
Elastic Security Labs has identified a new class of Windows vulnerabilities, termed “False File Immutability” (FFI). These vulnerabilities expose significant security risks stemming from incorrect assumptions about file immutability. The security firm revealed how these vulnerabilities can be exploited to achieve arbitrary code execution with kernel privileges in Windows 11.
Elastic Security Labs‘ detailed investigation reveals how fundamental flaws in Windows' file handling can lead to severe security breaches. This vulnerability affects both traditional file operations and memory-mapped files, underscoring the broad impact of these flaws.
Flaw mechanism
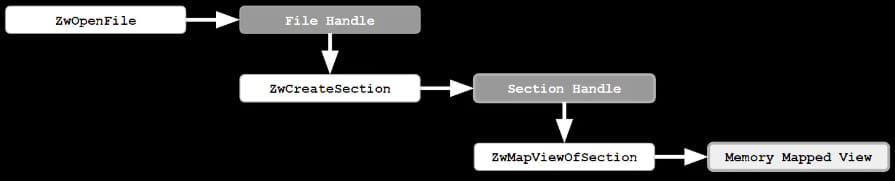
When a file is opened in Windows, the system uses the CreateFile API, which includes parameters for desired access and sharing mode. Typically, if a file is opened without write sharing (FILE_SHARE_WRITE), it is assumed to be immutable, meaning other processes cannot modify it while it is in use. The filesystem drivers enforce this immutability through functions like IoCheckShareAccess and MmDoesFileHaveUserWritableReferences.
However, the vulnerability arises when the filesystem is unaware of modifications made to memory-mapped files. When a file is mapped into memory using APIs like ZwCreateFile and ZwCreateSection, the mapping can persist even if the original file handle is closed. This allows an attacker to modify the file via memory mapping, bypassing the sharing restrictions.
Elastic
For example, if an application opens a file without FILE_SHARE_WRITE, it assumes the file is safe from external modifications. However, if another process maps the file into memory and modifies it, the first application remains unaware of these changes, leading to potential exploits.
Impact on Windows systems
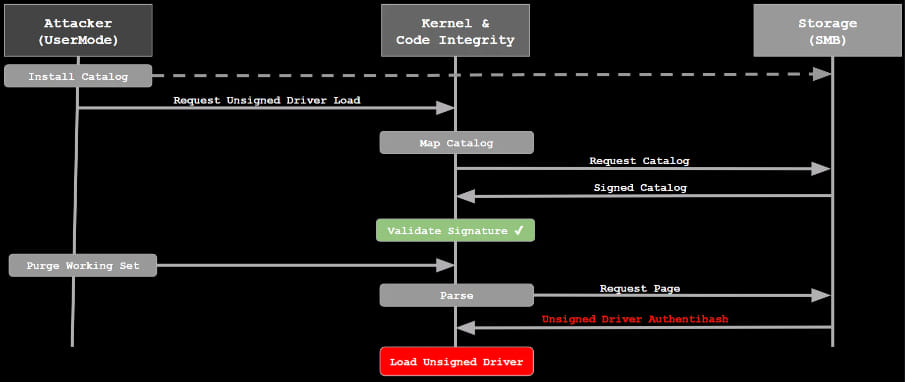
Windows requires PE files (EXE, DLL, SYS, etc.) to remain immutable to prevent tampering. This immutability is enforced by the Code Integrity (CI) subsystem. However, CI can be bypassed by exploiting FFI. For instance, an attacker can manipulate network redirectors to modify DLLs of Protected Process Light (PPL) applications, which are critical for security software. This was demonstrated by Elastic Security Labs through their PPLFault exploit, which showcased how ransomware could bypass protections and disable antivirus services.
Elastic
Mitigation and defense
Microsoft responded to the PPLFault exploit by implementing dynamic page hashes for executable images loaded over network redirectors in February 2024. However, Landau's latest research extends beyond this, showing how attackers can also exploit security catalogs (.cat files) used by CI to validate PE files.
To mitigate FFI vulnerabilities, several strategies are recommended:
- Enable page hashes to enforce integrity checks on individual pages of memory-mapped files.
- Avoid double reads to prevent scenarios where the same value is read multiple times from an attacker-controlled buffer.
- Copy files to heap. Work with a copy of the file contents in memory rather than directly accessing the file.
- Use functions like MmProbeAndLockPages to lock pages into physical memory, ensuring they cannot be swapped out and tampered with.
End-users can enable Hypervisor-Protected Code Integrity (HVCI) to add a security layer. HVCI runs CI in a separate virtual machine, mitigating the impact of these vulnerabilities by isolating the catalog processing.
The False File Immutability vulnerability class underscores the importance of re-evaluating long-standing assumptions in system design. As researchers continue to explore the implications of FFI, it is crucial for developers and security professionals to adopt recommended mitigations and remain vigilant against potential exploits.







Leave a Reply