
HP Threat Research reports a new twist in the tactics of the notorious Raspberry Robin malware, signaling an evolution in cybercriminal strategies that targets Windows users with sophisticated obfuscation and evasion techniques.
Initially identified in late 2021, Raspberry Robin has been a persistent threat primarily to technology and manufacturing sectors but has since widened its scope to become a significant concern for enterprises at large.
The latest development in the Raspberry Robin saga involves the utilization of Windows Script Files (WSF) to spread the malware. Unlike its previous propagation methods, which included removable media such as USB drives and various web downloads, the attackers have now turned to WSF. These script files, integral to administrative and legitimate software operations within Windows for task automation, have been hijacked by cybercriminals to deploy the malware. This shift underscores not only the adaptability of threat actors but also their intent to leverage less scrutinized vectors for malware distribution.
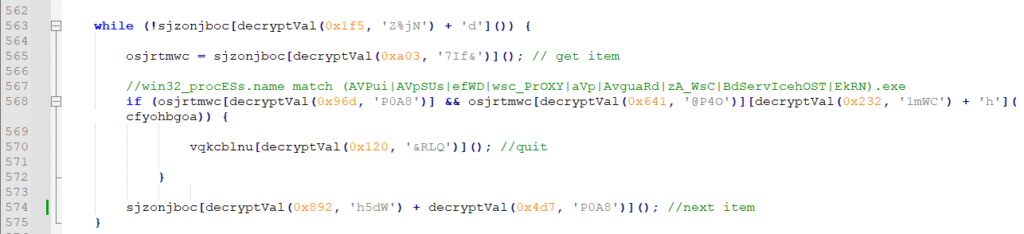
Windows Script Files serve as a potent vehicle for the malware due to their ability to support multiple scripting languages, which are interpreted by the built-in Windows Script Host. This characteristic is exploited to deliver highly obfuscated scripts laden with anti-analysis and virtual machine detection techniques. These measures ensure the malware evades detection by antivirus solutions and complicates analysis by security researchers. In the case of Raspberry Robin, the scripts act as a downloader for the malware, engaging in a series of checks to verify the environment is not a sandbox before executing the payload.
HP
Raspberry Robin distinguishes itself through its extensive use of obfuscation and evasion, communicating with command and control servers over Tor and capable of deploying additional malicious payloads. This versatility makes it a valuable tool for attackers, enabling the distribution of various malware families and serving as a precursor to ransomware attacks.
The infection methods employed by Raspberry Robin have evolved significantly since its inception. Initially spreading via USB devices with malicious shortcut files, the malware later utilized archived files hosted on platforms like Discord and malicious web downloads. These methods, characterized by their innovative abuse of legitimate services and software, highlight the malware's dynamic approach to compromising systems.
The transition to Windows Script Files reflects a calculated move by cybercriminals to exploit the dual nature of these files for both legitimate and malicious purposes. By doing so, they aim to blur the lines between benign and harmful software, complicating detection efforts. The files, once downloaded from attacker-controlled domains, initiate a downloader script replete with obfuscation and anti-analysis tactics. These scripts are not immediately recognized as malicious by antivirus programs, as evidenced by a 0% detection rate on VirusTotal at the time of analysis.
Security professionals and researchers are advised to prioritize the early detection and mitigation of Raspberry Robin, given its potential as a vector for more damaging attacks. The HP Threat Research team has made available indicators of compromise, YARA rules for detection, and Python scripts for automated analysis to aid the security community in combating this threat.







Leave a Reply