
A critical privacy vulnerability in O2 UK's Voice over LTE (VoLTE) system allows any caller to accurately geolocate any O2 customer simply by initiating a phone call, without their consent or knowledge.
The flaw, which leaked detailed network identifiers and location metadata during standard SIP signaling, persisted for months with no action from the mobile provider despite attempted disclosures.
The issue was discovered and documented by independent researcher Daniel Williams, who investigated O2's IP Multimedia Subsystem (IMS) configuration using a rooted Google Pixel 8 and the Network Signal Guru (NSG) diagnostic tool. While examining SIP signaling messages to evaluate call audio quality, Williams found unusually verbose data being sent by O2’s Mavenir Unified Access Gateway (UAG), including highly sensitive information such as subscriber IMSIs, device IMEIs, and detailed cell location data.
O2 UK, a subsidiary of Virgin Media O2, provides mobile, broadband, and entertainment services across the United Kingdom, serving tens of millions of users. The IMS-based VoLTE implementation — introduced in March 2017 as “4G Calling” — was designed to improve call quality and support simultaneous data usage during voice sessions. However, the SIP signaling configuration adopted by O2 exposed a serious privacy oversight.
In a SIP message captured during a standard 4G call, Williams found headers like P-Mav-Extension-IMSI, P-Mav-Extension-IMEI, and Cellular-Network-Info. These fields disclosed not only the call initiator’s identifiers but also those of the call recipient, including:
- The recipient’s IMSI (SIM identifier) and IMEI (device identifier)
- The cell tower (E-UTRAN cell ID) the recipient was connected to
- The Location Area Code (LAC) and the age of the cell information
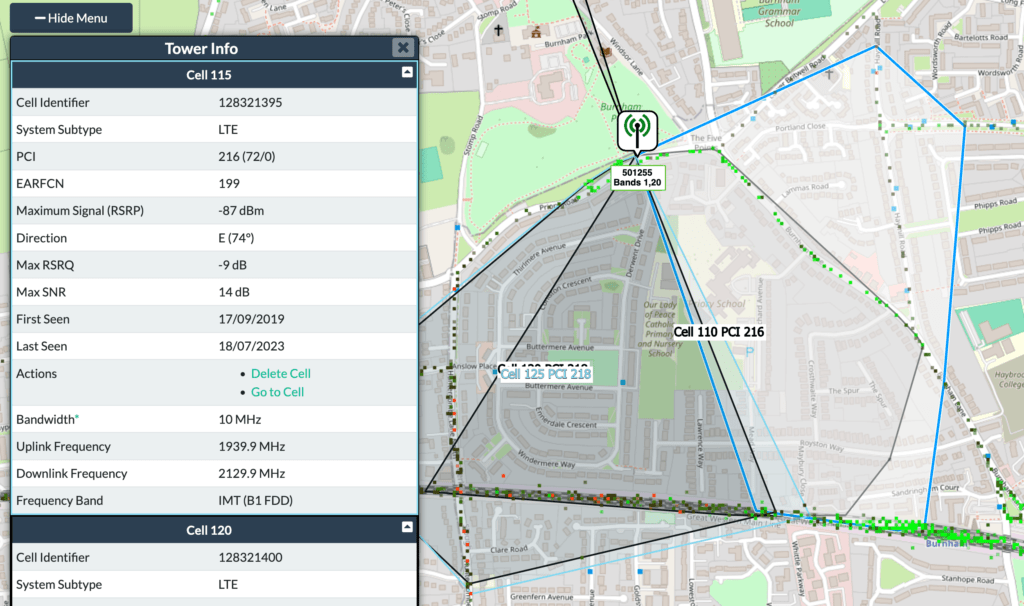
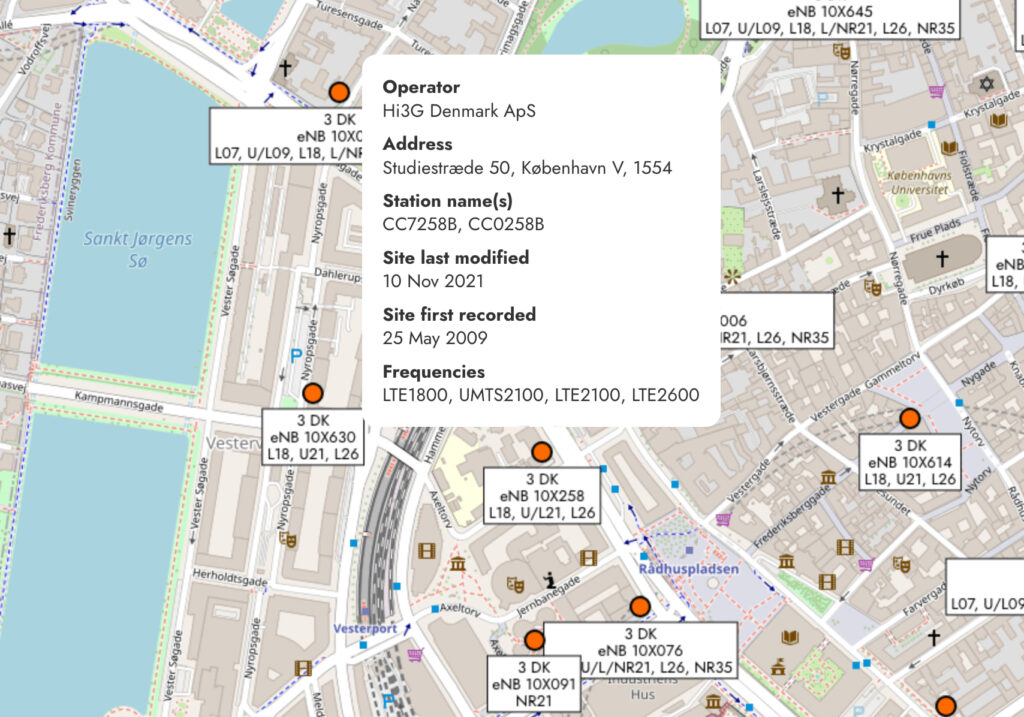
