
Guardio Labs recently identified and disclosed a critical vulnerability in Opera’s browser infrastructure that could allow malicious extensions to exploit Private APIs, granting unauthorized access to sensitive functions such as screen capture, settings modification, and potential account hijacking.
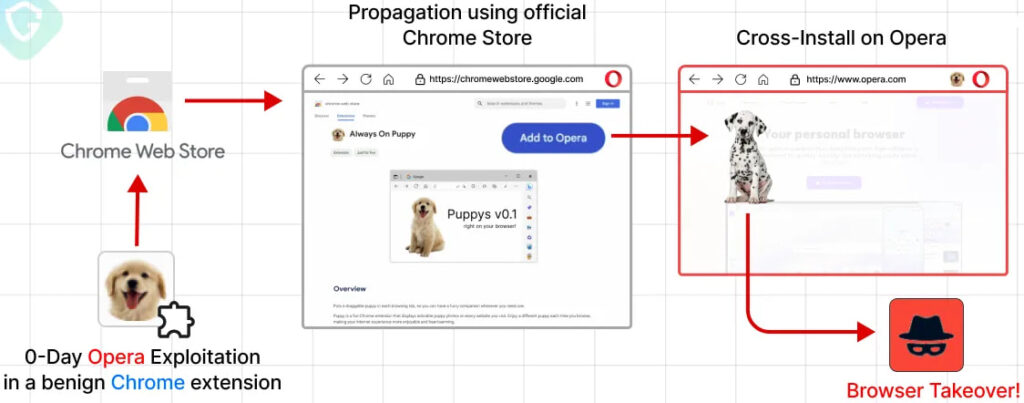
The attack, named “CrossBarking,” exemplifies the risks of enabling extensions from third-party sources, especially with seemingly harmless offerings like the popular “puppy-themed” extension, which Guardio crafted as a proof of concept. Opera has since patched the vulnerability, mitigating this novel cross-browser extension attack vector.
Guardio Labs
Vulnerability details and PoC
Guardio’s Head of Labs, Nati Tal, led the investigation into this flaw, building upon the earlier “MyFlaw” vulnerability, which highlighted a similar issue in cross-platform browser security. The recent vulnerability in Opera allowed malicious extensions from the Chrome Web Store to access Opera’s Private APIs, which are generally reserved for internal browser functionalities like the Pinboard feature, which uses these APIs for user convenience. These APIs, while enabling advanced browser capabilities, also create potential entry points for malicious actors if exploited through an external source.
Nati demonstrated the vulnerability by publishing a harmless-seeming extension on the Chrome Web Store. Disguised as an extension that adds a puppy image to every webpage, this “cute” application, once installed in Opera, could bypass security controls and manipulate the browser environment.
Such an exploit would allow attackers to inject malicious code and manipulate settings, even altering the browser’s DNS over HTTPS configuration to redirect traffic through rogue DNS servers. This proof of concept highlights the challenges in securing cross-browser extensions, particularly when third-party sources are involved.

Guardio Labs
Opera's response
Opera Software acknowledged the vulnerability, emphasizing that while this type of attack requires the user to bypass warnings and install the extension from an unverified source, it still represented a significant risk.
Opera's manual review process applied exclusively to extensions within its own Add-ons Store, typically prevents unvetted extensions from bypassing security protocols. However, users are permitted to install extensions from the Chrome Web Store, where Opera's direct oversight is not possible.
In collaboration with Guardio, Opera quickly addressed the vulnerability, deploying a fix last month. Opera reassured users that no known cases of exploitation had occurred prior to the patch. The company also committed to strengthening its review processes to limit such vulnerabilities in the future, recognizing the ongoing challenge of balancing productivity with robust security in cross-browser ecosystems.
Residual risk and recommendations
Despite Opera's prompt mitigation, residual risks remain due to the fundamental design of cross-browser extensions and reliance on third-party sources. Allowing users to install extensions from the Chrome Web Store, which uses a blend of automated and manual review, introduces a layer of exposure since malicious extensions can still evade detection through code obfuscation or delayed activation tactics.
Additionally, Opera’s reliance on Private APIs to power unique features, like Pinboards and Wallet, means these powerful access points remain potential attack vectors if future vulnerabilities arise. This setup places a degree of security responsibility on users, who must heed warnings about third-party extensions and regularly review installed add-ons for suspicious behavior.
As Guardio’s proof of concept illustrated, even seemingly benign extensions can carry hidden exploits, underscoring the ongoing risk of sophisticated attacks in the cross-browser ecosystem.
For Opera users, Guardio recommends:
- Installing extensions only from Opera’s Add-ons Store to benefit from the company's manual vetting process.
- Avoiding extensions with excessive permissions and always reviewing requested permissions upon installation.
- Ensuring frequent browser updates to stay protected as new patches are released.







Leave a Reply