
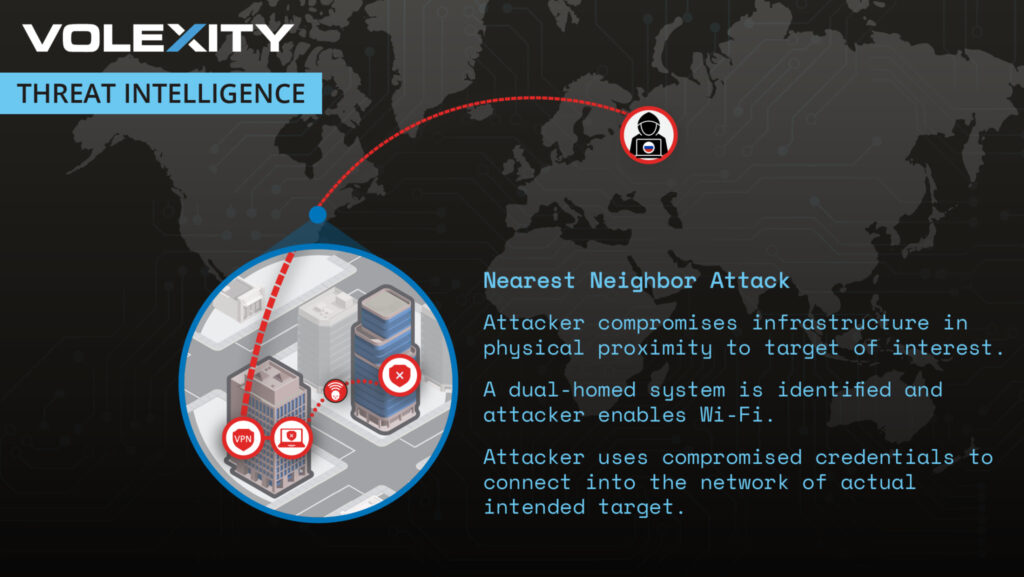
Volexity has uncovered a novel cyber-espionage campaign by the Russian APT group “GruesomeLarch” (also tracked under APT28, Fancy Bear, and Forest Blizzard). The group exploited weaknesses in corporate WiFi networks using what Volexity has termed the “Nearest Neighbor Attack.” This technique allowed the attackers to gain access to sensitive networks from organizations physically adjacent to their targets.
Attack discovery and context
The discovery began in February 2022, just before Russia's invasion of Ukraine, when Volexity detected unusual activity on the network of “Organization A,” an undisclosed client involved in Ukraine-related projects.
Initial investigation revealed that the attackers compromised the organization's enterprise WiFi network despite being thousands of miles away. By targeting nearby organizations, the attackers exploited dual-homed systems — devices connected to both wired and wireless networks — to remotely bridge the gap to Organization A's WiFi.
This campaign underscores how GruesomeLarch targeted Ukraine-related work during a critical geopolitical moment, relying on living-off-the-land techniques and a Windows zero-day privilege escalation vulnerability (CVE-2022-38028) to maintain access.
The techniques and tools observed, including the use of a post-compromise tool known as “GooseEgg,” led Volexity to attribute this campaign to GruesomeLarch with high confidence. The group's meticulous tactics and strategic targeting further reinforce its status as a high-priority cyber-espionage actor linked to Russian state interests.
Anatomy of the “Nearest Neighbor Attack”
GruesomeLarch's operation spanned multiple organizations:
- Initial Access: The attackers used password-spray attacks on public-facing services of Organization A, bypassing MFA by exploiting WiFi systems that only required valid credentials.
- Lateral Movement: After breaching nearby organizations (e.g., Organization B), the attackers targeted dual-homed systems connected to both Ethernet and WiFi networks. These systems acted as entry points to Organization A's WiFi.
- Credential Exploitation: With credentials brute-forced from Internet-facing services, the attackers authenticated into Organization A's network via WiFi access points located near external windows.
The attackers leveraged tools like PowerShell scripts to identify WiFi networks within range, and they used native Windows utilities like Cipher.exe to securely erase forensic traces of their activities.
The attack presented multiple challenges for investigators. For example, files critical to the investigation were deleted using Cipher.exe, securely overwriting data. Attackers also manipulated IP and MAC address logs, eluding detection in conventional systems. Even after detection and remediation, attackers leveraged guest WiFi and other overlooked vulnerabilities to regain access.
Ultimately, detailed wireless controller logs and coordination with adjacent organizations revealed the full scope of the attack. GruesomeLarch had daisy-chained access through multiple organizations — Organization B and possibly Organization C — to achieve their goals.
Broader implications and recommendations
This attack demonstrates the need for enhanced security around WiFi networks, which are often treated with less rigor than email or VPN systems, due to the required attacker proximity. The campaign's use of geographically adjacent organizations as stepping stones highlights a new class of risks for enterprises operating in close physical proximity.
To mitigate similar threats, Volexity recommends:
- Implementing multi-factor authentication (MFA) or certificate-based solutions for WiFi networks.
- Segregating WiFi and wired network access, especially for sensitive resources.
- Monitoring and flagging the use of tools like Cipher.exe and Netsh for potential abuse.
- Custom detection for unusual file activity in directories like C:\ProgramData.
- Reviewing network traffic for unusual SMB file transfers or credential-related exfiltration.







Leave a Reply