as SSO and MFA status
- License details
This trove of information, if leveraged by attackers, could facilitate both technical exploitation and social engineering at scale.
UpGuard
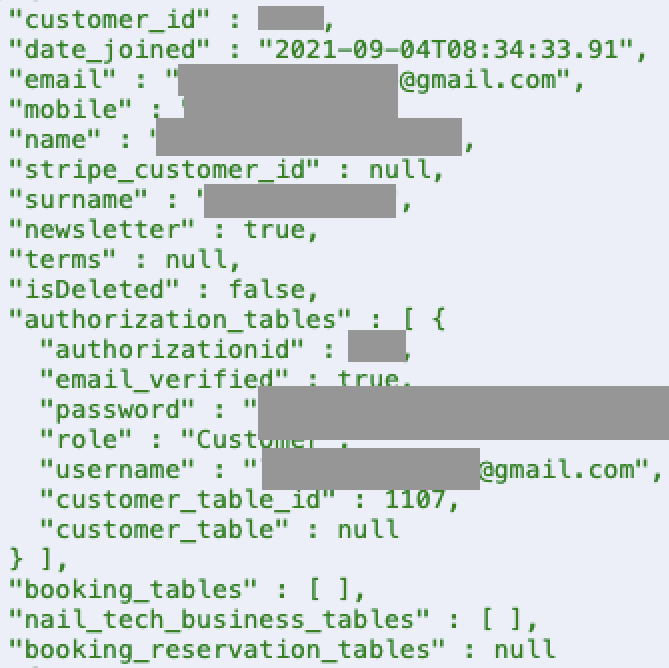
One particularly unusual discovery involved a UK-based nail salon that inadvertently exposed data for 224 technicians, including hashed passwords, emails, and phone numbers. Analysts believe this was likely the result of a misconfigured or unauthenticated API endpoint being scanned, a reminder that smaller organizations can become collateral damage in enterprise-grade security tooling.
The incident highlights the reality of tools designed to enhance visibility and reduce risk becoming liabilities themselves, sometimes acting as central points of failure. As attack surface management becomes a cornerstone of enterprise defense, the need for robust vendor security practices is more critical than ever.







Leave a Reply