
A recent analysis has revealed a critical security flaw in several popular mobile apps: hardcoded cloud credentials embedded directly within the code.
This practice, which involves storing access keys for services like Amazon Web Services (AWS) and Microsoft Azure in plain text within app binaries, exposes user data and backend services to potential attacks. The findings highlight the widespread nature of this vulnerability across both iOS and Android platforms, posing a serious risk to app users and their data privacy.
Security researchers discovered this issue in numerous high-profile mobile apps, many of which have millions of downloads on platforms such as the Google Play Store and the Apple App Store.
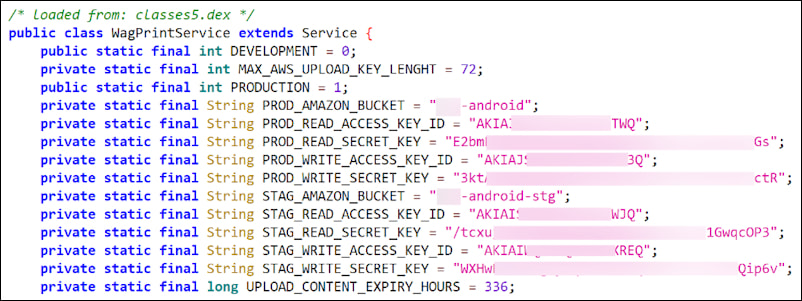
The hardcoded credentials, which provide access to sensitive cloud resources, could be extracted by anyone with access to the app’s source code, enabling malicious actors to manipulate or exfiltrate data. In particular, these vulnerabilities were identified in apps using AWS and Azure cloud services, two of the most widely used cloud platforms.
Apps with hardcoded cloud credentials
Several popular apps have been flagged for embedding unencrypted AWS or Azure credentials within their code:
- Pic Stitch: Collage Maker (5M+ downloads on Google Play): Hardcoded AWS credentials for accessing Amazon S3 storage.
- Crumbl (3.9M+ ratings on Apple Store): Contains plaintext AWS credentials used for IoT services.
- Eureka: Earn Money for Surveys (402.1K+ ratings on Apple Store): Embeds AWS credentials in plain text for logging events to AWS.
- Videoshop – Video Editor (357.9K+ ratings on Apple Store): AWS credentials are hardcoded into the app, allowing access to S3 storage.
- Meru Cabs (5M+ downloads on Google Play): Stores Azure credentials in its code, exposing log upload services.
- Sulekha Business (500K+ downloads on Google Play): Contains hardcoded Azure credentials for managing user data and posts.
- ReSound Tinnitus Relief (500K+ downloads on Google Play): Azure credentials for managing media assets are embedded within the app.
- Saludsa (100K+ downloads on Google Play): Embeds Azure Blob Storage credentials.
- Chola Ms Break In (100K+ downloads on Google Play): Contains hardcoded Azure credentials.
- EatSleepRIDE Motorcycle GPS (100K+ downloads on Google Play): Twilio credentials are embedded in the app’s code.
- Beltone Tinnitus Calmer (100K+ downloads on Google Play): Azure credentials are used for managing cloud-based assets.
- Solitaire Clash: Win Real Cash (244.8K ratings on Apple Store): Hardcoded AWS credentials.
- Zap Surveys – Earn Easy Money (235K ratings on Apple Store): AWS credentials are embedded in the app’s code.
These vulnerabilities expose sensitive cloud resources, such as storage buckets, IoT data, and logs, to unauthorized access. Attackers who obtain the credentials can potentially steal user data, modify app behavior, or disrupt service availability.
Symantec/Broadcom
Developer oversights
The prevalence of hardcoded credentials in these widely used apps underscores the severity of the issue. One of the main reasons developers resort to hardcoding credentials is to simplify access to cloud resources, such as media files, configuration settings, or cloud-based services. However, this practice introduces a significant security risk, as these keys can provide access to far more than just a single file or service.
Additionally, this issue is often rooted in poor development practices or oversight. Some developers embed credentials as a shortcut for testing purposes and forget to remove them before the app is published. In other cases, credentials are embedded in third-party libraries or SDKs that are shared across multiple apps, amplifying the risk. This supply chain problem, where vulnerabilities are introduced by outsourced developers or shared components, has been a persistent issue in mobile app development.
Securing cloud credentials
To prevent these vulnerabilities, developers must adopt secure practices for managing sensitive information:
- Instead of hardcoding credentials, store them in environment variables that are loaded at runtime.
- Utilize dedicated tools such as AWS Secrets Manager or Azure Key Vault to securely manage and access credentials.
- If credentials must be stored in the app, ensure they are encrypted and decrypted only at runtime.
- Conduct thorough code reviews and automated security scanning to detect hardcoded credentials early in the development process.







Leave a Reply