
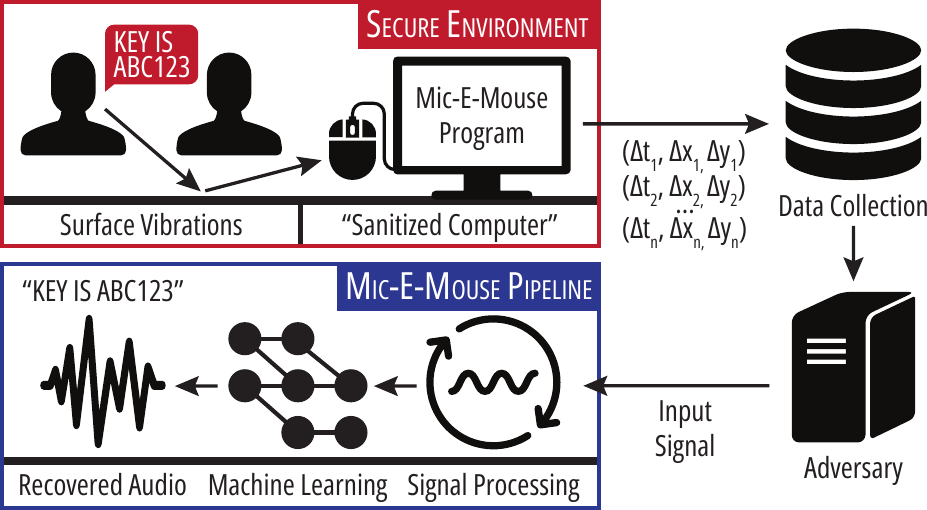
Researchers from the University of California, Irvine, have demonstrated a novel and practical side-channel attack, dubbed Mic-E-Mouse, that uses everyday optical mouse sensors to recover intelligible human speech, effectively turning your mouse into a crude, stealthy microphone.
With just unprivileged software access and no hardware modifications, attackers can reconstruct conversations by analyzing vibrations captured from desktop surfaces.
This first-of-its-kind exploit leverages the high DPI and polling rates of modern consumer-grade mice, converting tiny surface vibrations, induced by nearby speech, into data that can be filtered, processed, and reconstructed into comprehensible audio.
arxiv.org
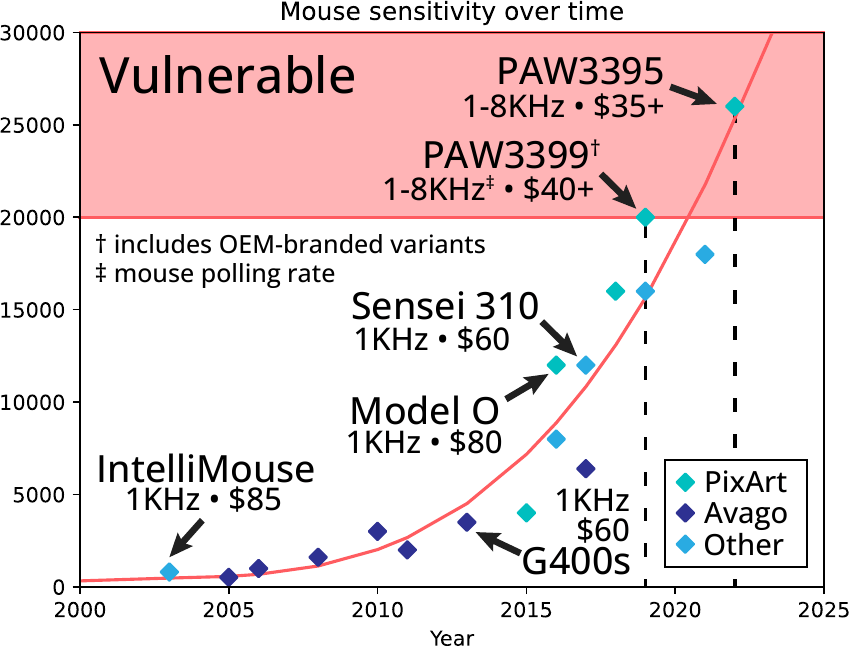
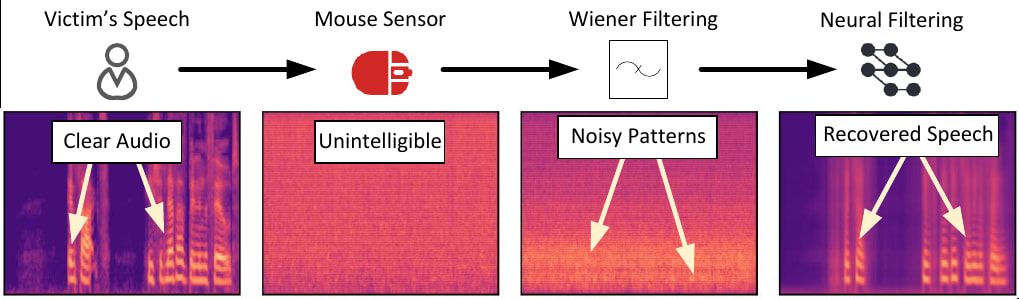
At the heart of the attack is a sophisticated data-processing pipeline that transforms raw mouse displacement data into audio waveforms. Using mice equipped with high-performance PixArt PAW3395 and PAW3399 sensors (found in models like the Razer Viper 8KHz and Darmoshark M3), the researchers collected motion data at polling rates up to 8,000 Hz and resolutions up to 26,000 DPI. These specifications, commonly found in gaming and creative peripherals, enable the detection of minute vibrations across common desk surfaces.
The pipeline consists of:
- Non-uniform data resampling using sinc interpolation.
- Noise reduction via custom Wiener filtering trained on sensor-specific profiles.
- Speech signal reconstruction using transformer-based neural networks, inspired by OpenAI's Whisper architecture.
arxiv.org
Using this approach, the researchers achieved up to +19 dB SNR improvement, with intelligibility rates of 61.57% for digit recognition and 62.3% for general speech from reconstructed AudioMNIST and VCTK datasets. Human listeners, in a blind study, were able to understand words with a 16.79% word error rate, and rated intelligibility at a Mean Opinion Score (MOS) of 4.06 out of 5.
arxiv.org
The attack requires no special privileges or kernel-level access. Modern operating systems (Windows, Linux, macOS) permit user-space access to high-frequency mouse data through widely-used libraries like Qt, GTK, SDL, or via game engines like Unity and Unreal. Exploits can be embedded into seemingly benign applications or games, even open-source ones, with minimal changes to existing telemetry or input capture routines.
A proof-of-concept was demonstrated using a patched version of OpenBlok, an open-source game, which covertly collected and transmitted mouse input data during normal gameplay. Similarly, video editing tools like Blender or Krita, which natively log fine-grained input, are potential delivery vectors.
The attack model assumes the victim is near the computer and speaking at a typical volume (60–80 dB) with their mouse resting on a surface capable of transmitting vibrations, such as plastic or wood. The researchers demonstrated that smooth surfaces like plastic allowed nearly double the speech recovery accuracy compared to rough ones like cardboard.
While not a widespread threat, Mic-E-Mouse demonstrates how modern peripherals designed for precision and speed can be misused in ways never anticipated by the manufacturers, leaking sensitive data via covert channels.







Leave a Reply