
A critical vulnerability has been identified in several D-Link Network Attached Storage (NAS) models, potentially allowing unauthorized threat actors to perform command injection.
Network Attached Storage (NAS) devices are specialized data storage servers connected to a network, designed to provide centralized data access and storage to multiple users and client devices. They serve as a hub for storing and sharing files within a local network or over the Internet, making them an essential component for both home networks and business environments.
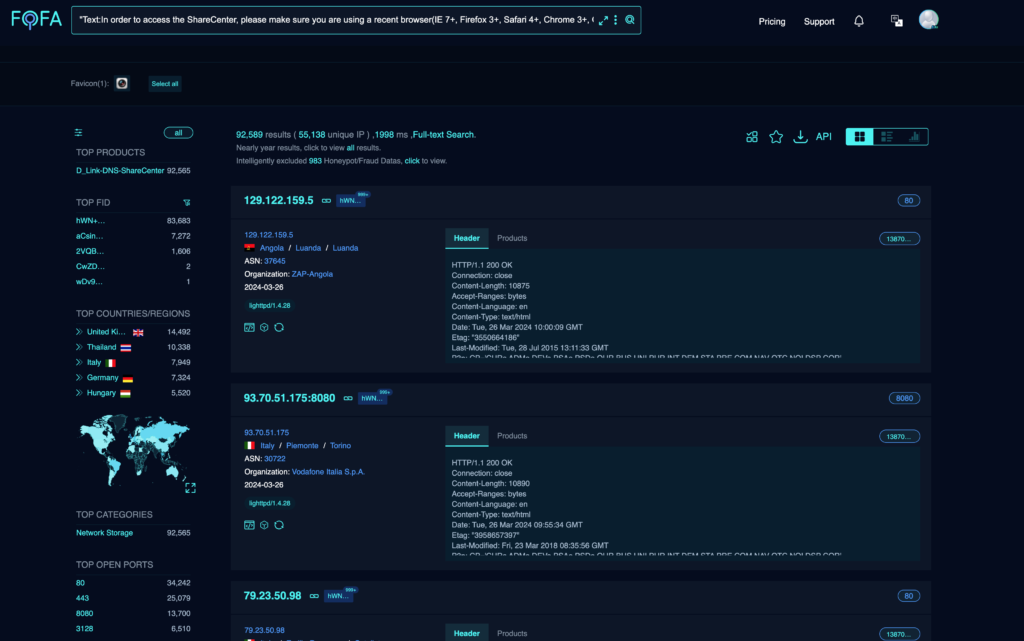
The vulnerability, identified as CVE-2024-3273, impacts the D-Link DNS-320L, DNS-325, DNS-327L, and DNS-340L models up to software version 20240403.
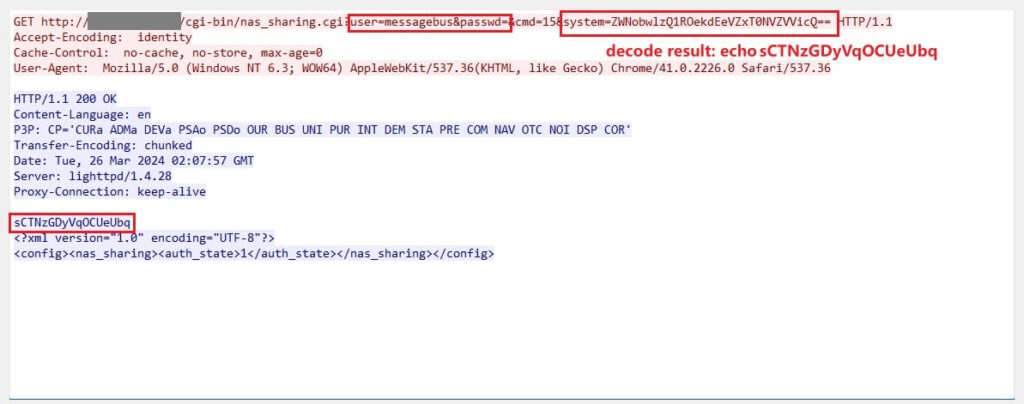
In a page on GitHub, security researcher ‘netsecfish’ offers a detailed exploration of the vulnerability mechanism, demonstrating how the flaw can be exploited. Specifically, the researcher outlines that the vulnerability exists due to improper handling of user input in the /cgi-bin/nas_sharing.cgi component of the affected D-Link NAS devices. Attackers can exploit this by crafting malicious HTTP GET requests, leading to remote command execution.
The researcher says that currently, there are 92,589 internet-exposed devices that are potentially vulnerable to CVE-2024-3273. Given the end-of-life status of the impacted models, as confirmed by D-Link, the devices are not eligible for official security updates, further exacerbating the risk for users who continue to rely on these models for data storage.
netsecfish
Considering the risks, there’s an urgent need for affected users to take immediate steps to mitigate the threats posed by CVE-2024-3273. Possible actions include ceasing the use of affected models and replacing them with currently supported devices. If immediate replacement is not feasible, affected devices should be segregated within the network to limit exposure to potential attacks.
netsecfish
Other robust mitigations include implementing firewalls, strict access controls, and regularly monitoring access logs to detect and respond to suspicious activities. Unfortunately, there are no workarounds available for CVE-2024-3273.
The most severe attack scenario for users of the vulnerable D-Link NAS devices would be data theft and leak, which can lead to personal exposure. Another grave situation would be the attackers leveraging the command injection flaw to wipe all data stored on the NAS device. Finally, there are dedicated ransomware groups operating in the NAS space, which encrypt data stored on these devices and then extort the victims.







Leave a Reply