Using open-source tools such as CellMapper, these cell identifiers could be cross-referenced to locate users with high precision. In urban environments where O2 deploys dense small-cell networks, the coverage area per tower can be as narrow as 100 square meters — allowing attackers to narrow down a user’s location to within a city block. Williams demonstrated the technique’s effectiveness even when targeting a roaming user abroad, successfully locating them in central Copenhagen.
What makes the flaw particularly alarming is its accessibility. No network intrusion or advanced hacking is required — any O2 customer with basic mobile diagnostics tools could exploit the issue. The information leakage occurs entirely within the bounds of normal VoLTE call setup and cannot be mitigated by users disabling 4G Calling or switching to WiFi Calling.
O2 says a fix has been applied
Despite efforts to privately disclose the vulnerability to O2 — including emails sent to CEO Lutz Schüler and the company’s security incident inbox on March 26 and 27, 2025 — Williams reports no response or corrective action as of mid-May 2025. The company also lacks a public vulnerability disclosure program comparable to other UK networks like EE.
CyberInsider independently contacted O2 to request a comment on Williams’ findings, and we received the below response:
Our engineering teams have been working on and testing a fix for number of weeks – we can confirm this is now fully implemented and tests suggest the fix has worked and our customers do not need to take any action. – an O2 spokesperson
To protect users, Williams recommends that O2 immediately sanitize its IMS SIP messages by removing all unnecessary headers, particularly those containing subscriber identifiers and cell location data. Debugging headers should be stripped or confined to internal network elements only. It is unclear if O2's fix implements any of these suggestions.
O2 customers have no way to know if the flaw was maliciously used against them at this time, but according to the firm, they do not need to take any action to protect themselves anymore. 4G Calling or WiFi Calling did not eliminate the metadata leak, so every configuration was exposed to this attack.







Leave a Reply