
The notorious Lazarus Group has evolved its infection tactics, employing both updated and novel malware like ‘CookiePlus' to infiltrate targets in defense, aerospace, cryptocurrency, and nuclear industries. Kaspersky's latest analysis reveals how the group used sophisticated infection chains and modular malware to bolster persistence and evade detection in a recent wave of attacks tied to their “DeathNote” or “Operation DreamJob” campaign.
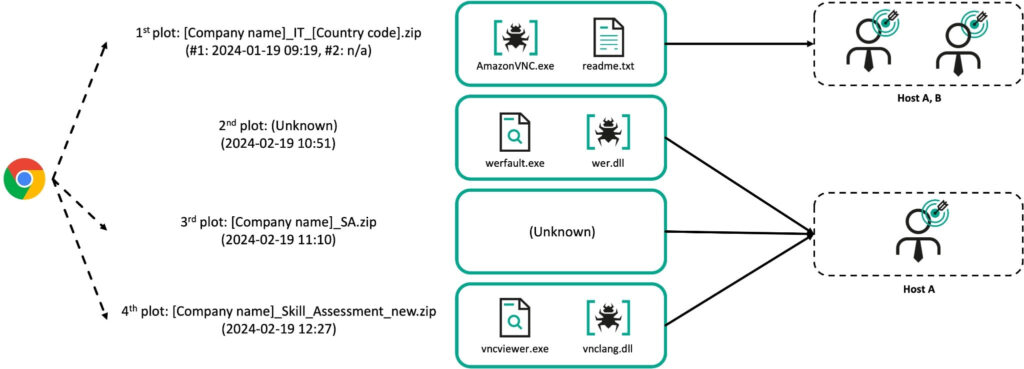
According to Kaspersky researchers, the threat group delivered malicious files via archive formats (ISO and ZIP) to at least two employees at the same nuclear-related organization within a month. These archives masqueraded as skill assessments for IT positions at prominent firms. The attackers used Trojanized utilities like AmazonVNC.exe, a modified version of TightVNC, which was deployed alongside legitimate UltraVNC components to deceive targets.
Kaspersky
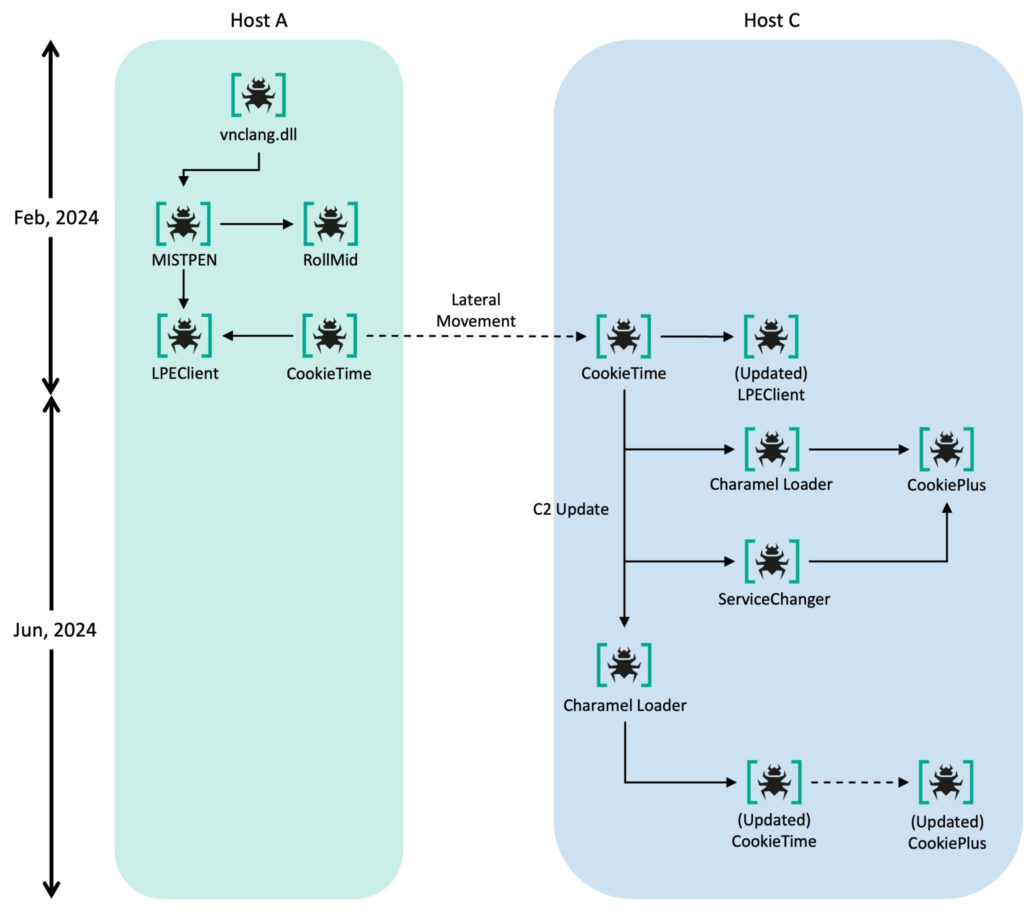
AmazonVNC.exe acts as a Trojanized remote access utility, decrypting internal malicious resources like the Ranid Downloader, while UltraVNC Viewer is a legitimate software paired with the malicious vnclang.dll, which acted as a loader for advanced malware like MISTPEN. This approach highlights the group's ability to blend legitimate tools with malicious code, creating a layered infection chain tailored to avoid detection.
