
Cybersecurity researcher Jeremiah Fowler has uncovered a massive data breach at SL Data Services, LLC, which left over 600,000 sensitive records — including background checks, vehicle details, and property records — publicly accessible online. The unprotected database, amounting to 713.1 GB of data, was found without encryption or password protection, raising serious privacy concerns.
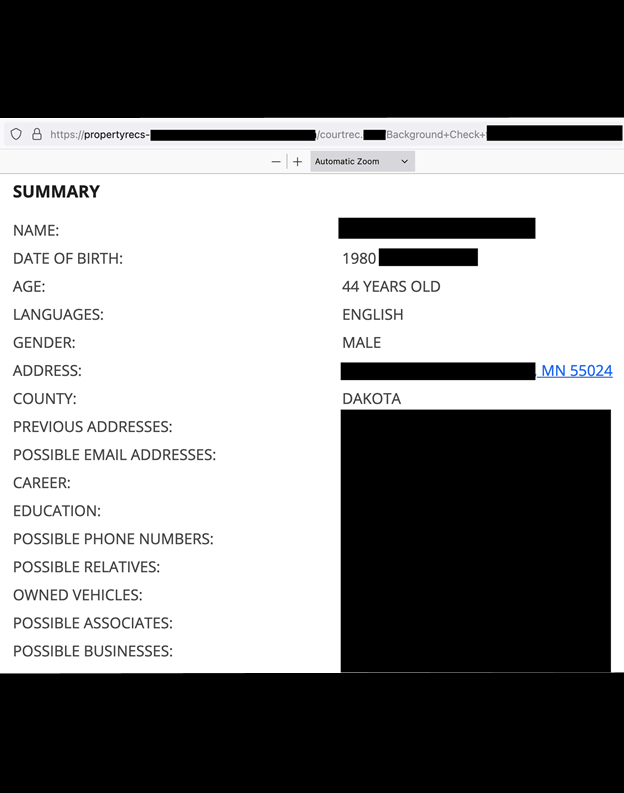
The breach exposed 644,869 PDF files containing detailed personal information such as full names, addresses, phone numbers, employment details, criminal history, and even family member details. A significant 95% of the sample documents were labeled as “background checks,” pointing to the core nature of the records stored.
Fowler, who disclosed his findings to SL Data Services via a responsible disclosure notice, noted that public access to the database was only restricted over a week after his report, during which time the number of files grew by over 151,000.
WebsitePlanet
Scale and impact of the breach
SL Data Services operates a network of 16 websites offering information services, including Propertyrec, a real estate research platform. While primarily advertising property ownership data, the database revealed the company also offers criminal background checks and motor vehicle records. SL Data Services did not respond to Fowler’s disclosure or clarify whether the database was managed internally or outsourced to a third party.
Although there is no direct evidence of unauthorized access to the database at the time of discovery, such exposed datasets are often indexed by automated web crawlers employed by threat actors. These crawlers can exfiltrate data within hours of exposure, and then resold privately or posted on darkweb forums.
Given the sensitive nature of the information, including Personally Identifiable Information (PII) like social media details and employment records, the likelihood of exploitation remains high. Threat actors could potentially use this data for spear-phishing campaigns, social engineering attacks, or identity theft.
The breach underscores the risks associated with storing sensitive data without adequate safeguards. Fowler observed that the file names themselves, which followed a format like “First_Middle_Last_State.PDF,” contained PII, making them vulnerable even if the files had been encrypted. He recommends using randomized, hashed identifiers for filenames to mitigate such risks.
This incident echoes the August 2024 National Public Data breach, where attackers accessed millions of background checks and advertised them on the dark web for $3.5 million. Both breaches highlight the growing vulnerability of background check services and similar platforms to cyberattacks, putting millions of individuals at risk of targeted exploitation.







Leave a Reply