
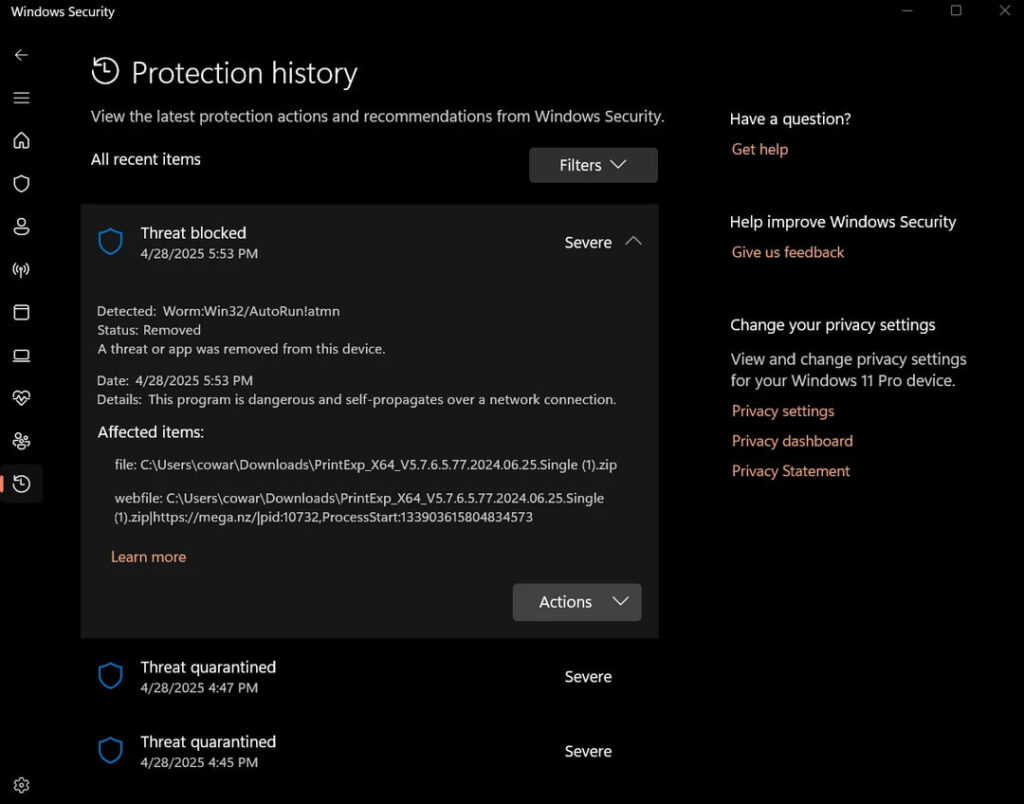
For at least six months, Procolored, a well-known manufacturer of UV and DTF printers, hosted malware-laden software downloads on its website, infecting users with backdoors and cryptocurrency stealers.
The incident first came to light when Cameron Coward, creator of the Serial Hobbyism YouTube channel, attempted to review a $6,000 Procolored UV printer. Upon inserting the USB stick included with the device, Coward's antivirus software immediately flagged the contents as dangerous, identifying a USB-spreading worm and a variant of the Floxif file infector. Procolored initially dismissed the alerts as false positives. Unsatisfied, Coward turned to Reddit for community insight and ultimately drew the attention of a professional malware analyst working for G Data.
TheSerialHobbyist | Reddit
Upon investigating the publicly available software downloads from Procolored's website, G Data discovered that six of the company's product lines, F8, F13, F13 Pro, V6, V11 Pro, and VF13 Pro, had malware embedded in their software packages. The software, hosted on mega.nz, amounted to around 8GB in total and had last been updated in October 2024.
A scan of the files revealed 39 malware detections across 20 uniquely hashed executables. These included a Delphi-based backdoor known as Win32.Backdoor.XRedRAT.A, as well as MSIL.Trojan-Stealer.CoinStealer.H, a .NET-based clipbanker that modifies cryptocurrency wallet addresses in clipboard operations to reroute funds to an attacker-controlled Bitcoin address.
G Data
Procolored, based in China, markets its products globally and positions itself as a leader in the digital textile printing industry. Their high-end hardware is widely used in small-scale manufacturing and creative industries. Given the company's established presence and the scale of the incident, the discovery sent ripples through the tech and maker communities, particularly among those who had unknowingly used the infected software in production environments.
The XRed backdoor found within Procolored's “PrintExp.exe” was consistent with previously analyzed malware from eSentire's February 2024 report, indicating that the exact same version had resurfaced unchanged. This backdoor enables attackers to execute commands via cmd.exe, capture screenshots, log keystrokes, and download or delete files. However, its associated command-and-control (C2) infrastructure has been inactive since early 2024, significantly reducing the real-world impact of this specific threat.
Of more immediate concern is the SnipVex virus, a new and previously undocumented clipbanker that doubles as a file infector. Unlike many simplistic stealers, SnipVex prepends itself to executable files, evades infection of system and temporary files, and avoids reinfecting already compromised executables using a custom infection marker (0x0A 0x0B 0x0C). It actively monitors logical drives for .exe files to spread further. The inclusion of this virus in Procolored's software strongly suggests that the infection occurred within the company's build environment or on developer systems.
The infection of 39 files across multiple software bundles points to a likely scenario of superinfection on a Procolored system lacking proper endpoint protection. Floxif, the infector initially flagged by Coward's antivirus, was not found in the downloadable software packages but may have existed solely on the USB drive shipped with his unit, further evidence of endemic malware on internal systems.
SnipVex successfully diverted cryptocurrency transactions to a single BTC address, which has recorded inbound transfers totaling 9.3 BTC. While activity on this wallet ceased in March 2024, the file infection poses a long-term integrity risk to users, as SnipVex alters original binaries, and restoring affected files can be non-trivial unless backups exist.
Following public exposure, Procolored removed all software downloads from its website around May 8, 2025, and launched an internal investigation. In correspondence with G Data, the company admitted that some software had been transferred via USB and that this might have introduced malware into their systems. They committed to virus-scanning all files before re-uploading them and shared new clean software packages for verification.
For affected users, reinstallation of the operating system is recommended for machines suspected of hosting file infectors like SnipVex or Floxif.







Leave a Reply