
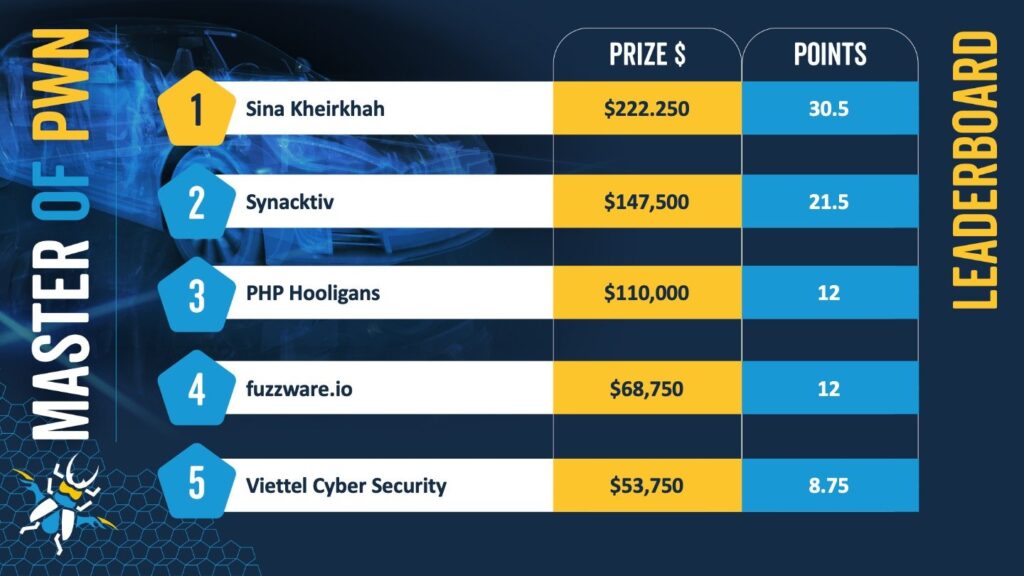
The Pwn2Own Automotive 2025 hacking competition has wrapped up, with security researchers uncovering 49 unique zero-day vulnerabilities across various automotive and charging systems. The event, which took place over three days, saw researchers awarded a total of $886,250 for their discoveries. Sina Kheirkhah of Summoning Team emerged as the “Master of Pwn,” securing the top spot with 30.5 points and $222,250 in winnings.
ZDI
Day Three highlights
The final day of the competition continued to expose critical vulnerabilities in electric vehicle (EV) chargers, in-vehicle infotainment (IVI) systems, and other automotive technologies. Among the most notable exploits were:
- Sina Kheirkhah (@SinSinology) of Summoning Team successfully exploited the ChargePoint EV charger using a single bug, earning $25,000 and 5 Master of Pwn points. He later demonstrated another exploit against the Alpine iLX-507 IVI system using a command injection bug, securing an additional $10,000 and 2 points.
- The Synacktiv team (@Synacktiv) identified an integer overflow vulnerability in the Sony IVI system, earning them $10,000 and 2 points. They also exploited a buffer overflow in the Autel MaxiCharger, demonstrating unauthorized signal transmission via the charging connector, winning $35,000 and 6 points.
- Thanh Do (@nyanctl) of Team Confused leveraged a stack buffer overflow to exploit the Alpine iLX-507, securing $10,000 and 2 points.
- PHP Hooligans demonstrated their expertise by using an OS command injection vulnerability to compromise the Kenwood DMX958XR, adding $10,000 and 2 points to their total.
- Evan Grant (@stargravy) made his Pwn2Own debut by exploiting the Kenwood DMX958XR with a unique OS command injection attack, earning $10,000 and 2 points.
Several participants also encountered “collision” scenarios, where their exploits used previously known vulnerabilities but still earned partial rewards:
- Bongeun Koo (@kiddo_pwn) of STEALIEN used three bugs to exploit the Ubiquiti EV charger, but two were already known. He still secured $26,750 and 4.5 points.
- Tobias Scharnowski (@ScepticCtf), Felix Buchmann (@diff_fusion), and Kristian Covic (@SeTcbPrivilege) of fuzzware.io exploited the WOLFBOX EV charger using a two-bug chain, but one bug was pre-discovered, reducing their prize to $18,750 and 2 points.
- Rob Blakely and Andres Campuzano of Technical Debt Collectors successfully targeted the Tesla Wall Connector, but since their exploit relied on a previously known issue, they earned $12,500 and 2.5 points.

Event summary and impact
Pwn2Own Automotive, organized by the Zero Day Initiative (ZDI), is one of the industry's leading security competitions, aimed at identifying and addressing vulnerabilities in modern automotive technology. The 2025 edition was sponsored by Tesla and VicOne, with researchers targeting systems from major brands like Sony, Kenwood, Alpine, ChargePoint, and Ubiquiti.
Throughout the three-day event (1, 2), participants were awarded $886,250 for 49 zero-day vulnerabilities, reinforcing the importance of security research in the automotive sector. With the increasing adoption of connected vehicles and EV infrastructure, these findings underscore the risks associated with automotive cybersecurity.







Leave a Reply