
In October 2024, ReliaQuest's Threat Research Team responded to a cyberattack targeting a manufacturing company, identifying the threat group “Scattered Spider” as the perpetrator.
This English-speaking cybercriminal collective, known for its past affiliation with ransomware group ALPHV, has now partnered with the ransomware group “RansomHub.” The attack leveraged social engineering tactics to compromise key employee accounts, which were then used to rapidly encrypt critical systems, highlighting the growing danger of well-executed ransomware campaigns.
Social engineering specialists
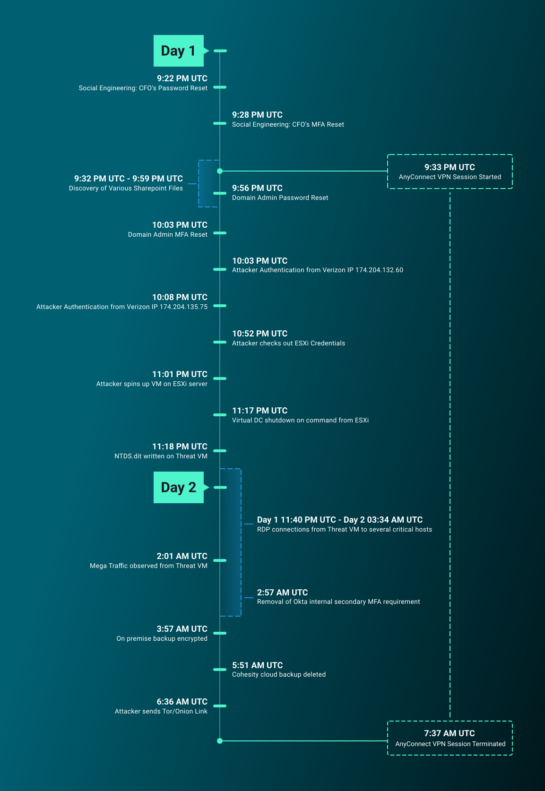
The incident began with Scattered Spider gaining access to the victim's network through two successful social engineering attacks on the organization's help desk. By convincing help desk staff to reset the Chief Financial Officer's (CFO) account credentials, the attackers initially compromised the CFO's account but found it lacked the permissions needed to progress.
Undeterred, they employed the same tactic again to compromise a domain administrator account, providing them with escalated privileges. Within hours of breaching these accounts, the attackers deployed ransomware, targeting the organization's ESXi virtualized environment to encrypt systems and sabotage backups, ensuring maximum disruption.
Reliaquest
ReliaQuest's investigation of the attack revealed several key tactics:
- Social engineering mastery: Scattered Spider successfully compromised multiple employee accounts through persistent social engineering attacks, highlighting vulnerabilities in help desk operations.
- ESXi environment exploitation: The attackers spun up a virtual machine within the victim's ESXi environment to evade detection and execute ransomware, targeting backups to hinder recovery efforts.
- Rapid execution: From initial access to system encryption, the entire attack unfolded within six hours, demonstrating the attackers' efficiency and coordination.
Cybercrime background
Scattered Spider, active since at least May 2022, gained notoriety for its sophisticated social engineering attacks and focus on high-reward targets. Initially involved in lower-level cybercrimes like SIM-swapping and identity fraud, the group evolved into an affiliate of ransomware groups.
Following the disbandment of ALPHV in early 2024, Scattered Spider sought new partnerships, aligning with RansomHub, a ransomware-as-a-service group offering affiliates 90% of attack profits. This partnership marked a shift toward targeting large corporations with more elaborate and financially rewarding attacks.
RansomHub was established around the same time and has quickly risen to prominence in the ransomware ecosystem, overtaking groups like LockBit due to its lucrative affiliate profit-sharing model.
The group's malware has been detected in numerous high-profile attacks since mid-2024, often deploying tactics linked to Scattered Spider, suggesting a strong collaboration between the two. The combination of RansomHub's infrastructure and Scattered Spider's advanced social engineering presents a potent threat to organizations across sectors, particularly those using virtualized environments like ESXi.
Defense recommendations
To mitigate the risk of similar attacks, organizations should implement the following strategies:
- Strengthen help desk security: Enforce strict protocols for resetting credentials, such as requiring secondary authorization for high-privilege accounts, and conduct regular social engineering training.
- Enhance multi-factor authentication (MFA): Avoid using vulnerable methods like SMS-based MFA, and instead deploy more secure alternatives, such as hardware tokens or app-based authentication.
- Harden ESXi environments: Ensure all virtual infrastructure is up to date and restrict access to sensitive areas through smart-card authentication and firewall allowlists.
- Restrict sensitive file access: Limit permissions for critical documents stored in SharePoint or other cloud platforms to prevent attackers from gathering valuable information for lateral movement.
This latest report underscores the ongoing evolution of ransomware tactics and the increasing collaboration between threat actors across language and regional boundaries. Despite the arrest of several Scattered Spider members earlier this year, the group continues to collaborate with Russia-linked ransomware affiliates, exploiting their social engineering expertise to bypass security measures.






Leave a Reply