
Multiple credible threat monitoring services and malware analysts report that QBot (Qakbot) is back to mass-distributing malicious emails to potential targets.
QBot is a malware botnet specializing in establishing initial access on computers, typically via malspam carrying laced attachments. It then monetizes this access by selling it to malware operators, ransomware affiliates, or threat actors who utilize QBot to exfiltrate data from compromised systems.
RestorePrivacy reported about the takedown of QBot in late August 2023, which was the largest in the botnet’s 25-year history. As we explained then, QBot’s operators remained free to regroup and rebuild just like Emotet did in the past, so the chances of the threat returning remained high. Regrettably, Microsoft Threat Intelligence confirmed this prediction, reporting over the weekend that QBot launched a new phishing campaign targeting the hospitality industry, using a bogus IRS notice as bait.
The PDF attachment used in the phishing emails urges recipients to download the file in order to view it. In reality, that file is an MSI executable that loads the QBot DLL payload into memory for AV evasion. Microsoft’s analysts reported that this DLL has a recent build date, and it switched to using AES encryption for its strings, indicating an effort to make the payload stealthier.
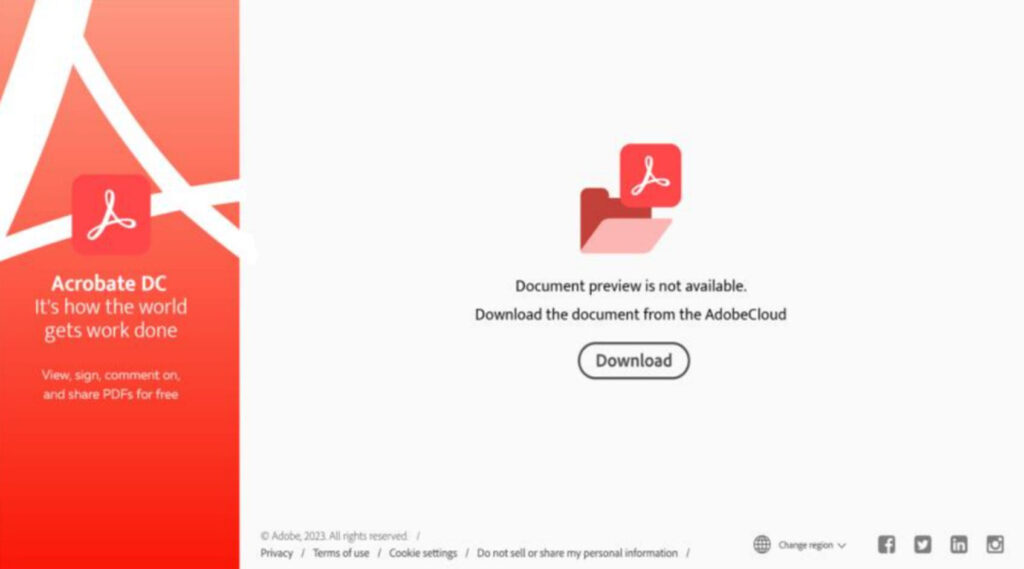
Microsoft Threat Intelligence
Information that was made available to RestorePrivacy in late September 2023 indicated that the law enforcement operation, code-named “Operation Duck Hunt,” only managed to map and take down roughly 80% of the botnet’s infrastructure, leaving behind a good enough starting point to make a potential rebuilding effort worthwhile.
However, it appears that the botnet’s operators took their time with the rebuilding process, potentially to ensure that their servers will be adequately protected from similar takedown attempts this time. Meanwhile, many of the malicious actors that were traditionally served by the QBot network had pivoted to using DarkGate, a highly capable and dangerous malware loader and info-stealer.
What does the QBot return mean
The return of QBot practically means elevated risk for internet users, and depending on the second-stage payload delivered via the attacks, the threat ranges from personal and financial data theft to data-encrypting ransomware attacks.
It is currently too early to tell if QBot will manage to return to its former size or if this will be a failed attempt to recreate the botnet, but out of an abundance of caution, users should be vigilant for phishing emails, unsolicited communications, and even reply-chain hijacks that are far trickier to spot.
When downloading files from the internet, it is a good idea to scan them on your AV tool before executing them. Most security tools today should catch the old threat even if its authors implemented evasion-enhancing refinements in the code.







Leave a Reply