
A team of researchers from Northeastern University has uncovered a novel USB side-channel attack that exploits congestion within USB hubs to monitor user activity.
Their study demonstrates how attackers can remotely recover keystrokes and track website visits without requiring physical access to the target device, raising significant privacy concerns.
USB congestion as an attack vector
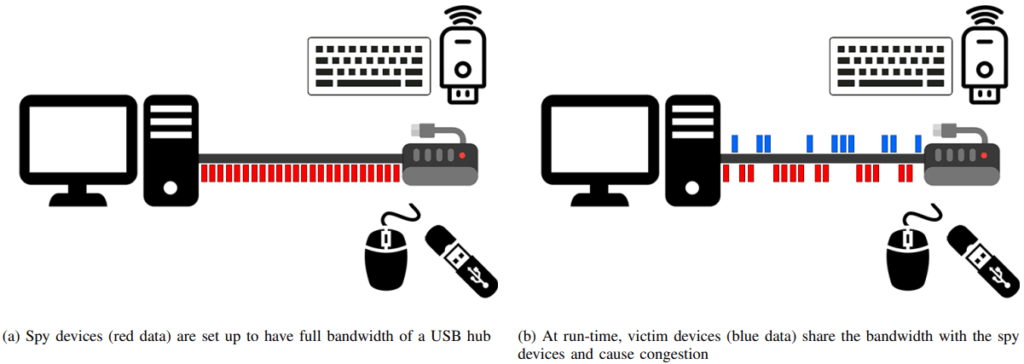
The research highlights vulnerabilities in USB’s shared bus architecture. USB hubs, which allow multiple peripherals to connect to a single host, allocate bandwidth dynamically based on device priority and activity. By analyzing traffic congestion at the hub level, attackers can infer sensitive information about the victim’s interactions with USB-connected devices.
Building on previous research into PCIe-based side-channel attacks, the team adapted the concept for USB, leveraging the predictable timing of data packets. Unlike traditional keylogging or network sniffing techniques, this attack does not require malware installation or administrative privileges, making it significantly harder to detect.
arxiv.org
The researchers successfully demonstrated two attack scenarios:
Keystroke Recovery Attack
- The attack exploits congestion caused by USB keyboards, which use small, frequent data transfers (interrupt transfers).
- An attacker introduces a rogue USB mouse, programmed to send frequent but imperceptible movement updates.
- By measuring delays in these updates when a user types, the attacker can reconstruct keystrokes.
- Using machine learning models, the researchers achieved a 36.3% accuracy in predicting typed passwords within the top 10 guesses and an 89.3% accuracy within the top 50.
Website Fingerprinting Attack
- This attack monitors network activity from a USB network adapter, such as an Ethernet dongle or USB Wi-Fi device.
- The attacker, using a connected USB device like an external SSD, continuously transfers data to measure variations in congestion.
- By analyzing these variations, the attacker can infer which website the user is visiting.
- A deep learning model achieved 83.4% accuracy in identifying websites in a closed-world scenario (top 100 websites).
Implications and countermeasures
This discovery underscores the inherent security risks in USB technology, which was not designed with strong privacy protections. Since USB devices are trusted by default, attackers could exploit this weakness by selling compromised peripherals or infecting commonly used devices.
Potential mitigation strategies include using USB hubs with multiple root controllers to isolate traffic and modifying USB driver behavior to introduce randomized bandwidth allocation. In general, users should avoid untrusted USB devices and physically disconnect unnecessary peripherals when not in use.
The researchers suggest that similar attacks could be extended to other USB peripherals, such as USB security keys or biometric devices, posing further risks to authentication systems. Additionally, they propose investigating congestion-based attacks over wireless protocols like Wi-Fi, which could reveal user activity without even requiring a physical connection.







Leave a Reply