
Russian hackers of the APT28 group (‘Fancy Bear’) are using new malware named GonePostal, which hijacks Microsoft Outlook to secretly spy on victims and steal data.
According to cybersecurity firm Kroll, which discovered GonePostal in a recent espionage case, the attackers use a combination of modified system files and hidden macros (automated scripts) inside Outlook to create a stealthy backdoor, allowing them to run commands, steal files, and send information, all through normal email traffic.
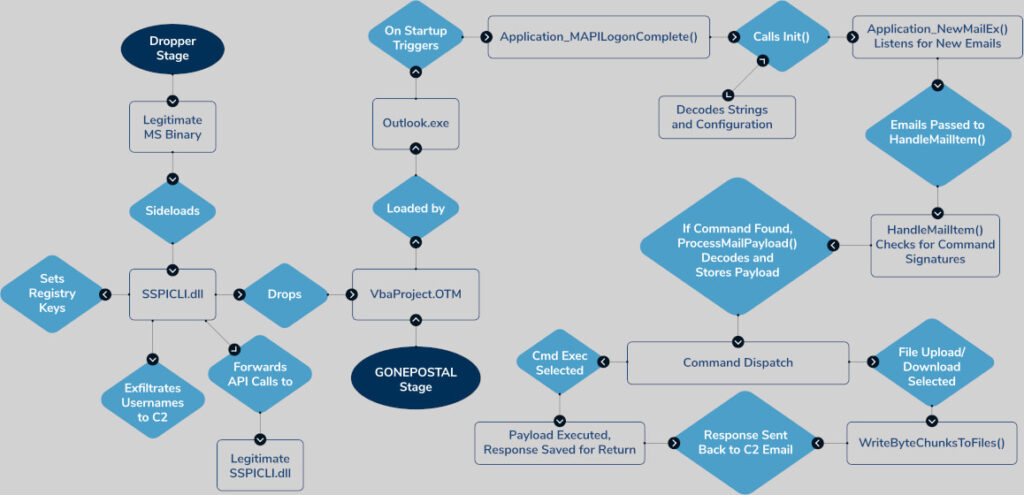
The campaign begins when victims are tricked into running a malicious file that pretends to be a legitimate Windows system component. Specifically, the malware includes a rogue DLL named SSPICLI.dll, which masquerades as a Microsoft-signed file and uses function forwarding to appear legitimate while executing embedded malicious code. This DLL then launches an encoded PowerShell command that copies a malicious file (testtemp.ini) to the Outlook macro folder as VbaProject.OTM.
This file contains password-protected VBA macros that are obfuscated and configured to load automatically at Outlook startup.
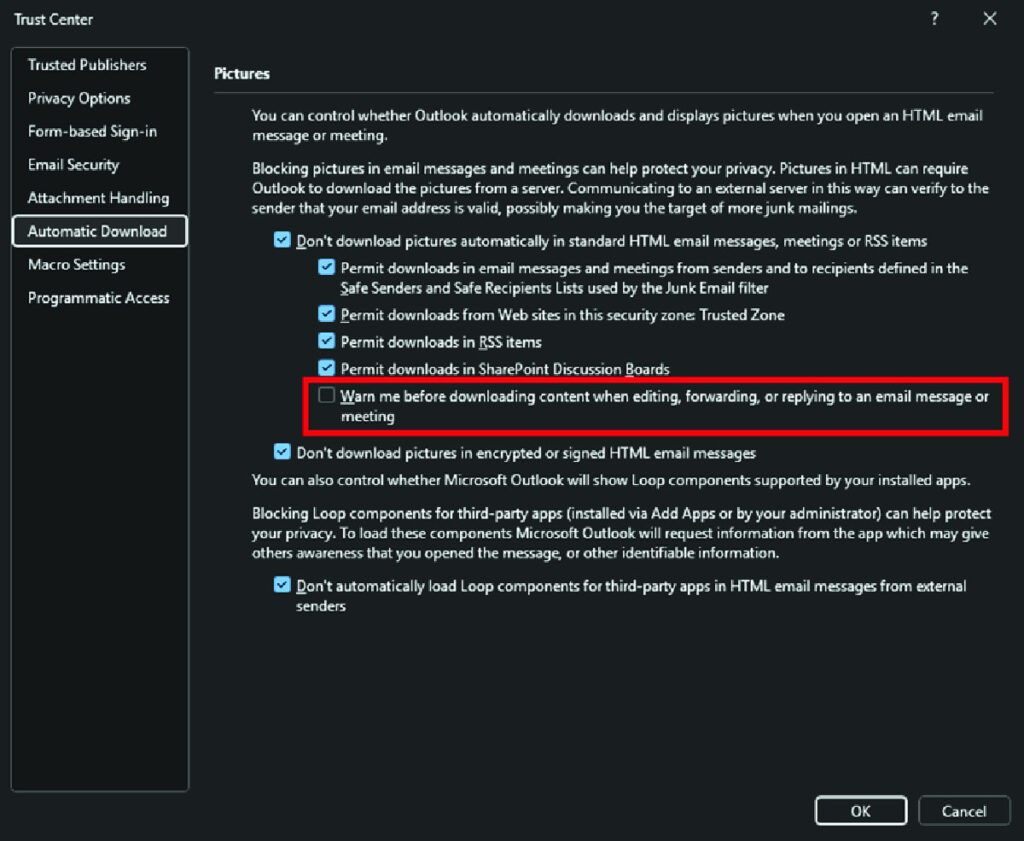
The malware makes subtle changes to the Windows registry to ensure these macros are always loaded without alerting the user. Keys like LoadMacroProviderOnBoot and Security\Level are altered to enable all macros silently. It also disables warning pop-ups that would normally appear when Outlook downloads external content by modifying the PONT_STRING registry value.
Kroll
Once installed, GonePostal turns Outlook into a command center for the attackers. It monitors all incoming emails for hidden instructions, then executes commands that perform the following actions:
- Run system commands and send back the results
- Upload or download files
- Execute tasks without returning results
- Send stolen data back to the attackers via email
These operations are done using regular-looking emails, making them extremely unlikely for security tools to detect.
Kroll
Microsoft Outlook is one of the most widely used email clients in the business world, making it a perfect tool for this kind of stealthy attack. By hiding inside a trusted app and using everyday email traffic, the hackers can operate under the radar, without needing to maintain noisy internet connections or drop additional malware.
Kroll recommends that users disable macros in Microsoft Office apps unless absolutely necessary, and regularly audit their Outlook settings, especially those related to macros and add-ins, to ensure there are no unauthorized changes.







Leave a Reply