
This article has been updated with a statement from Telegram below.
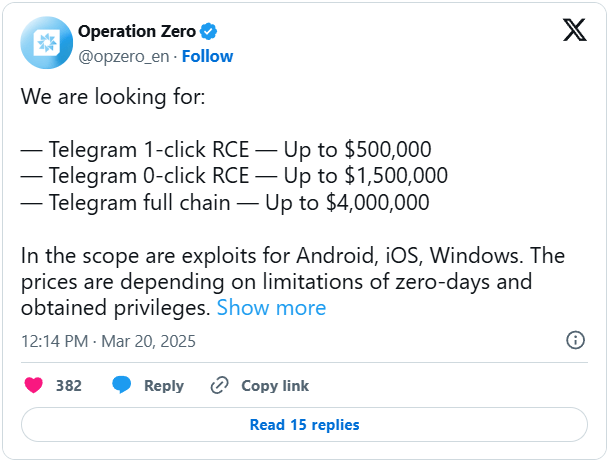
A Russian exploit broker is offering up to $4 million for zero-day vulnerabilities targeting Telegram, underscoring the growing value of messaging app exploits amid rising demand for covert surveillance capabilities.
Operation Zero, a zero-day acquisition company based in Saint Petersburg, posted the bounty this week, publicly seeking remote code execution (RCE) vulnerabilities for Telegram on Android, iOS, and Windows. The firm is offering $500,000 for one-click RCEs, $1.5 million for zero-click RCEs, and up to $4 million for a full exploit chain—potentially enabling attackers to gain full control of a target’s device starting from Telegram.
The unusually high price tag signals both demand and urgency, suggesting that Russian government agencies, among Operation Zero’s primary clients, have a current operational need for Telegram access. Operation Zero works exclusively with Russian private and governmental customers and holds permits to legally operate in the exploit trade. It explicitly refuses submissions of unfinished or unreliable code, requiring fully weaponized zero-days for consideration.
CyberInsider
The bounty is a rare public offer from a market usually shrouded in secrecy. Analysts believe such pricing often reflects real-time intelligence needs from buyers—likely government entities—which are passed down to brokers like Operation Zero. An unnamed source familiar with the market told TechCrunch that prices may be adjusted based on exploit quality, exclusivity, and resell potential, noting, “I don’t think they’ll actually pay full [price] … there’s not any real incentive to not f—k over the exploit writer.”
Telegram’s popularity in Russia and Ukraine makes it a high-value target. The platform boasts hundreds of millions of users worldwide and plays a critical role in information dissemination, particularly during wartime. Despite its perception as a secure messaging app, Telegram does not enable end-to-end encryption by default, and its proprietary cryptographic protocols have faced longstanding criticism from privacy experts.
The timing of Operation Zero’s call for Telegram exploits also coincides with broader concerns over spyware abuse on messaging platforms. Just two days ago, Citizen Lab exposed Paragon Solutions—a spyware vendor tied to Israeli intelligence—for leveraging a zero-click exploit in WhatsApp to deploy its Graphite surveillance tool. Victims included journalists, activists, and humanitarian workers across Europe, Canada, and Southeast Asia.
Paragon’s use of WhatsApp mirrors the kind of operations Russian intelligence services are believed to conduct via Telegram and other apps. Both WhatsApp and Telegram are among the most lucrative targets in today’s zero-day market. Operation Zero’s current price list shows it previously offered $1.5 million for WhatsApp zero-click exploits, while placing Telegram in the same tier—a reflection of its strategic importance.
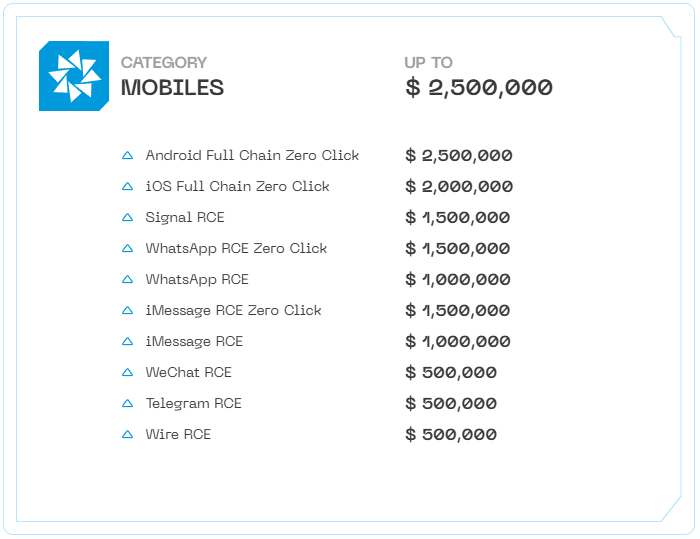
Operation Zero has also offered up to $2.5 million for Android full-chain exploits and $2 million for iOS zero-clicks, as well as competitive payouts for Signal, iMessage, and WeChat vulnerabilities. The firm states on its website that it ensures seller anonymity using PGP encryption and only accepts fully developed, reliable zero-days—discouraging proof-of-concepts or unpolished code.
Telegram statement
After the publication of this article, Telegram provided the statement below to CyberInsider:
Telegram has NEVER been vulnerable to a zero-click exploit. The fact that money is being offered for finding one only shows that they've been unable to. Telegram's open source app code and fully-documented encryption protocols have allowed numerous researchers to verify the integrity of Telegram's security. Further, Telegram is the only major messenger that has verifiable builds for both Android and iOS, allowing anyone to verify the apps published to stores are built from that same code.
Compare that to WhatsApp which has had zero-click exploits discovered at least in January 2024, December 2019 and November 2019. With its closed source code, it's likely there are more to be discovered – by criminals instead of security researchers.
– Telegram spokesperson







Leave a Reply