
A new ransomware-as-a-service (RaaS) offering dubbed VanHelsingRaaS has surfaced, rapidly gaining traction within cybercriminal circles since its launch earlier this month.
Within just two weeks, it has already claimed at least three victims, demanding up to $500,000 in Bitcoin and showcasing cross-platform capabilities that mark a significant evolution in the RaaS threat landscape.
Check Point Research and CYFIRMA were among the first to uncover and analyze the VanHelsing operation. CYFIRMA initially spotted signs of the ransomware on dark web forums during routine monitoring, while Check Point conducted an in-depth technical analysis after identifying multiple VanHelsing variants targeting Windows systems. The malware’s versatility and rapid development cadence were evident in two compiled versions dated March 11 and March 16 — just five days apart — highlighting swift iteration by its authors.
Affiliate-driven, broad targeting
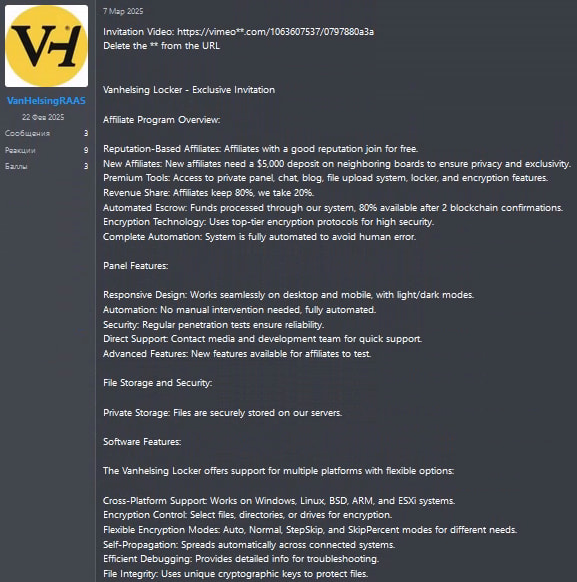
VanHelsing RaaS operates on a classic affiliate model, allowing experienced and novice cybercriminals alike to participate. New entrants must pay a $5,000 deposit, while reputable affiliates may join at no cost. The model pays affiliates 80% of any ransom collected — usually after two blockchain confirmations — while operators retain the remaining 20%. One hard rule governs the operation: attacks on Commonwealth of Independent States (CIS) nations are prohibited, a familiar restriction in Russian-based cybercrime groups.
Check Point Research
The malware supports targeting across several platforms, including Windows, Linux, BSD, ARM, and ESXi environments. Affiliates are equipped with an intuitive web-based control panel, making the orchestration of ransomware campaigns straightforward and scalable.
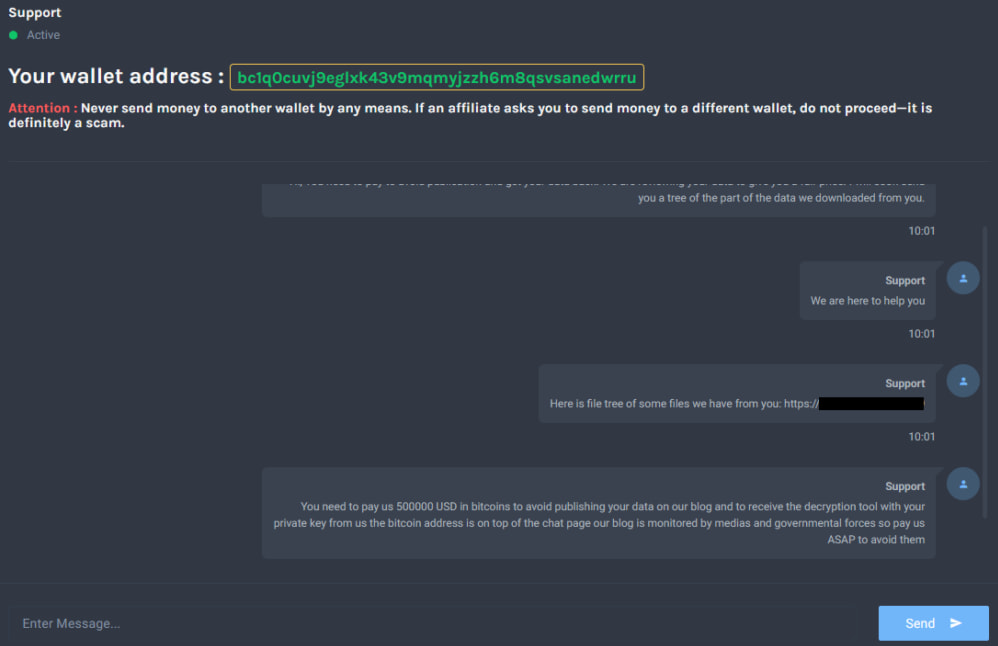
So far, VanHelsing affiliates have targeted victims in France and the United States, focusing on government agencies, manufacturing firms, and pharmaceutical companies. In each case, the attackers leveraged a double extortion strategy — encrypting files and exfiltrating sensitive data, with threats of public leaks used to intensify pressure during negotiations.
Check Point Research
VanHelsing’s features
The VanHelsing ransomware is written in C++ and shows early signs of modular, expandable architecture. Its encryption mechanism uses ChaCha20 with Curve25519 for key exchange. The malware appends the .vanhelsing extension to encrypted files and drops a ransom note (README.txt) in affected directories, warning against third-party recovery tools.
Desktop wallpapers are changed using a dropped image file (vhlocker.png), and a related .ico file is intended to mark encrypted files visually. However, Check Point found that a misconfiguration leads to a mismatch — the malware mistakenly expects a .vanlocker extension, though it actually uses .vanhelsing.
VanHelsing includes a Silent Mode encryption feature to evade detection. In this mode, the malware encrypts files first without renaming them, then re-scans the system solely to apply the .vanhelsing extension, helping it bypass behavior-based defenses that monitor file renaming during encryption.
It also supports SMB spreading using PsExec-like techniques, excluding critical network shares like NETLOGON and sysvol to avoid disrupting authentication services. The malware includes numerous command-line arguments to tailor execution, such as:
–no-network, –no-local, and –no-mounted to control target scopes–spread-smb and placeholder –spread-vcenter for network propagation–skipshadow to bypass deletion of shadow copies, though this is not used by default–system, a currently unimplemented placeholder for future privilege escalation
A threat on the rise
The VanHelsing RaaS poses an advanced threat even if it’s still in its beginnings. Its development is clearly ongoing, and its multi-platform targeting broadens its attack surface significantly. By combining advanced technical capabilities with a low barrier to entry for affiliates, it is well-positioned to proliferate rapidly.
Check Point confirmed that infected systems have already paid hefty ransoms, with one negotiation involving a $500,000 payment to a designated Bitcoin wallet. Several active Tor-based negotiation and leak portals have also been identified.






okieeeeeeeeeeeeee