
Elastic Security Labs has identified a new Windows backdoor called BITSLOTH, which exploits the Background Intelligent Transfer Service (BITS) for command-and-control (C2) operations.
This discovery emerged during an investigation into a cyber intrusion targeting a South American government's Foreign Ministry. The malware, under active development since 2021, showcases advanced capabilities for data gathering, execution, and evasion.
Discovery and analysis
BITSLOTH was uncovered on June 25, 2024, during a routine security assessment of a government server. The malware was part of an attack by a group tracked as REF8747, who primarily used publicly available tools. BITSLOTH, however, stood out due to its unique use of BITS for C2 communications. Notably, the malware leveraged a shellcode loading project called RINGQ to execute the payload in memory, bypassing traditional defenses.
Upon lateral movement within the network, BITSLOTH was deployed as a DLL (flengine.dll) via a side-loading technique using FL Studio, a legitimate music production program. This method enabled the attackers to evade detection and maintain persistence on the compromised systems.
Background Intelligent Transfer Service (BITS)
BITS is a Windows service designed to facilitate the asynchronous transfer of files between machines, which is particularly useful for downloading updates and data transfers with minimal impact on network performance. It handles network interruptions by pausing and resuming transfers, even after a system reboot. BITS is often trusted by security tools due to its legitimate use cases, making it an attractive vector for malicious exploitation.
Elastic Security labs
BITSLOTH capabilities
BITSLOTH is equipped with 35 command handlers, enabling extensive control over infected systems. Key features include:
- Data Collection: Keylogging, screen capture, system information retrieval.
- Execution: Running and executing commands, file uploads, and downloads.
- Persistence: Leveraging BITS jobs for maintaining a foothold on the system.
- Communication: Using hard-coded C2 server configurations embedded within the malware.
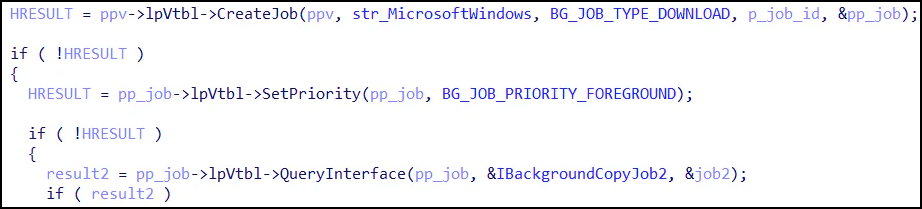
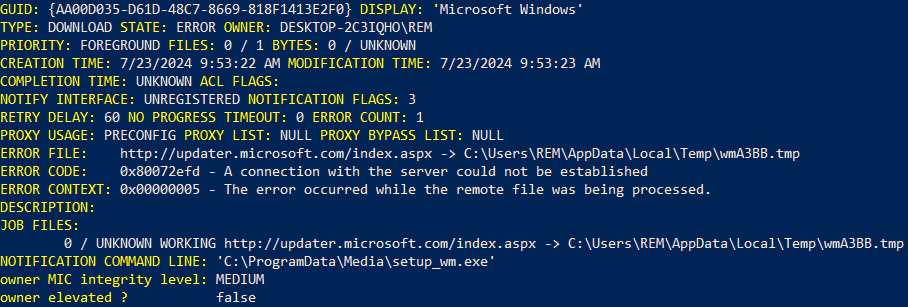
The malware uses BITS to create and manage jobs that appear benign, such as those mimicking Windows update tasks, thereby evading detection. For instance, BITSLOTH cancels existing BITS jobs with names like “WU Client Download” and creates new ones under similar guises. These jobs are configured to communicate with C2 servers using HTTP or HTTPS, blending malicious traffic with legitimate network operations.
Elastic Security Labs
Defending
The use of BITS by malware like BITSLOTH is particularly concerning due to the trusted nature of this service. Organizations often struggle to monitor and differentiate between legitimate BITS traffic and malicious activity. This exploitation method allows attackers to maintain a low profile and persist within networks for extended periods.
To mitigate such threats, security teams should implement the following measures:
- Increase visibility into BITS network traffic to detect anomalies.
- Utilize advanced endpoint detection and response (EDR) solutions to identify and block suspicious behaviors associated with BITS jobs.
- Conduct frequent security audits of systems to identify and remediate unauthorized BITS jobs.
- Deploy YARA rules provided by Elastic Security Labs to detect BITSLOTH and similar malware.
Elastic Security Labs has published YARA signatures and other indicators of compromise on its report to aid in the detection of BITSLOTH.







Leave a Reply