
A team of white-hat researchers from PCAutomotive demonstrated a chilling remote attack chain against the 2020 Nissan LEAF, converting the popular electric vehicle into a remotely controllable surveillance device with near-total access to its internal systems.
Presented at Black Hat Asia 2025, their 118-slide technical walkthrough shows how attackers could track, spy on, and even steer the car — all using parts bought on eBay and from a local junkyard.
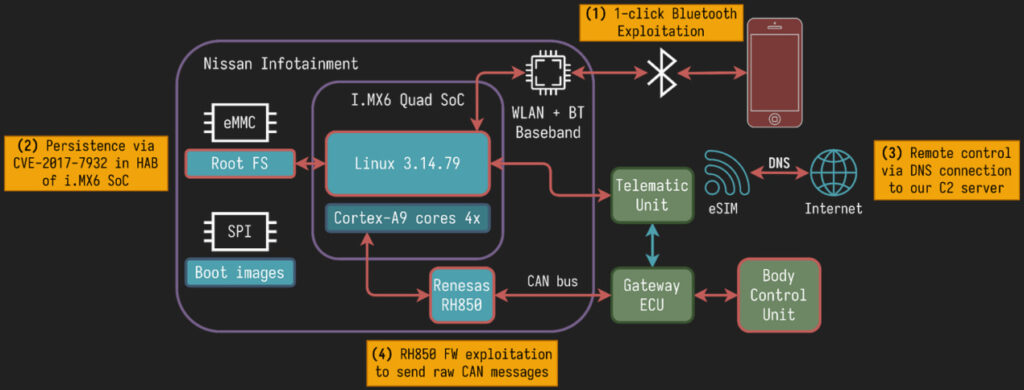
The researchers behind the exploit — Mikhail Evdokimov, Radu Motspan, and Polina Smirnova — spent over a year investigating Nissan’s in-vehicle infotainment (IVI) system, telematics unit, and gateway architecture. Their attack leveraged 11 vulnerabilities, including five stack buffer overflows and a decades-old secure boot bypass (CVE-2017-7932), allowing them to gain root access, persist across reboots, and ultimately gain control over safety-critical components via the CAN bus.
To begin, the researchers built a fully functional testbench of the Nissan LEAF’s electronic systems using salvaged modules. By bypassing the anti-theft mechanisms through CAN message replay and seed-response table generation, they enabled unauthorized startup of the IVI — the component central to the car’s infotainment and Bluetooth systems.
The team then turned to the Bluetooth stack, uncovering a critical vulnerability in the Hands-Free Profile (HFP) implementation. A poorly bounded buffer in the response parser allowed for remote code execution (CVE-2025-32059). Exploiting this flaw gave them root shell access without physical interaction — achievable through what they dubbed a “0.5-click” attack by tricking users into opening the Bluetooth pairing menu via 2.4GHz jamming.
Once inside, the attackers persisted by enabling SSH and abusing unprotected system partitions. They then leveraged an outdated secure boot process on the i.MX6 chip, enabling them to patch system scripts and survive reboots. For data exfiltration, they set up covert DNS-based tunnels via the car’s telematics module, circumventing outbound filtering using dnscat2.
From there, they pivoted to the car’s internal CAN buses. Exploiting a stack overflow in the RH850 microcontroller’s firmware update protocol (CVE-2025-32058), they gained code execution privileges within the car's real-time systems. Because the gateway filtering was weak (PCA_NISSAN_009), this allowed command injection into multiple domains, including body control (doors, lights), infotainment, and even steering (via UDS command 0430252001000000 to the ADAS ECU).
The result was complete remote control over the vehicle — from activating the horn and locking the doors to steering the wheel. All of this was performed over the internet, without physical access to the car, using only off-the-shelf tools and reverse-engineering effort.
PCAutomotive
The Nissan LEAF is one of the world’s best-selling electric vehicles, especially popular in Europe and Asia. The 2020 model targeted in this research includes electronic power steering, Bluetooth infotainment, and a telematics control unit, all of which were manipulated in this attack.
PCAutomotive responsibly disclosed the vulnerabilities to Nissan and Bosch (the IVI’s OEM vendor) over a 13-month period starting August 2023. However, CVE coordination was fraught with delays. Bosch ultimately declined to register the CVEs, and PCAutomotive resorted to using ASRG for publication.
The following CVEs were included in the research:
- CVE-2025-32056 – Anti-Theft bypass
- CVE-2025-32057 – MiTM attack on update mechanism (app_redbend)
- CVE-2025-32058 – Stack overflow in V850 CBR processing
- CVE-2025-32059 – Stack buffer overflow (RCE #0)
- CVE-2025-32060 – Lack of kernel module signature verification
- CVE-2025-32061 – Stack buffer overflow (RCE #1)
- CVE-2025-32062 – Stack buffer overflow (RCE #2)
- CVE-2025-32063 – Wi-Fi persistence mechanism
- PCA_NISSAN_009 – Improper CAN bus traffic filtration between domains
- PCA_NISSAN_012 – Persistence via CVE-2017-7932 in the i.MX6 secure boot (HAB)
- CVE-2017-7932 – Legacy CVE reused for the HAB vulnerability (i.MX6 root-of-trust bypass)
Drivers should ensure their vehicles are running the latest firmware updates from the manufacturer. Owners should also avoid pairing Bluetooth devices in public or under suspicious circumstances, as attackers could spoof devices or jam the signal to trigger exploit paths.
Auto manufacturers must strengthen update mechanisms, enforce secure boot, and adopt better separation between infotainment and critical systems. Finally, regulators should mandate regular third-party audits for automotive software, especially for components connected to wireless interfaces.







Leave a Reply