
Cybercriminals leverage newly registered domains to deliver a fresh wave of SpyNote malware through deceptive websites that convincingly mimic Google Play app pages.
The campaign, designed to distribute the potent Android remote access trojan (RAT), is part of an evolving strategy to increase infections and evade detection by leveraging familiar web design and misleading visuals.
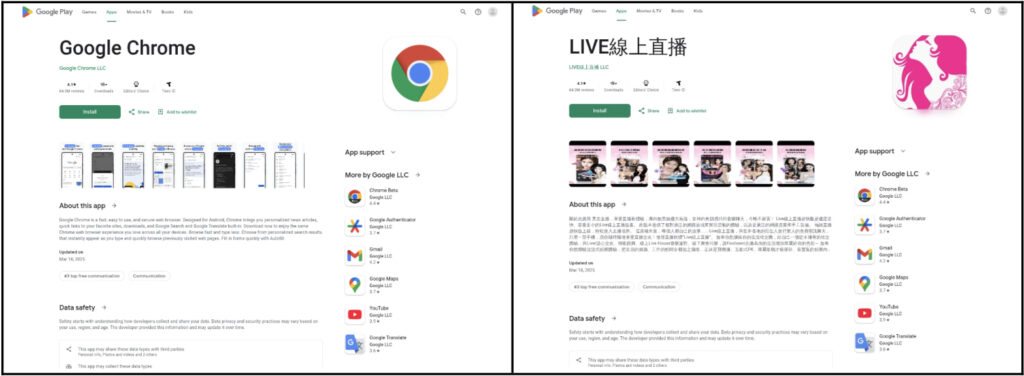
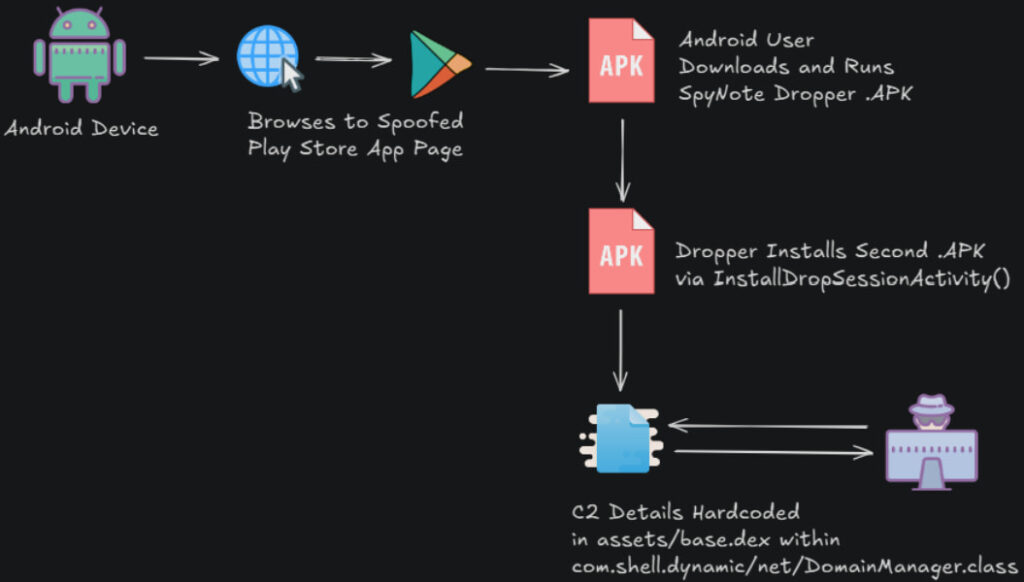
The DomainTools investigation uncovered that the fake app installation pages include an image carousel resembling legitimate Google Play listings, complete with icons and install buttons. When a user clicks the display images, a hidden JavaScript function executes, triggering the download of a malicious APK file. This file is the first stage of a dropper that installs a second APK housing the full SpyNote payload.
DomainTools
DomainTools’ researchers found Chinese-language comments embedded in both the malware and delivery site code and noted that some sites appeared in both English and Chinese, suggesting a potential China-based threat actor. The infrastructure uses domain registration services such as NameSilo and XinNet and relies on hosting providers like Lightnode and Vultr Holdings.
SpyNote, also known to have variants like SpyMax, has been previously linked to APT groups, including OilRig (APT34), APT-C-37 (Pat-Bear), and OilAlpha. It has a notorious history of being used in both targeted espionage and large-scale cybercrime campaigns. According to DomainTools, this version maintains a two-stage architecture, with the base DEX file in the assets folder managing command-and-control (C2) connectivity.
DomainTools
SpyNote is capable of extensive surveillance and control over infected devices. Once installed, it requests a vast range of intrusive permissions, including access to the internet, SMS, call logs, contacts, device admin privileges, and more. Its capabilities include:
- Real-time device tracking and microphone/audio recording
- Stealing 2FA codes from SMS and Google Authenticator
- Taking remote photos or video via the camera
- Injecting overlays for credential theft
- Installing apps silently and locking or wiping the device
- Preventing uninstallation through Accessibility abuse and interface manipulation
Previous SpyNote operations
In November 2024, CYFIRMA uncovered a SpyNote variant posing as Avast Mobile Security, and in mid-2023, Italian firm Cleafy documented a spike in infections across Europe. These earlier campaigns revealed SpyNote’s focus on banking fraud and cryptocurrency theft, and showed its adaptability in impersonating antivirus apps or fake bank updates to trick users.
The accessibility and modularity of SpyNote, especially after its source code leak in late 2022, have contributed to its growing popularity among cybercriminals. Builder tools circulating underground forums allow even less-skilled actors to tailor the malware to specific regions or victim profiles.
To guard against this expanding threat, Android users are strongly advised to only download apps from Google Play, manually review app permissions after installation, and ensure Play Protect is active on your device.







Leave a Reply