Quishing—QR code phishing—is a rapidly evolving threat, with the latest iteration involving ASCII-based QR codes to evade detection.
Check Point's researchers identified this new campaign, which uses HTML and ASCII characters to create QR codes, evading typical OCR (Optical Character Recognition) detection.
Evolution in QR code phishing
Check Point reports that the campaign began in late May, with over 600 related emails detected. This evolution follows previous quishing methods, starting with standard MFA authentication requests and advancing to conditional routing and custom targeting. The current trend manipulates QR codes using HTML and ASCII characters to bypass OCR engines, which traditionally detect malicious content in image-based QR codes.

Check Point
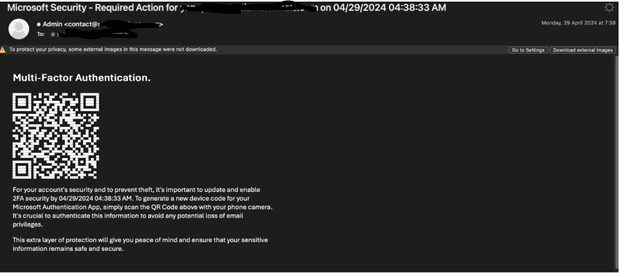
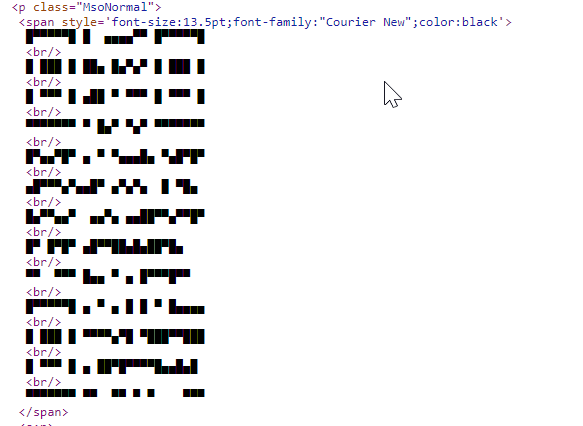
The manipulated QR codes are created using small blocks of HTML and ASCII characters, making them appear as QR codes in emails while remaining undetectable to OCR systems. These ASCII-based codes can be configured to include malicious links, leading to phishing websites or prompting users to re-authenticate sensitive information like MFA or financial data.
Examples of these emails typically request re-authentication, with the QR code containing ASCII characters to bypass security systems.
Check Point
This new technique represents the third evolution of QR code phishing:
- Initial phase: Standard MFA verification codes asking users to scan QR codes to reset MFA or access financial data.
- Second iteration: Conditional routing attacks, where the QR code link adapts based on the user's device, and custom campaigns dynamically include company logos and correct usernames.
- Current phase (QR Code 3.0): ASCII-based manipulation campaigns that evade OCR detection, complicating efforts for security systems to identify and block malicious emails.
Check Point
Given the widespread use of QR codes for authentication and access control, the entities affected by these sophisticated phishing attacks range across various sectors. The impact of these attacks could lead to compromised credentials, unauthorized access to sensitive data, and financial losses.
Defense tips
To defend against these advanced phishing techniques, Check Point recommends the following practices:
- Security systems should automatically decode QR codes embedded in emails and analyze the URLs for malicious content.
- Utilize security measures that rewrite the QR code in the email body and replace it with a safe, rewritten link.
- Employ security products that use advanced AI to analyze multiple indicators of phishing beyond just the QR code itself.
The evolution of quishing highlights the constant cat-and-mouse game between threat actors and cybersecurity defenders. As hackers innovate to bypass existing security measures, it's crucial for organizations to stay ahead by adopting advanced technologies and best practices to protect against emerging threats.







Leave a Reply