
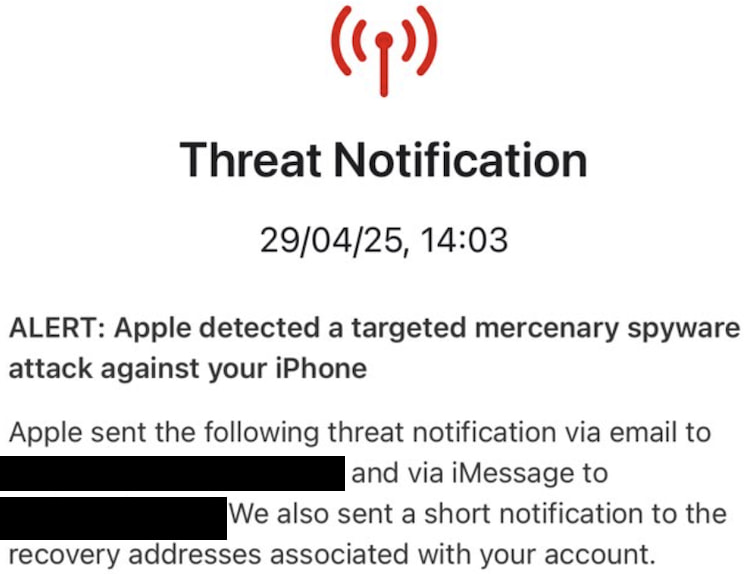
Citizen Lab has uncovered a previously undisclosed iMessage zero-click vulnerability used to deploy Paragon's Graphite spyware against at least two European journalists.
The flaw, now tracked as CVE-2025-43200, represents a new zero-day vulnerability and is the latest example of how mercenary spyware operators are exploiting iOS through silent or poorly disclosed attack chains.
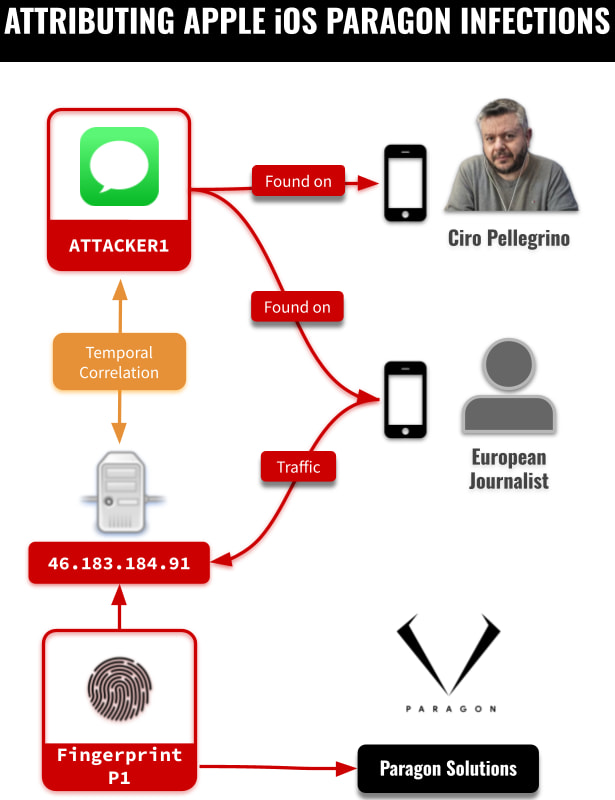
The forensic analysis published by researchers Bill Marczak and John Scott-Railton marks the first confirmed use of Paragon spyware against iPhones. Both victims, an anonymous prominent European journalist and Ciro Pellegrino of Fanpage.it, were targeted via a sophisticated zero-click iMessage exploit requiring no user interaction. The spyware silently infiltrated the devices through an iMessage account dubbed “ATTACKER1,” believed to belong to a specific Paragon customer.
Citizen Lab
Citizen Lab identified infection artifacts showing the compromised iPhones were communicating with the IP address 46.183.184[.]91, tied to previously published Graphite infrastructure. Infection occurred in early 2025 while the devices were running iOS 18.2.1, with no visible signs to the targets.
The central discovery here is the iMessage delivery vector itself: a zero-click exploit using a malicious media file shared via iCloud Link. Apple confirmed the underlying flaw and assigned CVE-2025-43200 only after Citizen Lab's inquiries, quietly updating its iOS 18.3.1 security bulletin on June 11, four months after the patch was released in February.
Apple's bulletin states the bug was “exploited in an extremely sophisticated attack against specific targeted individuals,” but gives no technical detail. It is unclear whether Apple originally patched the issue in response to internal knowledge of active exploitation as a result of third-party disclosure or incidentally as part of broader hardening. The retroactive CVE assignment and lack of disclosure have raised renewed concerns over Apple's transparency in handling actively-exploited vulnerabilities.
This isn't the first time Paragon has exploited a zero-day in iOS. As Citizen Lab reported in March 2025, the company previously used a WhatsApp-based zero-click exploit and another iOS zero-day against an Italian human rights activist. That attack left behind the forensic marker “SMALLPRETZEL,” linked to suspicious CloudKit behavior. The latest Graphite infections are distinct but reinforce the conclusion that Paragon and its clients have recurrent access to elite-level exploits, targeting both Android and iOS users without detection.
Citizen Lab
The repeated targeting of Fanpage.it, a prominent Italian investigative news outlet, suggests a focused campaign against the media. Pellegrino is the second confirmed journalist from the outlet to be targeted, following earlier evidence that editor Francesco Cancellato's Android device was flagged by WhatsApp for Graphite targeting, though without conclusive forensic proof.
Paragon Solutions, based in Israel, markets Graphite to government clients as a lawful surveillance tool. Yet investigations have repeatedly shown the tool being used against journalists, activists, and civil society. Italy has admitted to purchasing Graphite but denies deploying it against journalists. COPASIR, the Italian parliamentary intelligence oversight committee, recently acknowledged the spyware's use in limited cases but claims no knowledge of who targeted Fanpage.it staff.
In a separate report published June 5, the Italian intelligence oversight committee (COPASIR) acknowledged the government's past use of Graphite, but denied involvement in the Fanpage.it cluster. Paragon claimed it offered to assist Italian authorities in investigating the matter but was rejected.







Leave a Reply