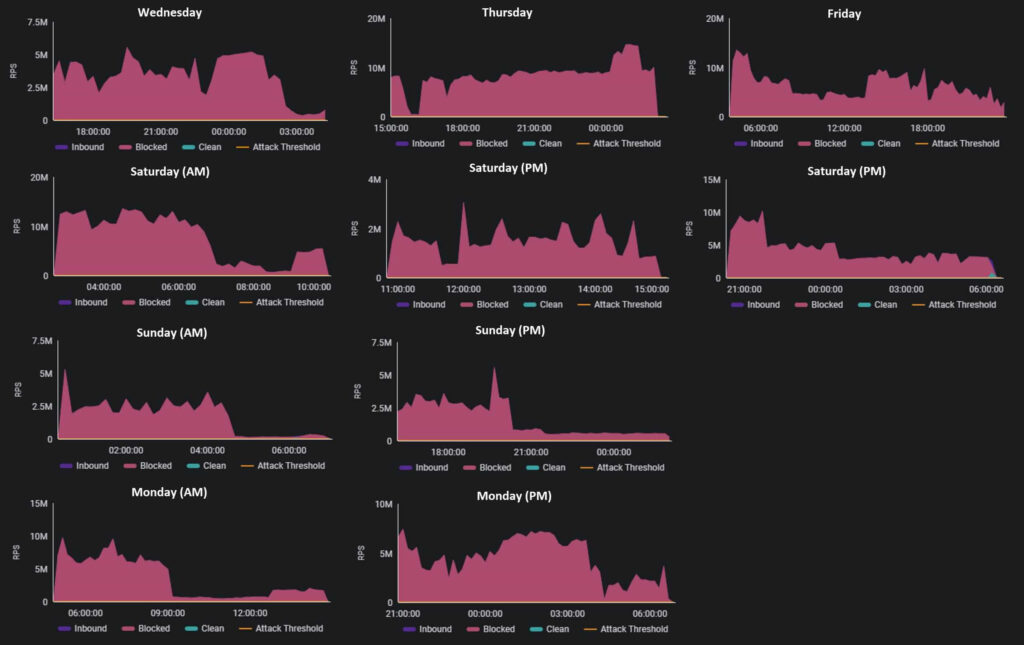
A massive Distributed Denial of Service (DDoS) attack campaign has been attributed to the hacktivist group SN_BLACKMETA, targeting a financial institution in the Middle East. Over six days, the attack sustained an average of 4.5 million requests per second (RPS), peaking at an unprecedented 14.7 million RPS.
The DDoS attack campaign, documented by Radware, consisted of multiple waves spanning four to twenty hours each, culminating in 100 hours of sustained attack time. Despite the barrage, Radware’s Web DDoS Protection Services successfully mitigated over 1.25 trillion malicious requests, allowing 1.5 billion legitimate requests to proceed.
Radware
Attribution to SN_BLACKMETA
The attack was publicly announced by SN_BLACKMETA on its Telegram channel days prior to its execution. This group, with potential ties to Sudan and operating possibly from Russia, has a history of targeting entities seen as adversaries to the Palestinian cause. SN_BLACKMETA has utilized the InfraShutdown premium DDoS-for-hire service, which boasts military-grade privacy and nation-state level disruption capabilities.
SN_BLACKMETA emerged on the cyber warfare scene on November 14, 2023, with an ideological stance supporting the Palestinian cause. The group quickly escalated its activities, targeting infrastructures across Israel, Canada, Saudi Arabia, and beyond. Key attacks included those on the International Airport of Azrael and the Saudi Ministry of Defense.
In early 2024, SN_BLACKMETA expanded its operations to include targets in France, UAE, and significant Western entities such as Microsoft and the Internet Archive. The group is led by the figure known as “Great Leader DarkMeta,” who uses social media to publicize and validate their attacks, thereby boosting the group's visibility and support.
SN_BLACKMETA's attacks often align with those previously claimed by Anonymous Sudan, another pro-Palestinian hacktivist group. Both share similar ideological motivations, target selections, and attack methodologies. The timing and nature of their attacks suggest a potential overlap or collaboration between the groups.
The origins of SN_BLACKMETA may be linked to the ongoing conflict in Sudan, which has seen the Rapid Support Forces (RSF) clash with the Sudanese Armed Forces (SAF). The group’s animosity towards the UAE could be driven by allegations of UAE’s support for the RSF, a claim denied by the UAE but one that aligns with SN_BLACKMETA’s target choices.
Launched by Anonymous Sudan, the InfraShutdown service markets itself as a top-tier DDoS-for-hire service, capable of executing high-scale RPS Web DDoS attacks. This service is likely the source of the recent attack on the Middle Eastern financial institution, given its capacity and sophistication.
Implications and recommendations
The SN_BLACKMETA attack demonstrates the evolving threat landscape of cyber warfare. To defend against such sophisticated and prolonged DDoS attacks, organizations must employ robust Web DDoS mitigation solutions with substantial capacity and advanced differentiation capabilities.
Key defensive measures include:
- Deploying high-capacity DDoS protection services capable of handling peak traffic volumes and sustained attack rates.
- Ensuring rapid differentiation of legitimate traffic to maintain service availability during an attack.
- Regularly updating defense mechanisms to stay ahead of emerging threats and attack methodologies.
The rise of groups like SN_BLACKMETA underscores the importance of understanding and preparing for ideologically motivated cyber threats, which continue to target critical infrastructures globally.







Leave a Reply