
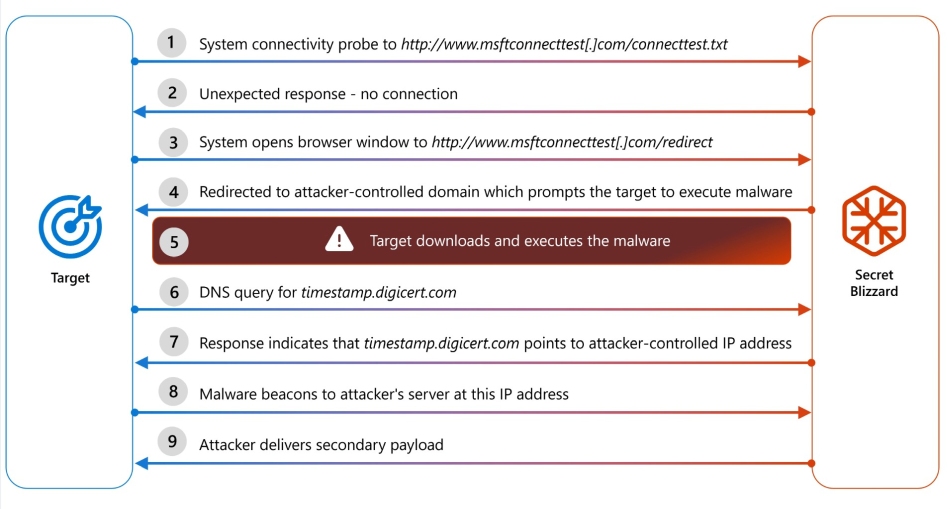
Microsoft Threat Intelligence has uncovered a high-risk cyber-espionage operation conducted by the Russian state-affiliated actor tracked as Secret Blizzard, targeting foreign embassies and diplomatic personnel in Moscow since at least early 2024. The campaign leverages adversary-in-the-middle (AiTM) access via local internet service providers to deploy custom ApolloShadow malware and exfiltrate sensitive diplomatic data.
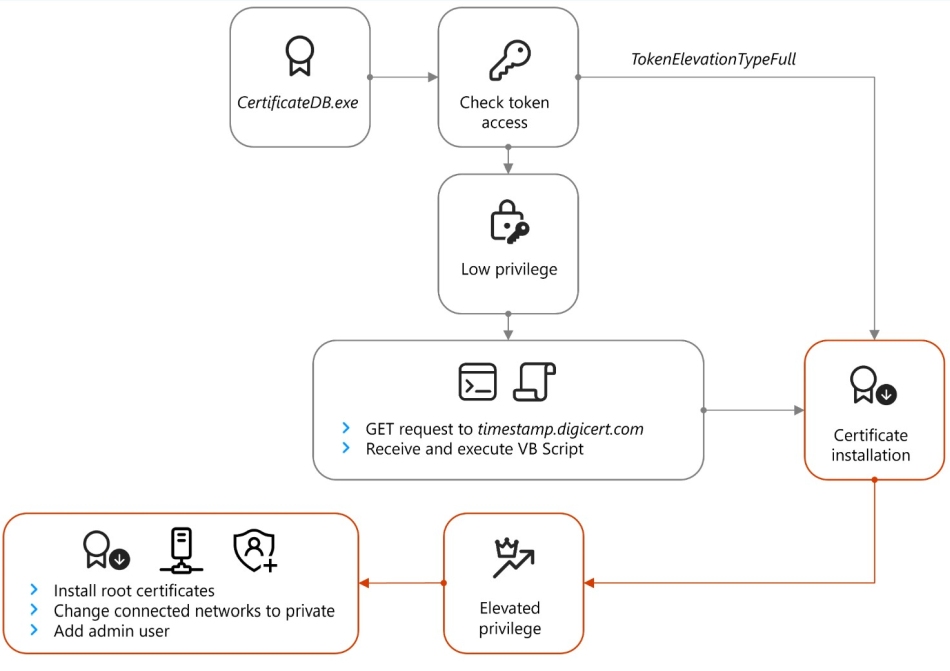
The attackers exploit Russia’s mandated surveillance infrastructure — such as the System for Operative Investigative Activities (SORM) — to intercept traffic at the ISP level. Victims are coerced into trusting fake root certificates masquerading as antivirus software, which strip encryption and enable persistent access via ApolloShadow implants installed on embassy devices. This marks the first confirmed use of ISP-level AiTM positioning by Microsoft researchers targeting diplomatic targets.
Microsoft
Secret Blizzard, attributed by CISA to Russia’s FSB Center 16, has been observed weaponizing infrastructure from other actors (including Storm‑0156) to stage multi-phase espionage intrusions in prior campaigns across regions like Afghanistan and South Asia.
Microsoft’s blog post provides detailed indicators of compromise — including domains like kav‑certificates[.]info, IP 45.61.149.109, and the ApolloShadow SHA256 hash — and outlines detection queries and mitigation steps tailored for enterprise defenders. Recommendations include routing diplomatic traffic through encrypted tunnels or satellite-based providers outside hostile jurisdictions, and employing endpoint protections such as Microsoft Defender with attack surface reduction rules and automated remediation capabilities.
Microsoft
The campaign underscores an alarming shift in espionage tactics: rather than relying solely on malware deployment or phishing, highly resourced actors are now manipulating national telecommunications infrastructure to intrude on sensitive targets.







Leave a Reply