Kaspersky
Key elements of Lazarus's evolving toolkit include new malware frameworks and plugins:
- CookieTime: Initially observed on infected systems, this malware now downloads payloads and executes commands from a command-and-control (C2) server.
- CookiePlus: A successor to MISTPEN, this downloader masquerades as a Notepad++ plugin and communicates via encrypted HTTP headers. It employs advanced decryption techniques to fetch plugins and additional payloads, including:
- TBaseInfo.dll: Gathers system information.
- Sleep.dll: Pauses activity based on external parameters.
- Hiber.dll: Alters execution configurations.
- ServiceChanger: Exploits legitimate services like SSH-agent to side-load malicious DLLs, enabling stealthy deployment of malware.
Kaspersky
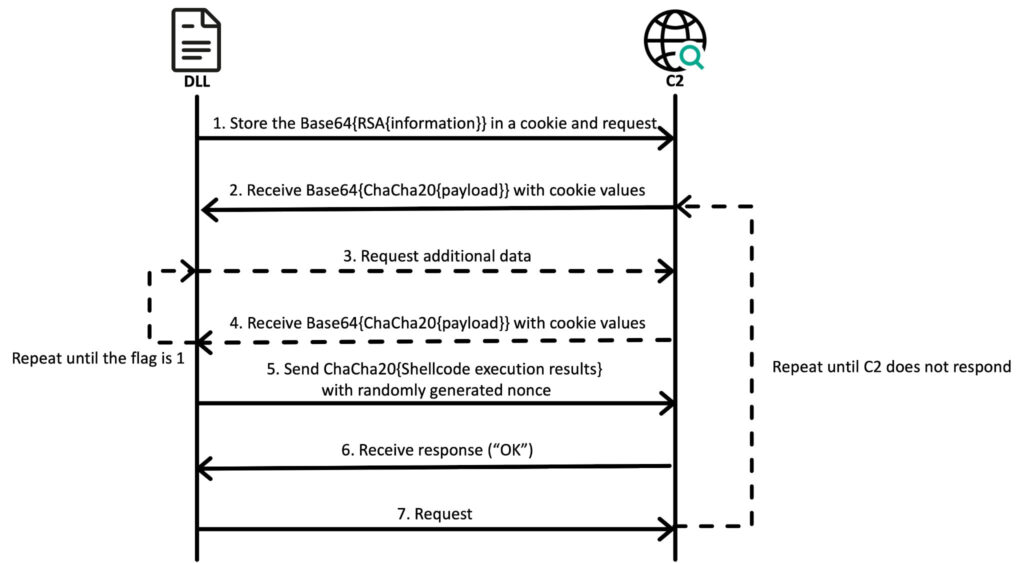
The attackers utilized compromised WordPress servers as C2 infrastructure, relying on PHP-based services to host payloads. Advanced encryption and modular design have made it challenging to determine the extent of infections. For example, CookiePlus uses ChaCha20 encryption and a Base64-encoded RSA handshake for secure communication. The modular design allows plugins to be swapped or expanded, showing active development and iterative improvements in the group's tools.
Kaspersky
The Lazarus Group, linked to North Korea's government, is a sophisticated Advanced Persistent Threat (APT) actor known for targeting critical sectors. The use of modular malware like CookiePlus demonstrates their adaptability and focus on enhancing resilience against security defenses.
Defending against this sophisticated threat requires monitoring for abnormal activity from legitimate VNC utilities, employing endpoint security solutions that detect DLL side-loading, and isolate sensitive systems through network segmentation.







Leave a Reply