
A recently disclosed vulnerability in the RADIUS protocol allows attackers to forge authentication responses, posing a significant risk to network security. This flaw, identified by researchers from UC San Diego, exploits a cryptographic weakness in the protocol's integrity check.
RADIUS (Remote Authentication Dial-In User Service) is an authentication protocol widely used since the 1990s. It handles authentication, authorization, and accounting (AAA) for users accessing network resources. Despite its age, RADIUS remains prevalent in networking environments, from simple switches to complex VPN solutions, and has been adopted by cloud services for role-based access control.
Flaw discovery and details
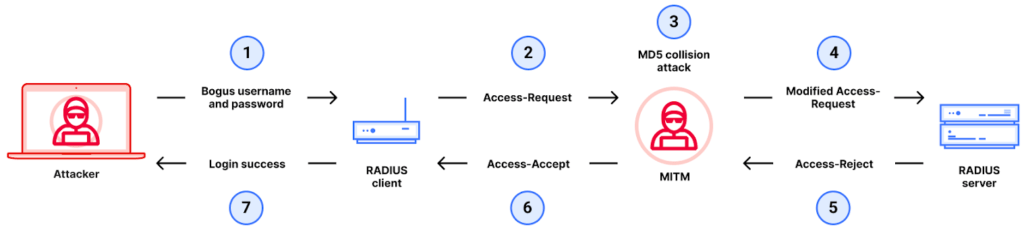
The vulnerability, cataloged as CVE-2024-3596 and detailed by CERT Coordination Center (CERT/CC) on July 9, 2024, allows an attacker to spoof RADIUS responses if the Message-Authenticator attribute is not enforced. This flaw stems from the use of a cryptographically insecure MD5 hash function to validate responses from RADIUS servers, enabling chosen-prefix collision attacks.
The research team demonstrated that attackers with network access can intercept and manipulate RADIUS response packets. By exploiting the MD5 weakness, they can transform an Access-Reject response into an Access-Accept response, effectively bypassing authentication without knowing the shared secret between the RADIUS client and server. This vulnerability is particularly concerning due to RADIUS's extensive use in authenticating users and devices across various network infrastructures.
Cloudflare
Impact on network security
The flaw affects multiple modes of RADIUS authentication, including Password Authentication Protocol (PAP), Challenge-Handshake Authentication Protocol (CHAP), and Microsoft's CHAP (MS-CHAP). However, modes using the Extensible Authentication Protocol (EAP), which requires the Message-Authenticator attribute, are not vulnerable. The use of TLS (Transport Layer Security) or DTLS (Datagram Transport Layer Security) encryption can also mitigate these attacks, although RADIUS over TCP remains susceptible to advanced man-in-the-middle scenarios.
Alan DeKok, developer of FreeRADIUS, emphasized that many Access-Request packets lack authentication or integrity checks, enabling attackers to exploit the chosen-prefix collision vulnerability and modify response packets. More info is available on this Cloudflare report.
Mitigation measures
Manufacturers and network operators need to take immediate action to mitigate this vulnerability:
- Vendors should ensure their RADIUS implementations, such as FreeRADIUS, are updated to the latest versions requiring the use of the Message-Authenticator attribute.
- Network operators should enforce TLS or DTLS encryption for RADIUS communications to secure the protocol from unauthorized access.
- Isolate RADIUS traffic within restricted-access management VLANs or secure VPN tunnels to limit exposure to potential attackers.







Leave a Reply