
The growing complexity of electronics has made it easier than ever to conceal malicious hardware in everyday tools, such as USB cables. A detailed industrial CT scan of the O.MG Cable — a USB cable designed by security researcher Mike Grover (aka MG) — reveals just how advanced these threats have become. What appears to be an ordinary USB-C cable hides a microprocessor, antenna, and other electronics that can execute highly sophisticated attacks, posing risks to individuals and organizations alike.
3D scanning the O.MG Cable
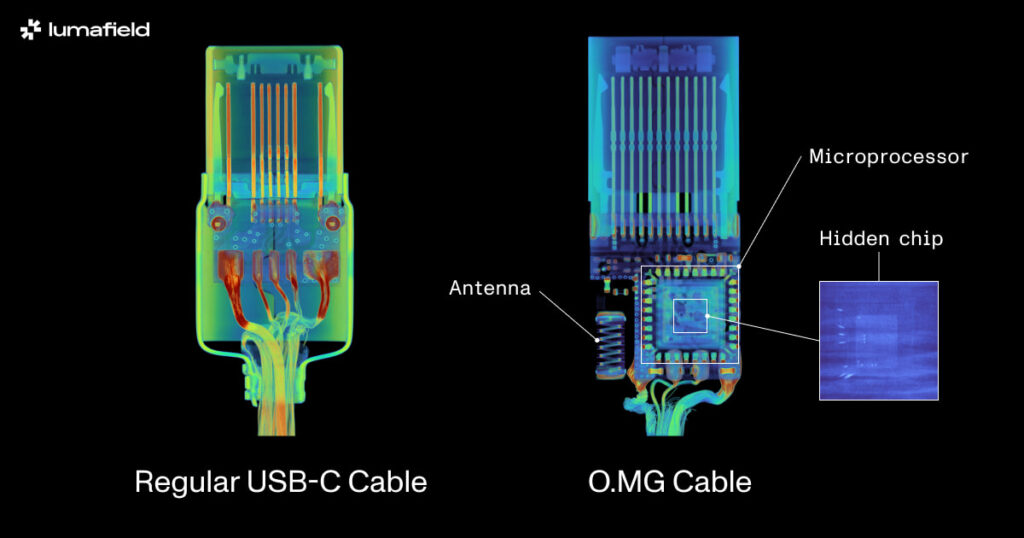
The O.MG Cable is a specially modified USB cable designed to look indistinguishable from its legitimate counterparts. While it functions as a normal USB cable, its hidden electronics allow it to log keystrokes, inject malicious scripts, and even enable remote system access over wireless connections. Developed by MG, a security researcher specializing in hardware hacking, the O.MG Cable showcases the alarming level of sophistication that can be achieved in malicious device design.
Inside the cable’s casing, a tiny microprocessor and antenna are seamlessly embedded, making detection nearly impossible through conventional inspection methods. Using industrial CT scanning technology, Lumafield’s research team uncovered the intricate internal structure of the cable, highlighting how these components are expertly concealed. Lumafield states that even 2D X-ray scans would struggle to reveal such a malicious design.
Lumafield
Unlike traditional inspection tools, which can only capture surface details or flat, 2D images, industrial CT scans generate volumetric 3D images, exposing every component and its connections. If you’re interested in taking a closer look at the scan, you can do it from Lumafield’s ‘Voyager’ 3D model viewer (takes a while to load).
One particularly alarming discovery in the O.MG Cable is the hidden silicon storage chip bonded to the microprocessor, linked by bond wires thinner than a human hair. These connections are nearly invisible to the naked eye or under conventional imaging, but industrial CT exposes them in detail, allowing researchers to trace their purpose and function.
Supply chain and hardware tampering risks
The O.MG Cable is not an isolated example — it highlights the broader risks posed by supply chain tampering. As electronics become smaller and more integrated, the potential for concealed threats increases dramatically. Malicious components can be inserted at virtually any point in the supply chain, potentially compromising sensitive systems or critical infrastructure.
Modern supply chains often rely on traditional inspection tools to validate hardware, but these methods are insufficient for detecting sophisticated threats. Industrial CT provides non-destructive inspection capabilities that can verify hardware integrity with micron-level precision. This is crucial in industries ranging from consumer electronics to defense, where undetected tampering can have catastrophic consequences. However, this technology is beyond the reach of the average consumer/end user, who is left with no other option than to trust the makers, importers, and resellers of the products they buy and use.
The O.MG Cable serves as both a proof-of-concept and a warning about the hidden risks in everyday devices. While it was designed as a research tool to raise awareness of hardware security vulnerabilities, the techniques used in its creation could easily be replicated by malicious actors. From phone chargers to network cables, the potential for concealed attacks is vast and largely undetected.







Leave a Reply