
The second day of Pwn2Own Berlin 2025 wrapped up with another wave of critical zero-day exploits and $435,000 in rewards, bringing the contest total to $695,000.
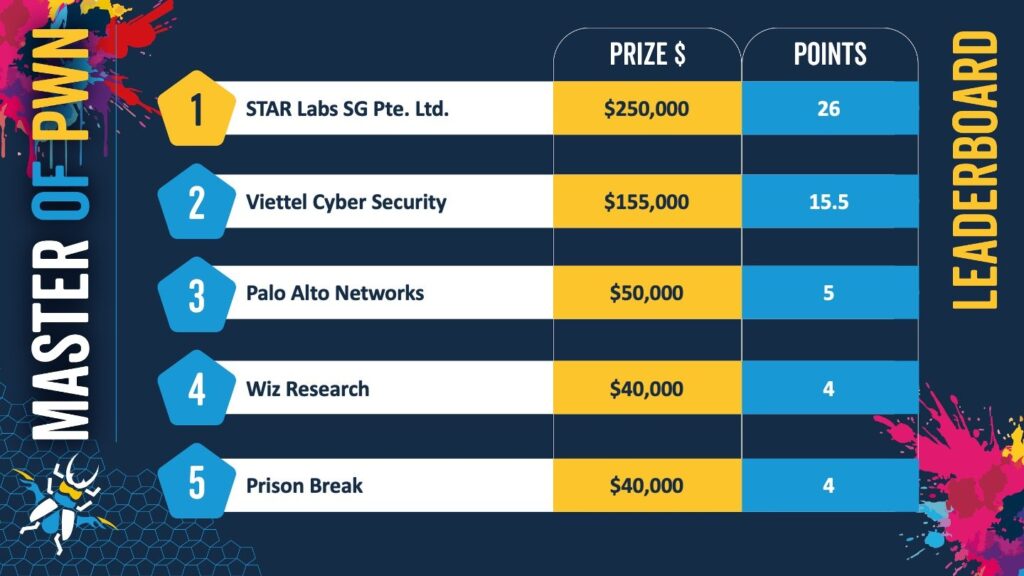
STAR Labs solidified its dominance on the leaderboard, while researchers demonstrated successful exploits across major platforms including Microsoft SharePoint, VMware ESXi, Mozilla Firefox, and several AI systems.
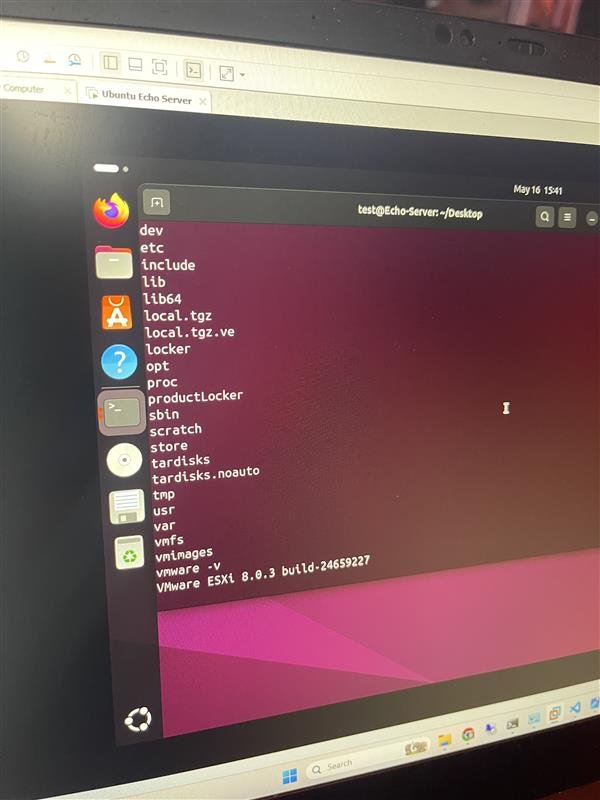
Among the standout achievements of the second day of the competition was the first-ever successful VMware ESXi exploit in Pwn2Own history. Nguyen Hoang Thach of STAR Labs SG identified and leveraged a single integer overflow vulnerability to compromise the hypervisor, earning $150,000 and 15 Master of Pwn points. This high-impact exploit reinforces the strategic focus attackers are placing on virtualization infrastructure.
ZDI
The Microsoft SharePoint category also saw a major win, with Dinh Ho Anh Khoa of Viettel Cyber Security chaining an authentication bypass with an insecure deserialization bug to gain unauthorized access. His effort netted $100,000 and added 10 points to Viettel’s tally. SharePoint, widely used by enterprises as a collaboration and document management platform, represents a valuable target given its integration with Microsoft 365 and widespread corporate adoption.
Browser security was put to the test by Edouard Bochin and Tao Yan from Palo Alto Networks, who exploited Mozilla Firefox using an out-of-bounds (OOB) write. Their work earned $50,000 and demonstrated ongoing risks in client-side software even amid years of hardening efforts.
Artificial intelligence systems remained in the spotlight following their debut on Day One. A significant win came from Benny Isaacs, Nir Brakha, and Sagi Tzadik of Wiz Research, who exploited Redis in an AI context via a use-after-free (UAF) vulnerability. Their effort brought in $40,000 and showed how machine learning infrastructure — often backed by traditional server-side tech — remains vulnerable in novel contexts.
The NVIDIA Triton Inference Server, already a contested target on Day One, faced renewed scrutiny. Ho Xuan Ninh and Tri Dang from Qrious Secure delivered the first full win against the platform, chaining four distinct bugs to compromise the AI system. Their originality was rewarded with $30,000 and 3 Master of Pwn points. Another Triton attempt by FuzzingLabs’ Mohand Acherir and Patrick Ventuzelo resulted in a bug collision — the vulnerability had already been reported to NVIDIA but remained unpatched — yielding a partial reward of $15,000.
Virtualization software continued to be a hot target, with Viettel Cyber Security using another out-of-bounds write to escape Oracle VirtualBox’s guest environment, earning $40,000. Meanwhile, Gerrard Tai of STAR Labs executed a local privilege escalation on Red Hat Enterprise Linux using a UAF flaw, adding $10,000 and further consolidating STAR’s lead.
Not every attempt succeeded. Sina Kheirkhah of the Summoning Team, who was first to exploit an AI system in Pwn2Own history yesterday, fell short in both his SharePoint and VirtualBox entries due to time constraints, though he remains a strong presence in the competition.
ZDI
Trend Micro’s Zero Day Initiative (ZDI), which operates Pwn2Own, confirmed that 20 unique zero-days were demonstrated during Day Two alone. With another full day remaining and only $305,000 needed to hit the $1 million milestone, the inaugural Berlin edition is on track to set records in both scope and payout.







Leave a Reply